CompTIA CAS-004 Exam With Confidence Using Practice Dumps

CAS-004: CompTIA CASP Exam 2025 Study Guide Pdf and Test Engine
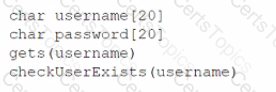
Are you worried about passing the CompTIA CAS-004 (CompTIA SecurityX Certification Exam) exam? Download the most recent CompTIA CAS-004 braindumps with answers that are 100% real. After downloading the CompTIA CAS-004 exam dumps training , you can receive 99 days of free updates, making this website one of the best options to save additional money. In order to help you prepare for the CompTIA CAS-004 exam questions and verified answers by IT certified experts, CertsTopics has put together a complete collection of dumps questions and answers. To help you prepare and pass the CompTIA CAS-004 exam on your first attempt, we have compiled actual exam questions and their answers.
Our (CompTIA SecurityX Certification Exam) Study Materials are designed to meet the needs of thousands of candidates globally. A free sample of the CompTIA CAS-004 test is available at CertsTopics. Before purchasing it, you can also see the CompTIA CAS-004 practice exam demo.