Which of the following tools would be the best to use to intercept an HTTP response of an API, change its content, and forward it back to the origin mobile device?
During an assessment, a penetration tester was able Jo get access on all target servers by attempting authentication using a service account key that was published on the intranet site as part of a standard procedure. Which of the following should the penetration tester recommend for this type of finding?
During an assessment of a web application, a penetration tester would like to test the application for blind SQL injection. Which of the following techniques should the penetration tester perform next?
A penetration tester is hired to test a client’s systems. The client's systems are hosted by the client at its headquarters. The production environment is hosted by a private cloud-hosting company. Which of the following would be the most important for the penetration tester to determine before beginning the test?
A vulnerability assessor is looking to establish a baseline of all IPv4 network traffic on the local VLAN without a local IP address. Which of the following Nmap command sequences would best provide this information?
A penetration tester wants to crack MD5 hashes more quickly. The tester knows that the first part of the password is Winter followed by four digits and a special character at the end. Which of the following commands should the tester use?
A security consultant wants to perform a vulnerability assessment with an application that can effortlessly generate an easy-to-read report. Which of the following should the attacker use?
During a security assessment, a penetration tester decides to implement a simple TCP port scanner to check the open ports from 1000 to 2000. Which of the following Python scripts would achieve this task?
Which of the following describes how a penetration tester could prioritize findings in a report?
Which of the following is the most common vulnerability associated with loT devices that are directly connected to the internet?
A security analyst is conducting an unknown environment test from 192.168 3.3. The analyst wants to limit observation of the penetration tester's activities and lower the probability of detection by intrusion protection and detection systems. Which of the following Nmap commands should the analyst use to achieve This objective?
In a standard engagement, a post-report document is provided outside of the report. This document:
• Does not contain specific findings
• Exposes vulnerabilities
• Can be shared publicly with outside parties that do not have an in-depth understanding about the client's network
Which of the following documents is described?
Given the following user-supplied data:
AND 1=1
Which of the following attack techniques is the penetration tester likely implementing?
A penetration tester enters a command into the shell and receives the following output:
C:\Users\UserX\Desktop>vmic service get name, pathname, displayname, startmode | findstr /i auto | findstr /i /v |C:\\Windows\\" I findstr /i /v""
VulnerableService Some Vulnerable Service C:\Program Files\A Subfolder\B Subfolder\SomeExecutable.exe Automatic
Which of the following types of vulnerabilities does this system contain?
A penetration tester managed to exploit a vulnerability using the following payload:
IF (1=1) WAIT FOR DELAY '0:0:15'
Which of the following actions would best mitigate this type ol attack?
A penetration tester is performing an assessment of an application that allows users to upload documents to a cloud-based file server for easy access anywhere in the world. Which of the following would most likely allow a tester to access unintentionally exposed documents?
A penetration tester is performing an assessment for an application that is used by large organizations operating in the heavily regulated financial services industry. The penetration tester observes that the default Admin User account is enabled and appears to be used several times a day by unfamiliar IP addresses. Which of the following is the most appropriate way to remediate this issue?
During a REST API security assessment, a penetration tester was able to sniff JSON content containing user credentials. The JSON structure was as follows:
<
transaction_id: "1234S6", content: [ {
user_id: "mrcrowley", password: ["€54321#"] b <
user_id: "ozzy",
password: ["1112228"] ) ]
Assuming that the variable json contains the parsed JSON data, which of the following Python code snippets correctly returns the password for the user ozzy?
A penetration tester is performing a social engineering penetration test and was able to create a remote session. Which of the following social engineering techniques was most likely successful?
During an assessment, a penetration tester needs to perform a cloud asset discovery of an organization. Which of the following tools would most likely provide more accurate results in this situation?
Which of the following is the most important aspect to consider when calculating the price of a penetration test service for a client?
An organization's Chief Information Security Officer debates the validity of a critical finding from a penetration assessment that was completed six months ago. Which of the following post-report delivery activities would have most likely prevented this scenario?
