A penetration tester is looking for a particular type of service and obtains the output below:
I Target is synchronized with 127.127.38.0 (reference clock)
I Alternative Target Interfaces:
I 10.17.4.20
I Private Servers (0)
I Public Servers (0)
I Private Peers (0)
I Public Peers (0)
I Private Clients (2)
I 10.20.8.69 169.254.138.63
I Public Clients (597)
I 4.79.17.248 68.70.72.194 74.247.37.194 99.190.119.152
I 12.10.160.20 68.80.36.133 75.1.39.42 108.7.58.118
I 68.56.205.98
I 2001:1400:0:0:0:0:0:1 2001:16d8:ddOO:38:0:0:0:2
I 2002:db5a:bccd:l:21d:e0ff:feb7:b96f 2002:b6ef:81c4:0:0:1145:59c5:3682
I Other Associations (1)
|_ 127.0.0.1 seen 1949869 times, last tx was unicast v2 mode 7
Which of the following commands was executed by the tester?
Which of the following elements of a penetration testing report aims to provide a normalized and standardized representation of discovered vulnerabilities and the overall threat they present to an affected system or network?
A penetration testing firm wants to hire three additional consultants to support a newly signed long-term contract with a major customer. The following is a summary of candidate
background checks:
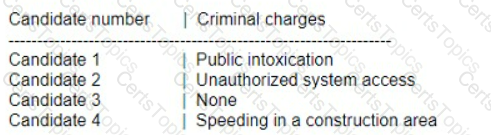
Which of the following candidates should most likely be excluded from consideration?
Which of the following best explains why communication is a vital phase of a penetration test?