A vulnerability analyst received a list of system vulnerabilities and needs to evaluate the relevant impact of the exploits on the business. Given the constraints of the current sprint, only three can be remediated. Which of the following represents the least impactful risk, given the CVSS3.1 base scores?
A security analyst noticed the following entry on a web server log:
Warning: fopen : failed to open stream:
Connection refused in /hj/var/www/showimage.php on line 7
Which of the following malicious activities was most likely attempted?
A technician identifies a vulnerability on a server and applies a software patch. Which of the following should be the next step in the remediation process?
A security analyst scans a host and generates the following output:
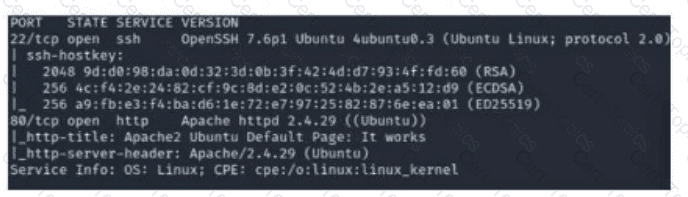
Which of the following best describes the output?