A technician is analyzing output from a popular network mapping tool for a PCI audit:
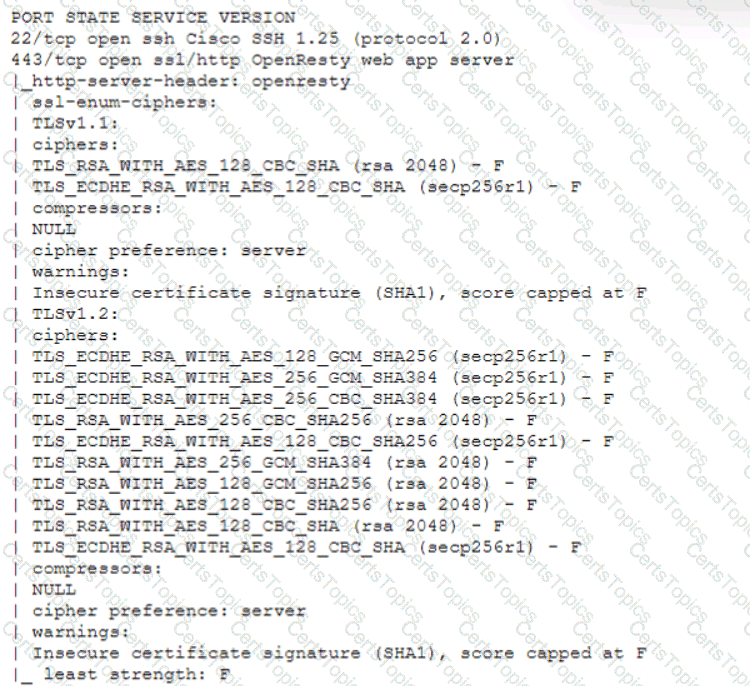
Which of the following best describes the output?
When starting an investigation, which of the following must be done first?
A security analyst needs to develop a solution to protect a high-value asset from an exploit like a recent zero-day attack. Which of the following best describes this risk management strategy?
A security analyst is reviewing events that occurred during a possible compromise. The analyst obtains the following log:

Which of the following is most likely occurring, based on the events in the log?