During a security test, a security analyst found a critical application with a buffer overflow vulnerability. Which of the following would be best to mitigate the vulnerability at the application level?
A security analyst is trying to identify anomalies on the network routing. Which of the following functions can the analyst use on a shell script to achieve the objective most accurately?
An analyst needs to provide recommendations based on a recent vulnerability scan:
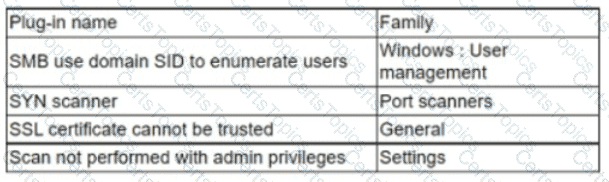
Which of the following should the analyst recommend addressing to ensure potential vulnerabilities are identified?
A Chief Information Security Officer (CISO) has determined through lessons learned and an associated after-action report that staff members who use legacy applications do not adequately understand how to differentiate between non-malicious emails and phishing emails. Which of the following should the CISO include in an action plan to remediate this issue?