A penetration tester was conducting a penetration test and discovered the network traffic was no longer reaching the client’s IP address. The tester later discovered the SOC had used sinkholing on the penetration tester’s IP address. Which of the following BEST describes what happened?
A penetration tester conducted a discovery scan that generated the following:
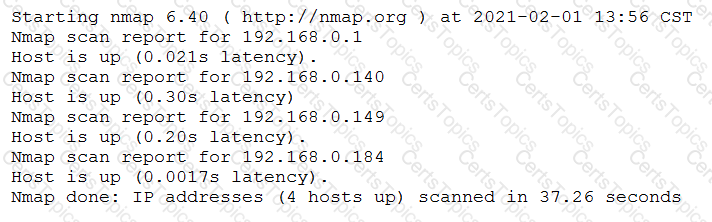
Which of the following commands generated the results above and will transform them into a list of active hosts for further analysis?
A security engineer identified a new server on the network and wants to scan the host to determine if it is running an approved version of Linux and a patched version of Apache. Which of the following commands will accomplish this task?
A penetration tester found the following valid URL while doing a manual assessment of a web application:
Which of the following automated tools would be best to use NEXT to try to identify a vulnerability in this URL?