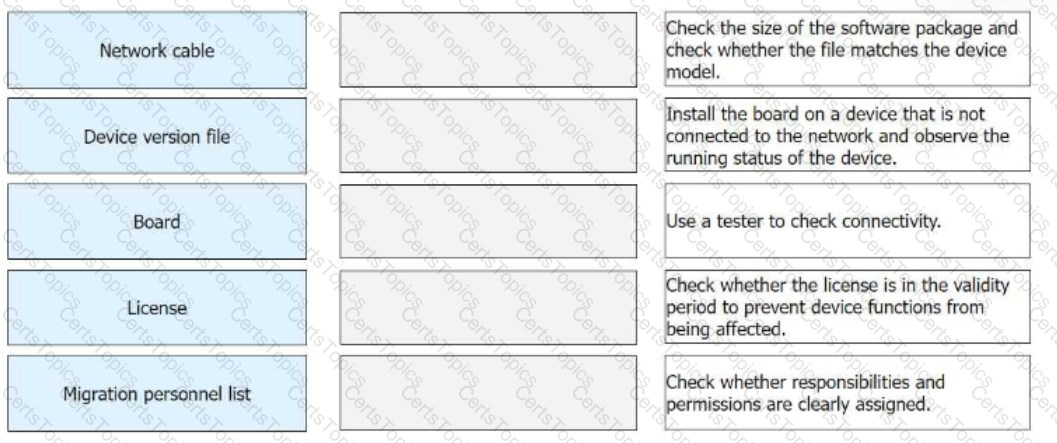
In the preparation phase of a migration project, the software and hardware need to be checked. Match the operation objects in the preparation phase with the corresponding operation contents.
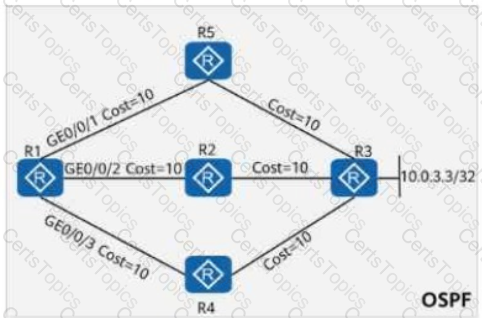
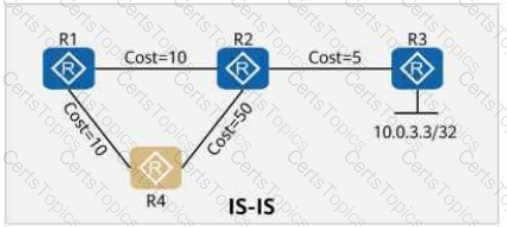
On the OSPF network shown in the figure, the cost values of links are marked. OSPF IP FRR is enabled on R1, and the maximum load-balancing 8 command is configured in the OSPF process. If a service passes through the path R1 → R5 → R3 to reach 10.0.3.3/32, which of the following is the backup outbound interface for the service?
OSPF requires that routers in the same area have the same link state database (LSDB). As the number of routes on the network increases, some routers cannot carry so much routing information due to limited system resources. This state is called database overflow. If the Isdb-overflow-limit number 7 command is run on all routers on an OSPF network, which of the following conditions are likely to cause routers to enter the overflow state?
