A penetration tester is testing a new API for the company's existing services and is preparing the following script:
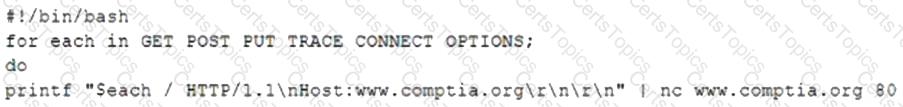
Which of the following would the test discover?
A penetration tester has extracted password hashes from the lsass.exe memory process. Which of the following should the tester perform NEXT to pass the hash and provide persistence with the newly acquired credentials?
During a penetration tester found a web component with no authentication requirements. The web component also allows file uploads and is hosted on one of the target public web the following actions should the penetration tester perform next?
Which of the following factors would a penetration tester most likely consider when testing at a location?