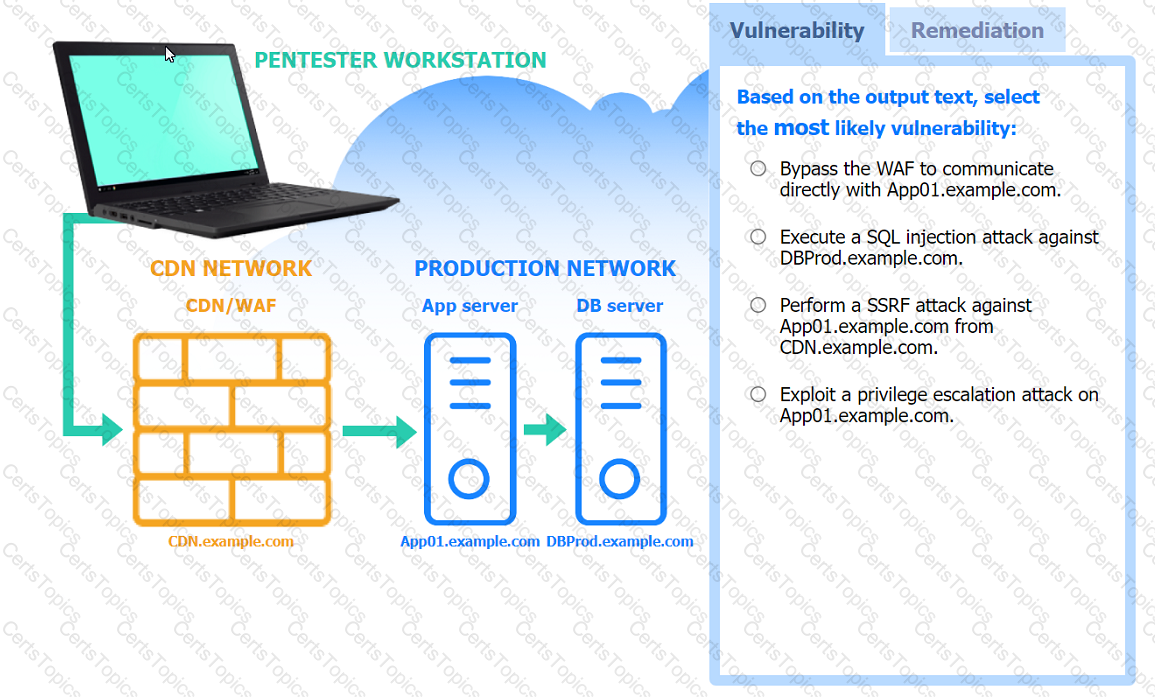
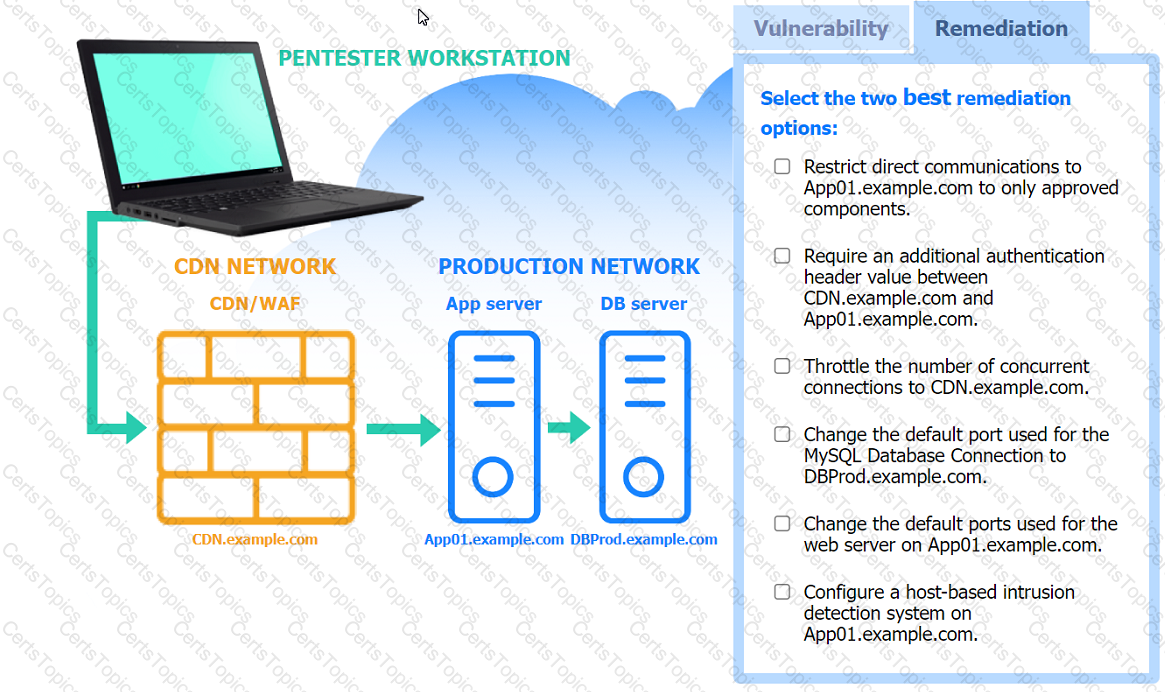
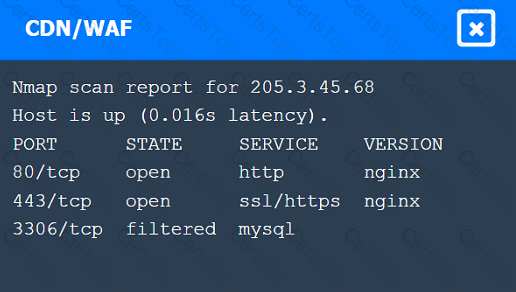
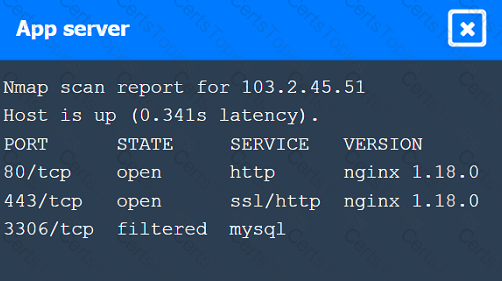
A penetration tester performs several Nmap scans against the web application for a client.
INSTRUCTIONS
Click on the WAF and servers to review the results of the Nmap scans. Then click on
each tab to select the appropriate vulnerability and remediation options.
If at any time you would like to bring back the initial state of the simulation, please
click the Reset All button.
In Java and C/C++, variable initialization is critical because:
A penetration tester is performing DNS reconnaissance and has obtained the following output using different dig comrr
;; ANSWER SECTION
company.com.5INMX10 mxa.company.com
company.com.5IN-MX10 mxb.company.com
company.com.5INMX100 mxc.company.com
;; ANSWER SECTION company.com.5INA120.73.220.53
;; ANSWER SECTION company.com.5INNSnsl.nsvr.com
Which of the following can be concluded from the output the penetration tester obtained?
Given the following code:
$p = (80, 110, 25)
$network = (192.168.0)
$range = 1 .. 254
$ErrorActionPreference = 'silentlycontinue'
$Foreach ($add in $range)
$Foreach ($x in $p)