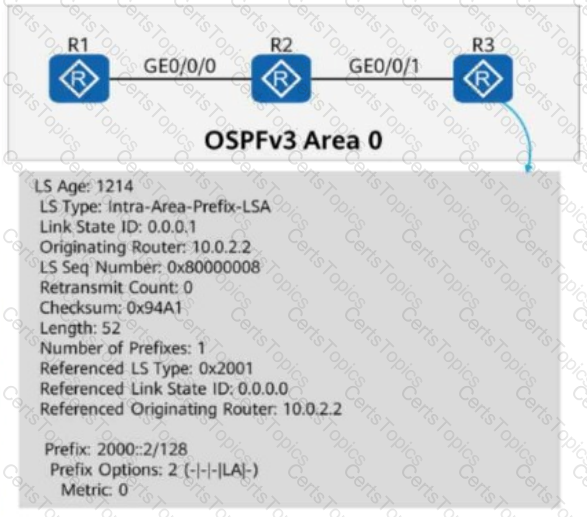
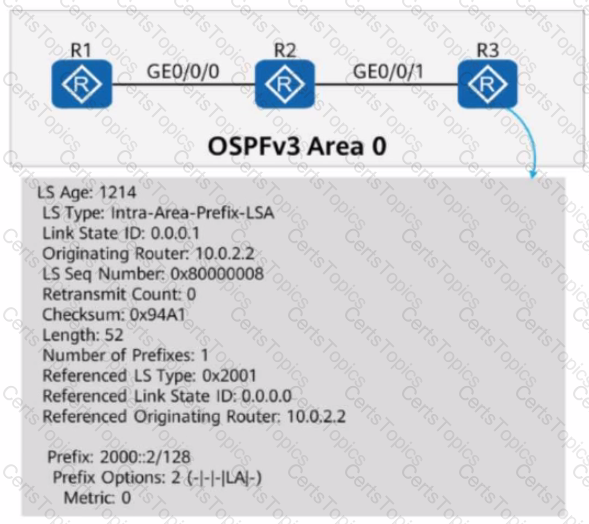
On the OSPFv3 network shown in the figure:
OSPFv3 is enabled on the interfaces connecting R1, R2, and R3.
The router ID of each router is 10.0.X.X, where X is the number of the router.
If you check detailed information about an LSA on R3, the command output shows that the LSA is generated by R2 and describes the IPv6 prefix address associated with the Router-LSA.
Is this statement TRUE or FALSE?
To support the processing and calculation of IPv6 routes, IS-IS adds a new NLPID to TLV 129. The NLPID is an 8-bit field that identifies network layer protocol packets. Which of the following is the NLPID of IPv6?
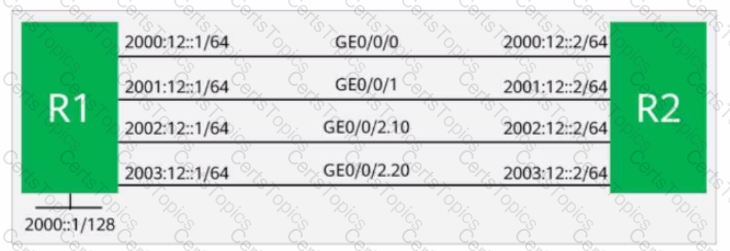
R1 and R2 use directly connected interfaces to establish an EBGP peer relationship. R1 imports 2000:: 1/128 to BGR By default, which of the following is the next hop of the route from R2 to 2000:: 1/128?
As shown in the figure, an administrator enables port isolation on the switch’s interfaces connected to terminals.
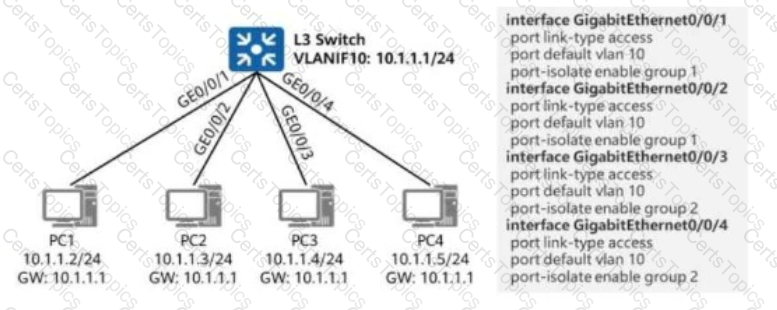
In this scenario, which of the following IP addresses cannot be pinged from PC1?
