A new cybersecurity analyst is tasked with creating an executive briefing on possible threats to the organization. Which of the following will produce the data needed for the briefing?
An organization has tracked several incidents that are listed in the following table:
 Which of the following is the organization's MTTD?
Which of the following is the organization's MTTD?
A Chief Information Security Officer wants to map all the attack vectors that the company faces each day. Which of the following recommendations should the company align their security controls around?
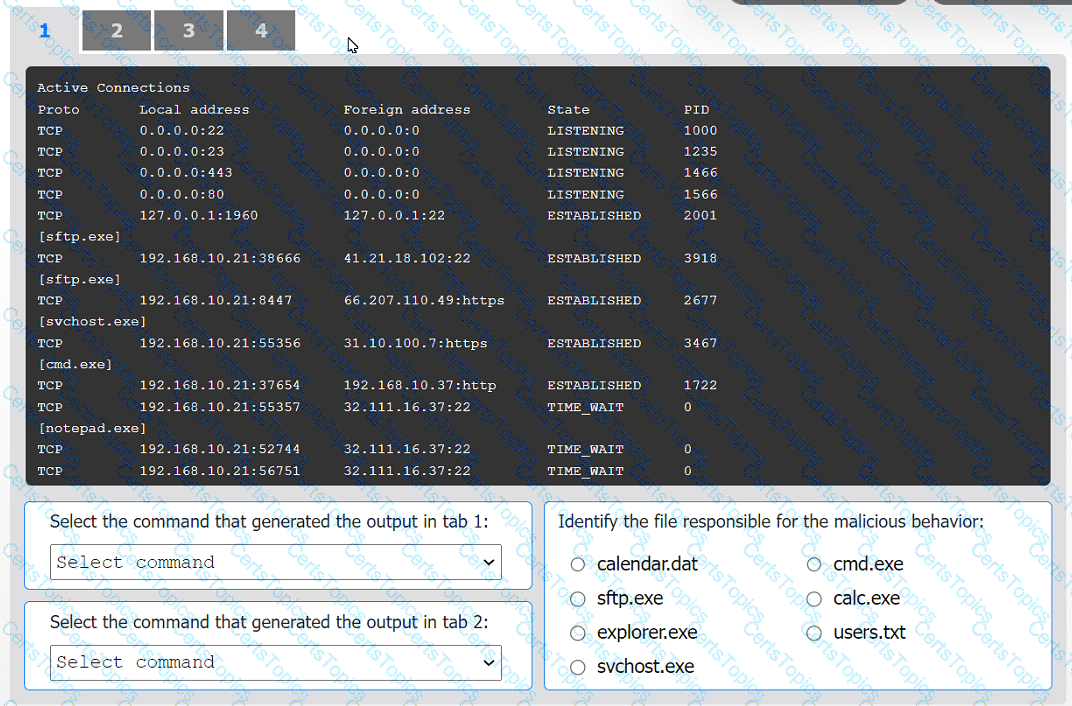
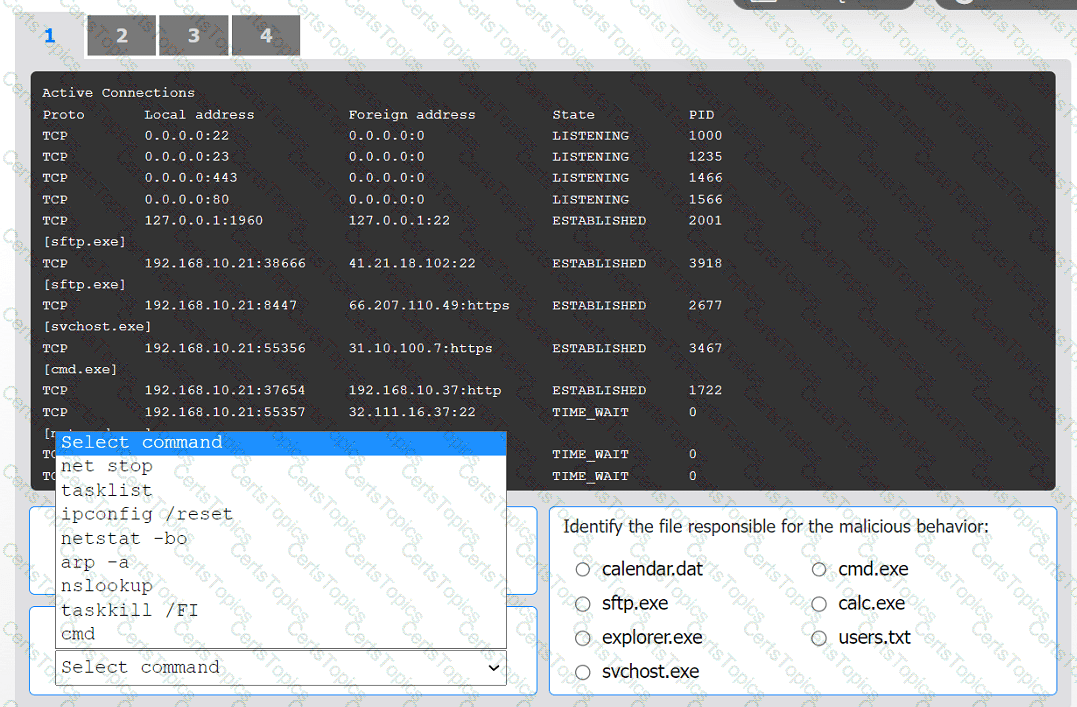
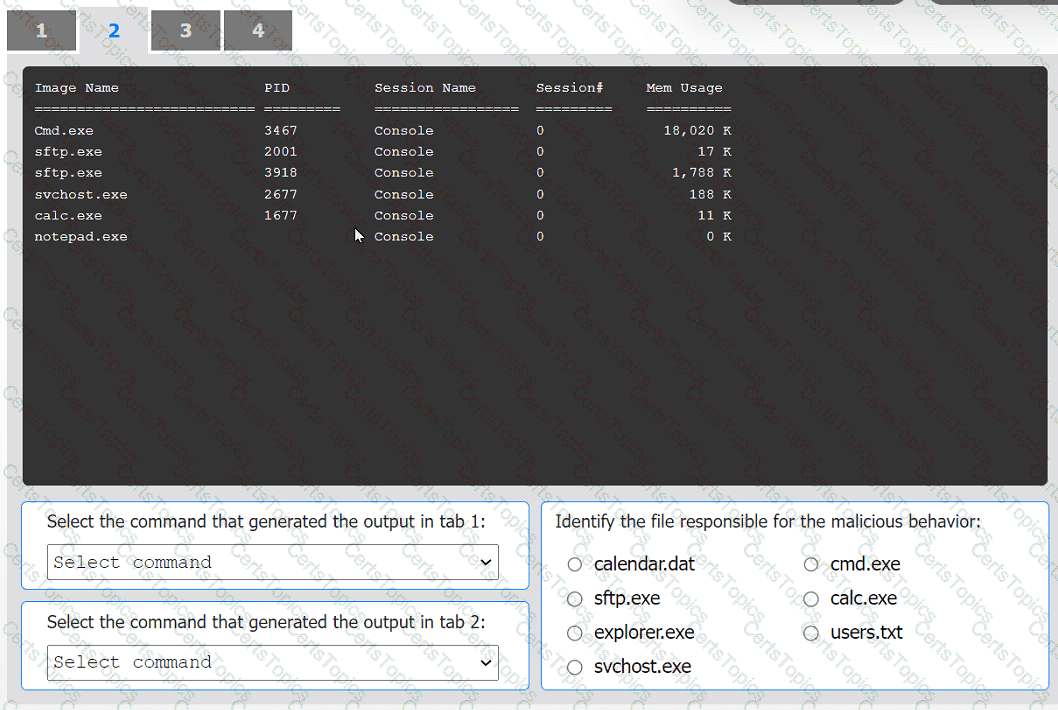
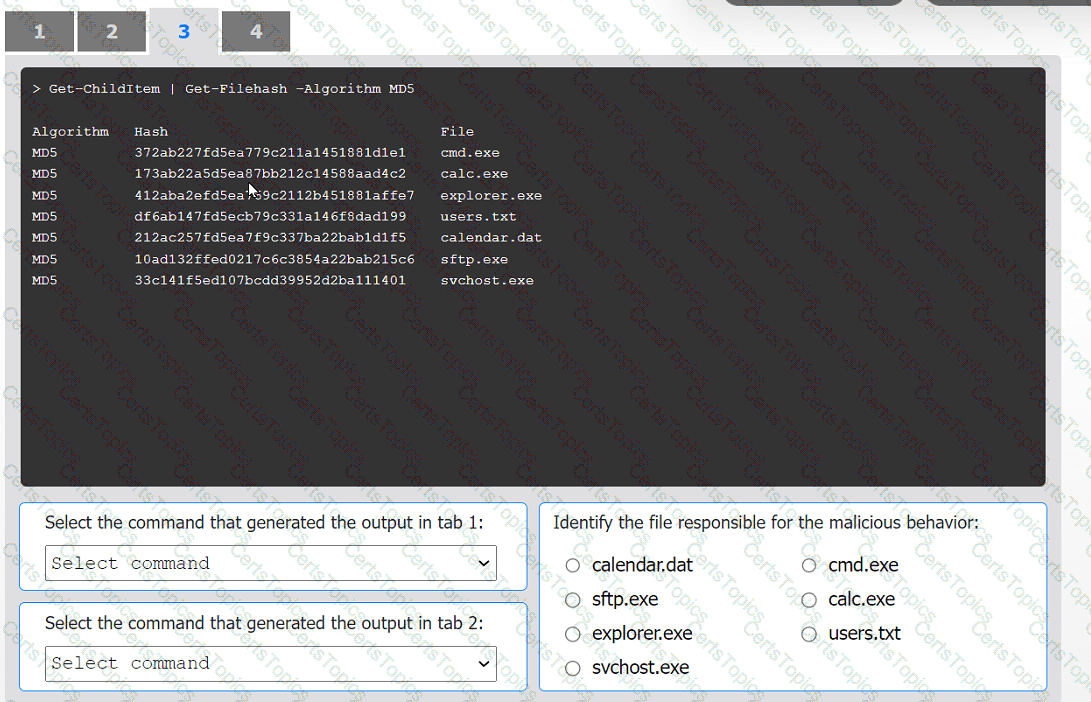
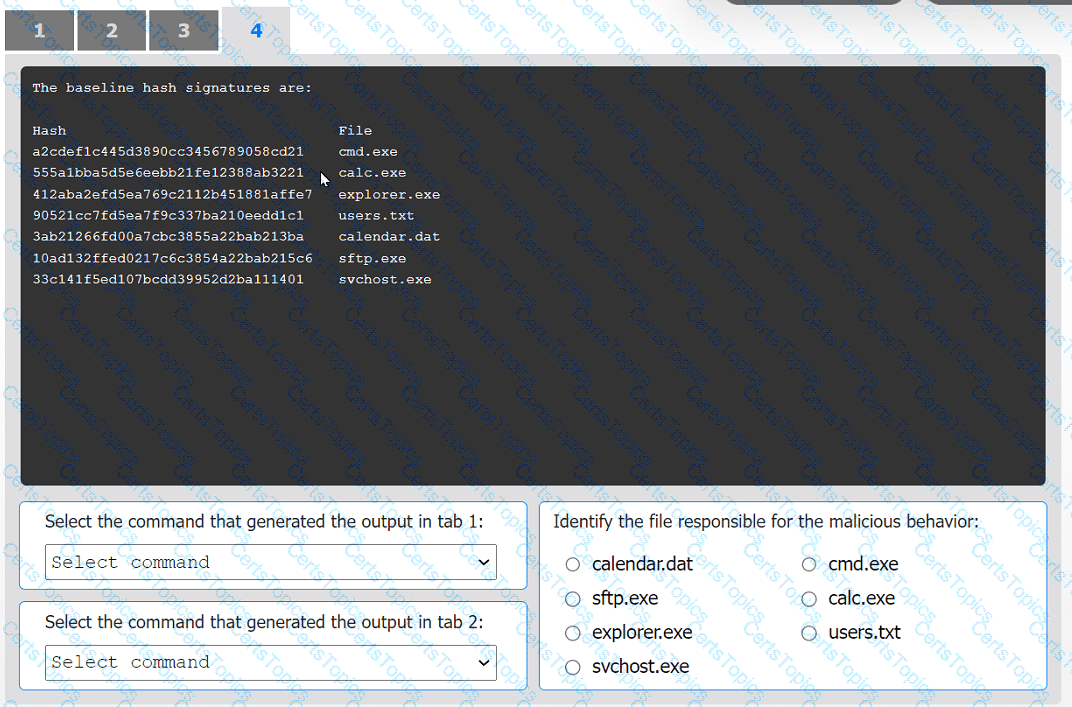
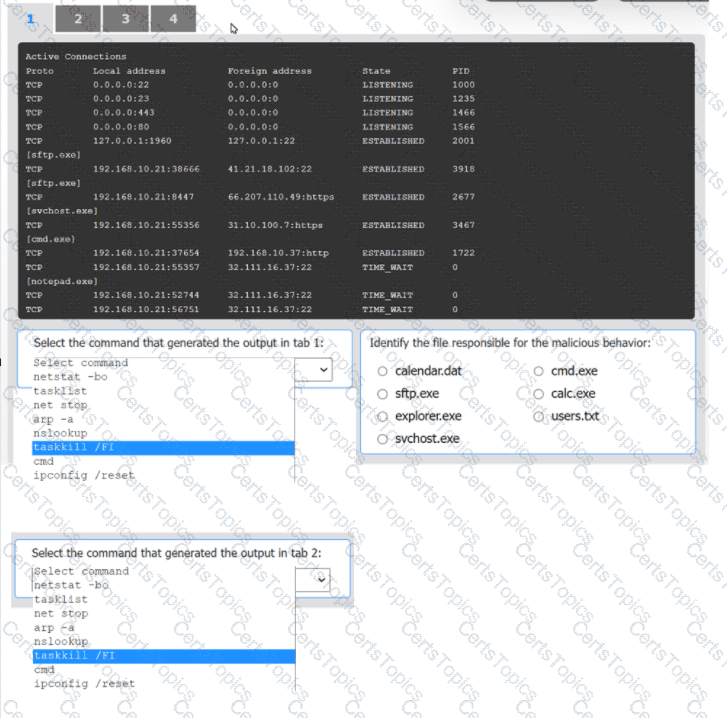
An organization has noticed large amounts of data are being sent out of its network. An
analyst is identifying the cause of the data exfiltration.
INSTRUCTIONS
Select the command that generated the output in tabs 1 and 2.
Review the output text in all tabs and identify the file responsible for the malicious
behavior.
If at any time you would like to bring back the initial state of the simulation, please click
the Reset All button.