{ {$ip = "{0} . {1} -F $network, $add"
If (Test-Connection -BufferSize 32 -Count 1 -quiet -ComputerName $ip)
{$socket = new-object System.Net. Sockets. TcpClient (&ip, $x)
If ($socket. Connected) { $ip $p open"
$socket. Close () }
}
}}
Which of the following tasks could be accomplished with the script?
A penetration tester is performing an assessment for an organization and must gather valid user credentials. Which of the following attacks would be best for the tester to use to achieve this objective?
A penetration tester is working to enumerate the PLC devices on the 10.88.88.76/24 network. Which of the following commands should the tester use to achieve the objective in a way that minimizes the risk of affecting the PLCs?
Penetration on an assessment for a client organization, a penetration tester notices numerous outdated software package versions were installed ...s-critical servers. Which of the following would best mitigate this issue?
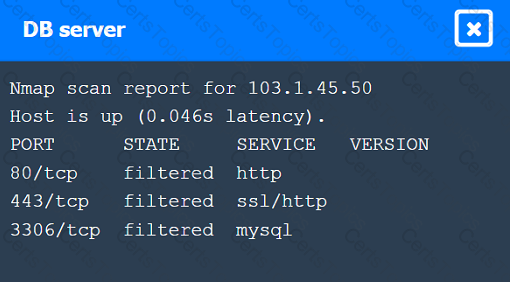
A penetration tester executes the following Nmap command and obtains the following output:
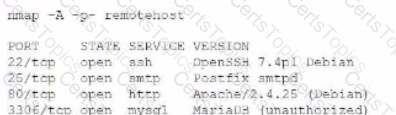
Which of the following commands would best help the penetration tester discover an exploitable service?