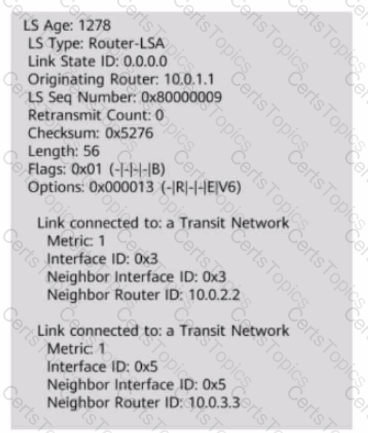
The figure shows the Router-LSA generated by a router. Which of the following statements are true based on the LSA?
On the OSPFv3 network shown in the figure, OSPFv3 is enabled on the interfaces connecting R1, R2, and R3. The router ID of each router is 10.0.X.X, where X is the number of the router. If you check detailed information about an LSA on R3, the command output shows that the LSA is generated by R2 and describes the IPv6 prefix address associated with the Router-LSA.
On the network shown in the figure, EBGP peer relationships are established between neighboring routers through directly connected interfaces.
The router ID of each router is 10.0.X.X, and the AS number is 6500X, where X is the number of the router.
Both R1 and R4 have static routes to 192.168.1.0/24, which are imported to BGP through the import-route command.
The aggregate 192.168.1.0/16 detail-suppressed command is configured on R2.
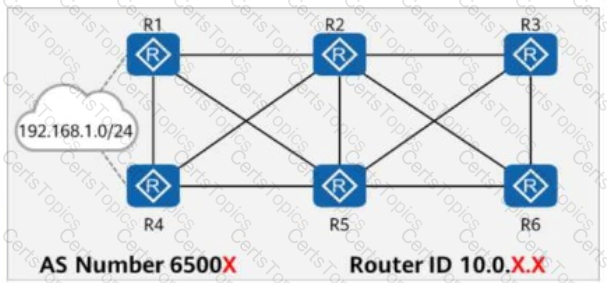
Which of the following is the path for traffic from R3 to 192.168.1.0/24?
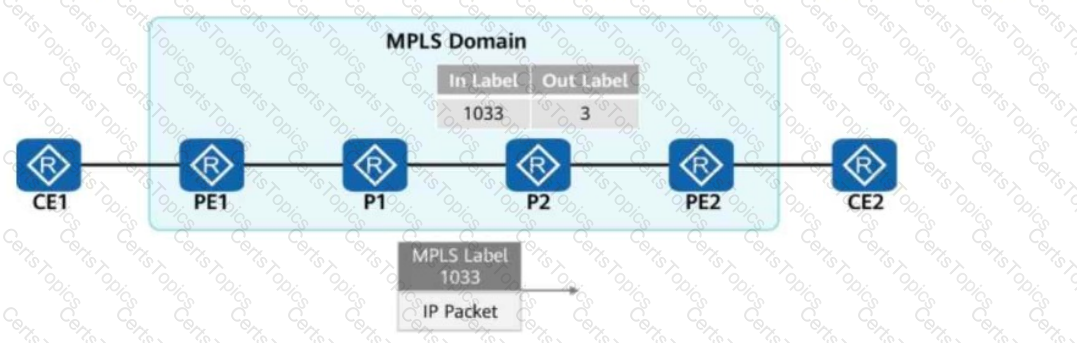
MPLS can carry multiple network protocol services, including unicast IPv4 services, multicast IPv4 services, unicast IPv6 services, and multicast IPv6 services.
In the figure, packets are forwarded based on MPLS on the network.
When PE2 receives a packet from P2, what is the label value carried in the packet?
Options:
On the OSPFv3 network shown in the figure:
OSPFv3 is enabled on the interfaces connecting R1, R2, and R3.
The router ID of each router is 10.0.X.X, where X is the number of the router.
When checking detailed information about an LSA on R3, the command output shows that the LSA is generated by R2 and describes the IPv6 prefix address associated with the Network-LSA.
