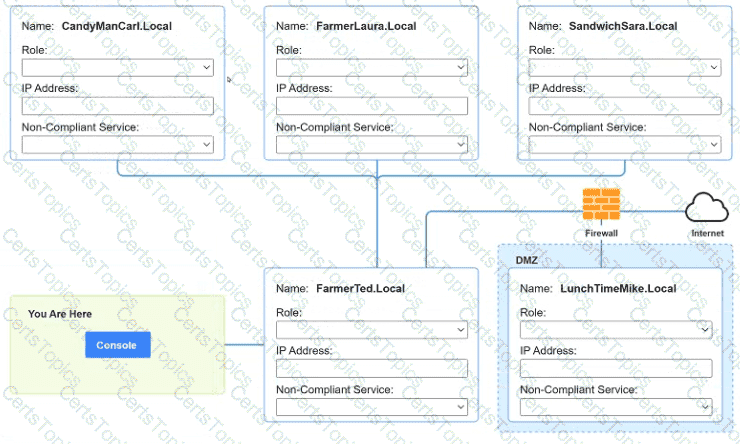
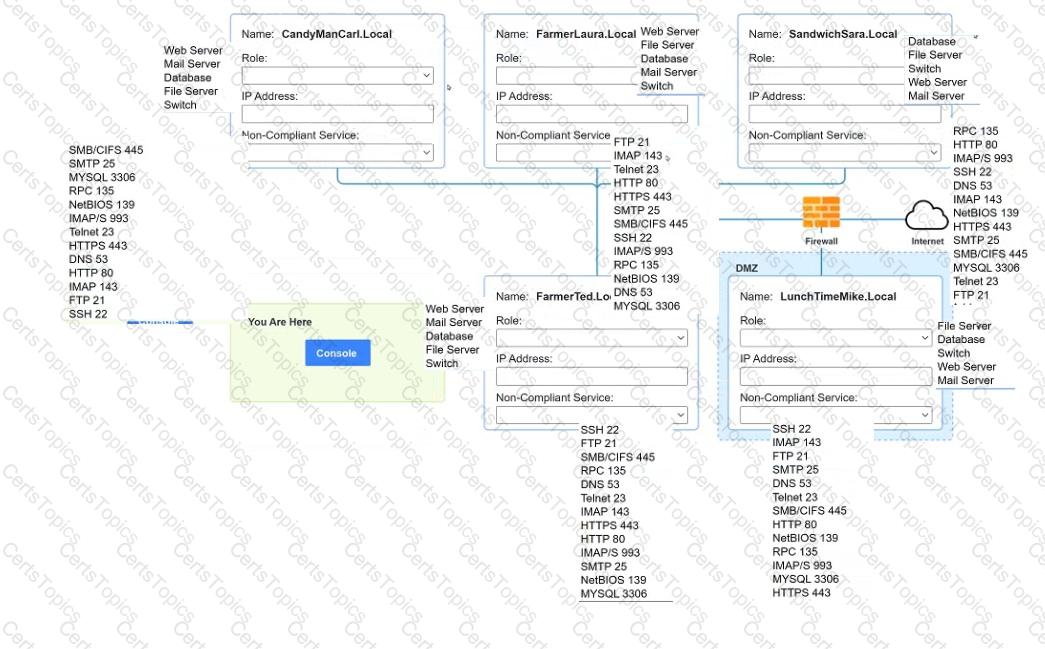
You are a penetration tester who is reviewing the system hardening guidelines for a company. Hardening guidelines indicate the following.
There must be one primary server or service per device.
Only default port should be used
Non- secure protocols should be disabled.
The corporate internet presence should be placed in a protected subnet
Instructions :
Using the available tools, discover devices on the corporate network and the services running on these devices.
You must determine
ip address of each device
The primary server or service each device
The protocols that should be disabled based on the hardening guidelines
A systems administrator is reviewing after-hours traffic flows from data-center servers and sees regular outgoing HTTPS connections from one of the servers to a public IP address. The server should not be making outgoing connections after hours. Looking closer, the administrator sees this traffic pattern around the clock during work hours as well. Which of the following is the most likely explanation?
Which of the following tools would work best to prevent the exposure of PII outside of an organization?
Which of following would best mitigate the effects of a new ransomware attack that was not properly stopped by the company antivirus?