A)
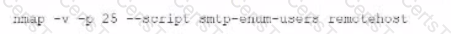
B)
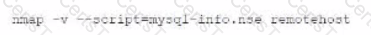
C)
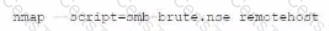
D)
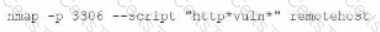
During a penetration test of a server application, a security consultant found that the application randomly crashed or remained stable after opening several simultaneous connections to the application and always submitting the same packets of data. Which of the following is the best sequence of steps the tester should use to understand and exploit the vulnerability?
A penetration tester wants to find the password for any account in the domain without locking any of the accounts. Which of the following commands should the tester use?
Given the following Nmap scan command:
[root@kali ~]# nmap 192.168.0 .* -- exclude 192.168.0.101
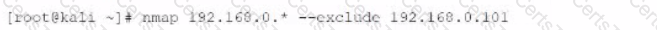
Which of the following is the total number of servers that Nmap will attempt to scan?
A penetration tester is looking for a particular type of service and obtains the output below:
I Target is synchronized with 127.127.38.0 (reference clock)
I Alternative Target Interfaces:
I 10.17.4.20
I Private Servers (0)
I Public Servers (0)
I Private Peers (0)
I Public Peers (0)
I Private Clients (2)
I 10.20.8.69 169.254.138.63
I Public Clients (597)
I 4.79.17.248 68.70.72.194 74.247.37.194 99.190.119.152
I 12.10.160.20 68.80.36.133 75.1.39.42 108.7.58.118
I 68.56.205.98
I 2001:1400:0:0:0:0:0:1 2001:16d8:ddOO:38:0:0:0:2
I 2002:db5a:bccd:l:21d:e0ff:feb7:b96f 2002:b6ef:81c4:0:0:1145:59c5:3682
I Other Associations (1)
|_ 127.0.0.1 seen 1949869 times, last tx was unicast v2 mode 7
Which of the following commands was executed by the tester?
Which of the following elements of a penetration testing report aims to provide a normalized and standardized representation of discovered vulnerabilities and the overall threat they present to an affected system or network?
A penetration testing firm wants to hire three additional consultants to support a newly signed long-term contract with a major customer. The following is a summary of candidate
background checks:
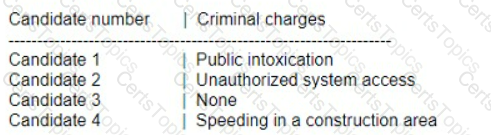
Which of the following candidates should most likely be excluded from consideration?
Which of the following best explains why communication is a vital phase of a penetration test?
A penetration tester wants to perform a SQL injection test. Which of the following characters should the tester use to start the SQL injection attempt?
bash
Copy code
for ip in $(seq 1 254);
do echo $(echo "192.168.15.$ip ") $(host 192.168.15.$ip dns.company.com | grep "domain name pointer")
done | grep "domain name pointer" | cut -d" " -f1,6
Which of the following best explains the purpose of this script?
A penetration tester is preparing a credential stuffing attack against a company's website. Which of the following can be used to passively get the most relevant information?
Which of the following is the most secure way to protect a final report file when delivering the report to the client/customer?
A penetration tester gained access to one of the target company's servers. During the enumeration phase, the penetration tester lists the bash history and observes the following row:
Which of the following steps should the penetration tester take next?
An external consulting firm is hired to perform a penetration test and must keep the confidentiality of the security vulnerabilities and the private data found in a customer's systems. Which of the following documents addresses this requirement?
During a web application test, a penetration tester was able to navigate to and view all links on the web page. After manually reviewing the pages, the tester used a web scanner to automate the search for vulnerabilities. When returning to the web application, the following message appeared in the browser: unauthorized to view this page. Which of the following BEST explains what occurred?
During an assessment, a penetration tester gathered OSINT for one of the IT systems administrators from the target company and managed to obtain valuable information, including corporate email addresses. Which of the following techniques should the penetration tester perform NEXT?