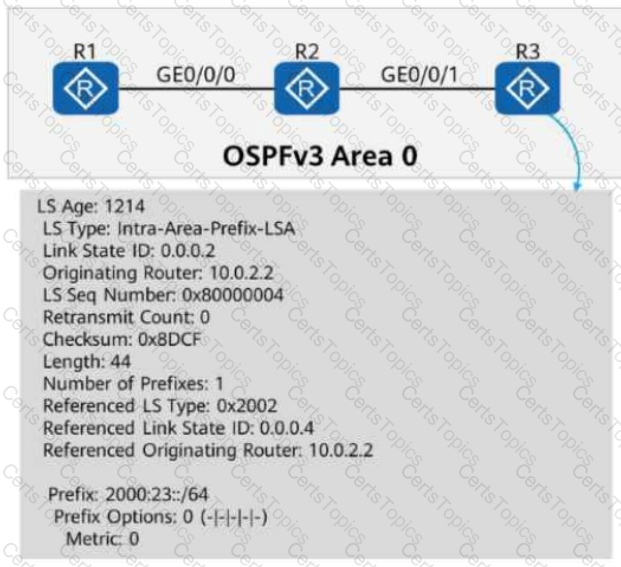
Based on this information, which of the following statements is correct?
MPLS supports nesting of multiple labels. After receiving an MPLS packet, a device first processes the label next to the Layer 2 header, that is, the top MPLS label.
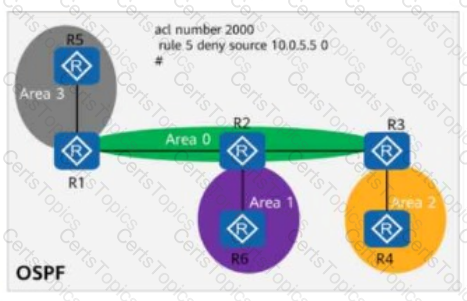
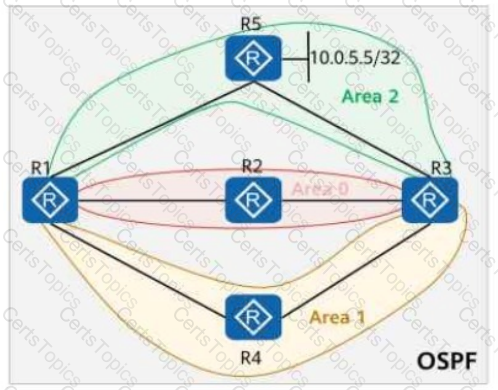
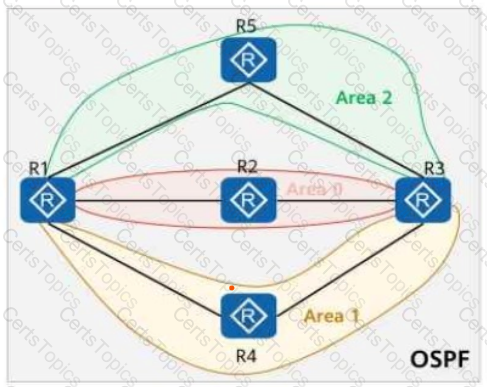
On the OSPF network shown in the figure, areas 1, 2, and 3 are common areas. The IP address of Loopback0 on R5 is 10.0.5.5/32, and OSPF is enabled on the interface using the network command.
ACL 2000 (with the matching rule shown in the figure) is configured on all routers. If the command filter 2000 import is run in area 0 (where R1, R2, and R3 reside), which of the following routers do not have the route 10.0.5.5/32 in their routing tables?
On the network shown in the figure, single-hop BFD is configured on R1 and R2.
A network engineer finds that the BFD session goes down. To locate the fault, the network engineer queries the BFD configurations on R1 and R2.
According to the configuration information marked in the figure, it can be determined that mismatched time parameter settings on R1 and R2 cause the BFD session to go down.

Is this statement TRUE or FALSE?
On the network shown in the figure, the DHCP server function is enabled on GE0/0/0 of R2, and the address pool is an interface address pool.
