A physical penetration tester needs to get inside an organization's office and collect sensitive information without acting suspiciously or being noticed by the security guards. The tester has observed that the company's ticket gate does not scan the badges, and employees leave their badges on the table while going to the restroom. Which of the following techniques can the tester use to gain physical access to the office? (Choose two.)
In Python socket programming, SOCK_DGRAM type is:
Which of the following is the most secure method for sending the penetration test report to the client?
A penetration tester writes the following script:
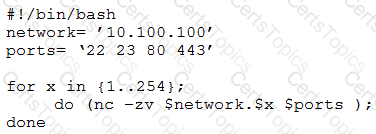
Which of the following is the tester performing?