When GE0/0/0 and GE0/0/1 of R1 function as DHCP clients, only one interface can obtain an IP address by default.
Options:
VLAN aggregation is configured on a switched network. Sub-VLAN 2 and Sub-VLAN 3 are added to Super-VLAN 10.
To enable hosts in different Sub-VLANs to communicate with each other, run the _____ inter-sub-vlan-proxy enable command in the view of VLANIF 10, corresponding to the Super-VLAN.
(Enter the answer in lowercase letters only.)
On the OSPF network shown in the figure, area 1 and area 2 are common areas. The IP address of Loopback0 on R5 is 10.0.5.5/32, and OSPF is enabled on this interface. If the abr-summary 10.0.5.0 255.255.255.0 command is run in area 2 (where R1 resides), which of the following routers have the route 10.0.5.0/24 in their routing tables?
On an enterprise network shown in the figure, EBGP is deployed between CEs and PEs.
CE1 sends a VPN route to PE1.

Which of the following statements are false?
Options:
On the OSPF network shown in the figure, the cost values of links are marked. IS-IS Auto FRR is enabled on R1. The primary path from R1 to 10.0.3.3/32 is R1 → R2 → R3, and the backup path is R1 → R4 → R2 → R3.
Is this statement TRUE or FALSE?
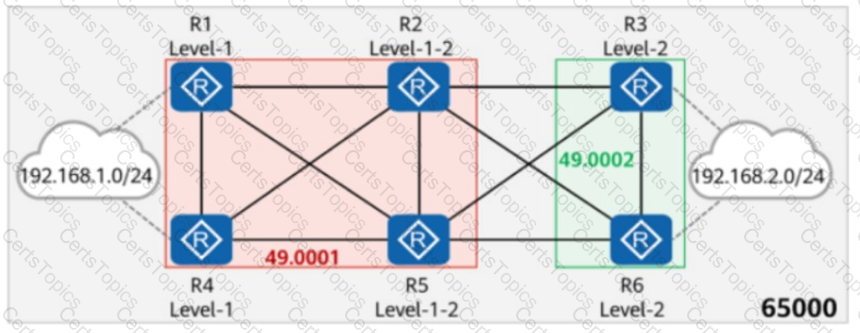
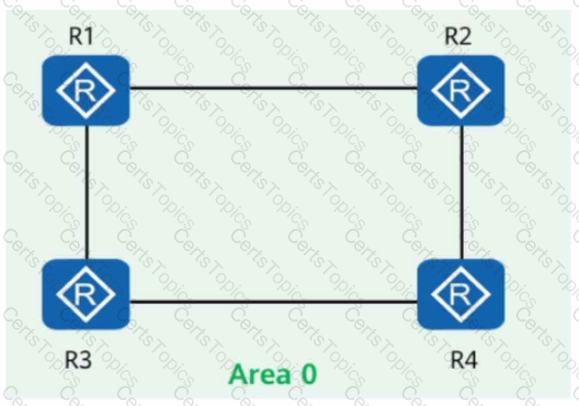
On the network shown in the figure, IS-IS runs on R1, R2, R4, and R5, and the area ID is 49.0001. IS-IS runs on R3 and R6, and the area ID is 49.0002. In AS 65000, R1, R3, R4, and R6 each establish iBGP peer relationships with R2 and R5. R2 and R5 are RRs (Route Reflectors), and R1, R4, R3, and R6 are clients. The iBGP peer relationships are established using Loopback0 on each router, and the router ID is 10.0.0.X/32, where X is the number of the router. R1 and R4 import the external route 192.168.1.0/24 to BGP through the import-route command, and R3 and R6 import the external route 192.168.2.0/24 to BGP through the import-route command. Which of the following statements are true?
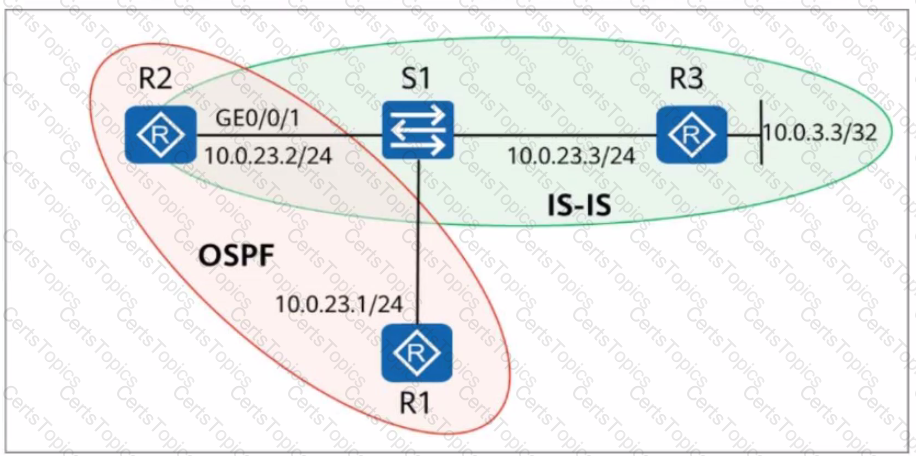
On the network shown in the figure, OSPF is deployed on R1 and R2. IS-IS is deployed on R2 and R3. To enable R1 to obtain the route to 10.0.3.3/32, ISIS routes are imported into OSPF on R2. In this case, the next hop address to 10.0.3.3/32 in the routing table of R1 is_____.
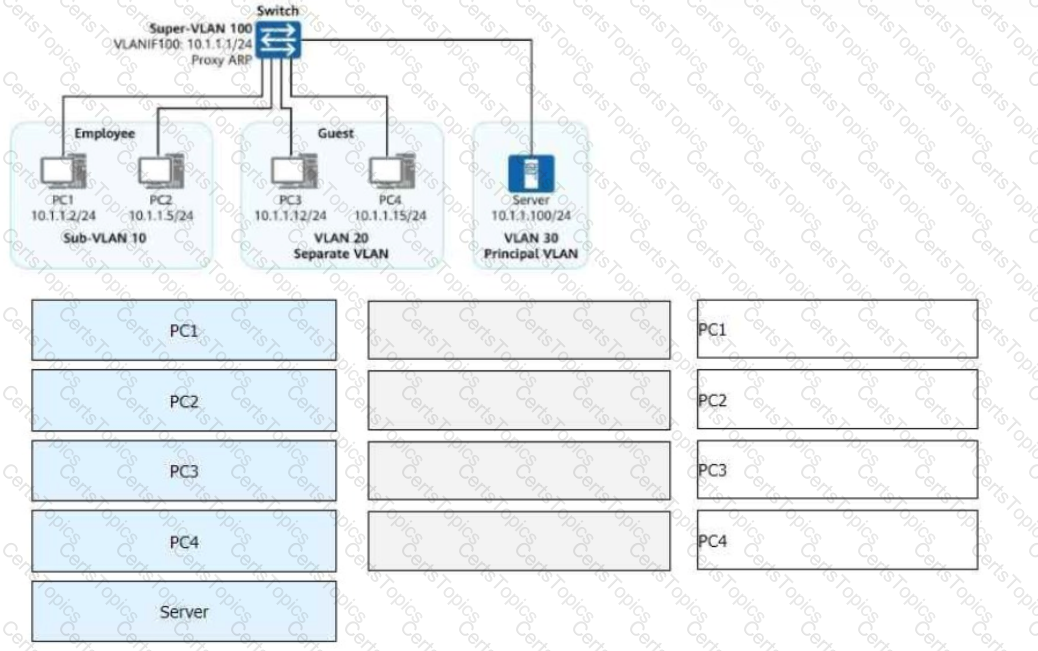
Both VLAN aggregation and MUX VLAN are deployed on the enterprise network shown in the figure.
All switch interfaces connected to terminals are access interfaces.
Given this, match PC1 to PC4 with the hosts or servers they can access on the network.
(Note: A host cannot be matched with itself. For example, PC1 cannot match PC1. Tokens can be reused.)
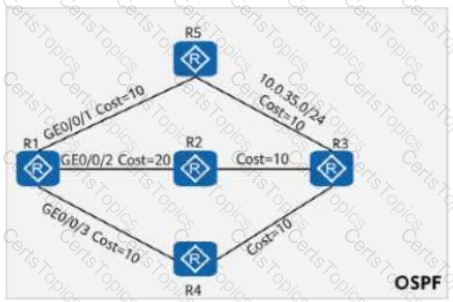
On the OSPF network shown in the figure, the cost values of links are marked. OSPF IP FRR is enabled on R1, and the maximum load-balancing 8 command is configured in the OSPF process. Which of the following is the cost value of the route 10.0.35.0/24 in the routing table of R1?
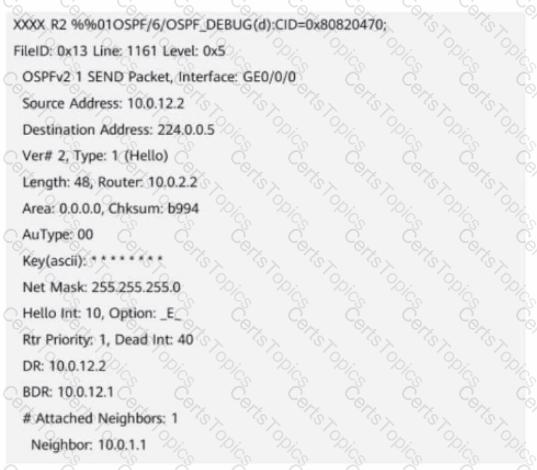
The figure shows the debugging information on an OSPF router. Which of the following is the router ID of this router?
When configuring port security on a switch, the administrator also enables static MAC address flapping detection. If static MAC address flapping occurs, the switch takes the configured action to protect the interface.
Match the names of interface security protection actions with corresponding operations.

After port isolation is configured on a switch, hosts in the same VLAN cannot communicate with each other at Layer 2 or Layer 3 by default.
An administrator runs the display mpls lsp command to view LSPs on a device. The command output is shown in the figure.

Which of the following statements is true?
Options:
I-SPF and PRC can speed up ISIS route convergence. PRC does not calculate nodes. Instead, it updates routes based on the shortest path tree (SPT) calculated using the SPF algorithm.
In the figure, an administrator needs to enable MPLS LDP on R1 to R4. Which of the following configurations of R1 is correct?

On the OSPF network shown in the figure, a network engineer finds that R1 and R2 have the same router ID, and both have imported default routes (with the default-route-advertise always command configured). Given this, which of the following statements is false?
A network engineer checks LLDP neighbor information on R1. The output is shown below.
Which of the following statements are true?
LLDP Output:
yaml
CopyEdit
------------------------------------------------
GE0/0/0 has 1 neighbor(s):
Neighbor index: 1
Chassis type: MAC Address
Chassis ID: faed-ad04-0010
Port ID subtype: Interface Name
Port ID: GE0/0/0
System name: R2
System description: Huawei YunShan OS
Version 1.22.01 (AR8000 V100R002C200)
Copyright (C) 2021-2022 Huawei Technologies Co., Ltd.
HUAWEI AR8140-12G10XG
System capabilities supported: bridge router
System capabilities enabled: bridge router
Management address type: IPv4
Management address: 192.168.1.1
Expired time: 107s
On the OSPF network shown in the figure, area 1 is an NSSA, area 2 is a common area, and R4 imports an external route 10.0.4.4/32. The router ID of each router is 10.0.X.X, where X is the router number. If the asbr-summary 10.0.4.0 255.255.255.0 command is run in the OSPF processes of R1 and R3, which of the following routers have the route 10.0.4.0/24 in their routing tables?
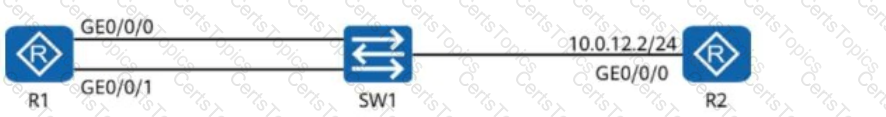
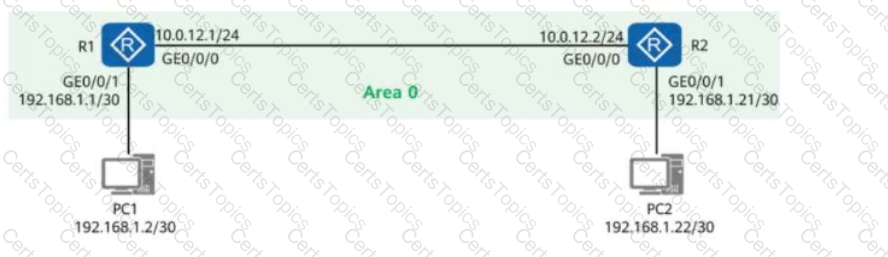
A network engineer provides a troubleshooting report after rectifying a fault. The actual network is simplified into the one shown in the figure, where:
R1 and R2 both have OSPF enabled.
R1 and R2 function as the gateways for PC1 and PC2, respectively.
Given this, which of the following statements are true?
Options:
To protect a device against the attacks of forged BGP messages, you can configure GTSM to check whether the TTL value in the IP message header is within the specified range. If the peer x.x.x.x valid-ttl-hops 100 command is configured on a device, the valid TTL value range of the detected message is [155, 255].
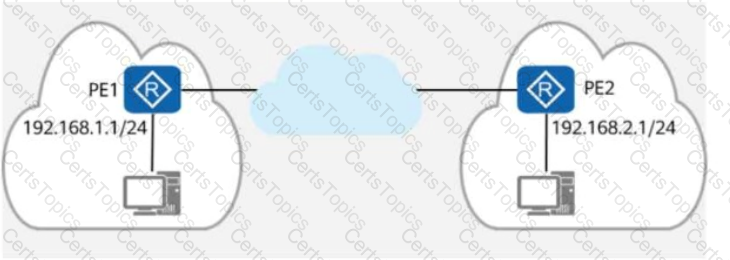
The figure shows the logical network architecture of a migration project. The purpose of the migration is to enable terminals in different geographical locations to communicate with each other and deploy the gateway of the terminals on the PE routers.
After the migration is complete, which of the following methods can be used by network engineers to preliminarily check the network connectivity?
Options:
In the figure, the company wants to ensure secure communication between the headquarters and branch, and isolate the R&D areas from non-R&D areas, without changing the current network deployment.
To meet this requirement, an administrator deploys BGP/MPLS IP VPN on the network.
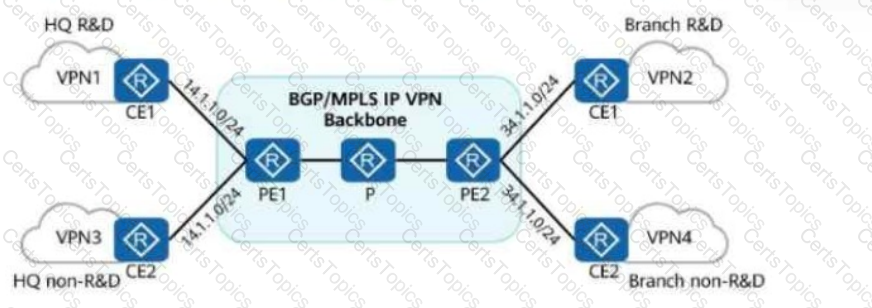
Which of the following statements are true?
On the ISIS network shown in the figure, R1 imports a default route using the default-route-advertise always level-1 command. In this case, R3 can learn this default route through IS-IS.