A penetration tester was contracted to test a proprietary application for buffer overflow vulnerabilities. Which of the following tools would be BEST suited for this task?
Company.com has hired a penetration tester to conduct a phishing test. The tester wants to set up a fake log-in page and harvest credentials when target employees click on links in a phishing email. Which of the following commands would best help the tester determine which cloud email provider the log-in page needs to mimic?
After running the enum4linux.pl command, a penetration tester received the following output:
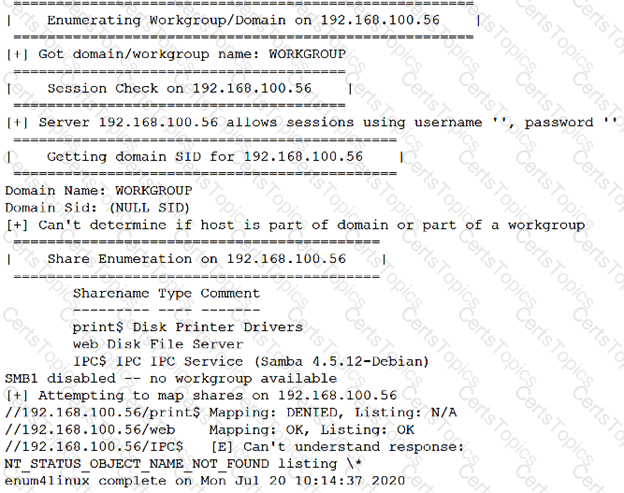
Which of the following commands should the penetration tester run NEXT?
A penetration tester successfully performed an exploit on a host and was able to hop from VLAN 100 to VLAN 200. VLAN 200 contains servers that perform financial transactions, and the penetration tester now wants the local interface of the attacker machine to have a static ARP entry in the local cache. The attacker machine has the following:
IP Address: 192.168.1.63
Physical Address: 60-36-dd-a6-c5-33
Which of the following commands would the penetration tester MOST likely use in order to establish a static ARP entry successfully?
While performing the scanning phase of a penetration test, the penetration tester runs the following command:
........v -sV -p- 10.10.10.23-28
....ip scan is finished, the penetration tester notices all hosts seem to be down. Which of the following options should the penetration tester try next?
A penetration tester was hired to perform a physical security assessment of an organization's office. After monitoring the environment for a few hours, the penetration tester notices that some employees go to lunch in a restaurant nearby and leave their belongings unattended on the table while getting food. Which of the following techniques would MOST likely be used to get legitimate access into the organization's building without raising too many alerts?
After gaining access to a Linux system with a non-privileged account, a penetration tester identifies the following file:
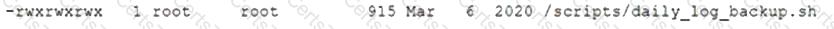
Which of the following actions should the tester perform FIRST?
A penetration tester utilized Nmap to scan host 64.13.134.52 and received the following results:

Based on the output, which of the following services are MOST likely to be exploited? (Choose two.)
A penetration tester runs the following command:
l.comptia.local axfr comptia.local
which of the following types of information would be provided?
A penetration tester was able to compromise a web server and move laterally into a Linux web server. The tester now wants to determine the identity of the last user who signed in to the web server. Which of the following log files will show this activity?
Which of the following tools would be best suited to perform a cloud security assessment?
A physical penetration tester needs to get inside an organization's office and collect sensitive information without acting suspiciously or being noticed by the security guards. The tester has observed that the company's ticket gate does not scan the badges, and employees leave their badges on the table while going to the restroom. Which of the following techniques can the tester use to gain physical access to the office? (Choose two.)
In Python socket programming, SOCK_DGRAM type is:
Which of the following is the most secure method for sending the penetration test report to the client?
A penetration tester writes the following script:
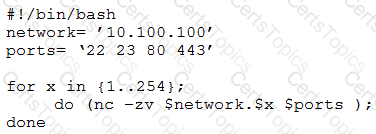
Which of the following is the tester performing?
When planning a penetration-testing effort, clearly expressing the rules surrounding the optimal time of day for test execution is important because:
A penetration tester uncovers access keys within an organization's source code management solution. Which of the following would BEST address the issue? (Choose two.)
A penetration tester has been hired to examine a website for flaws. During one of the time windows for testing, a network engineer notices a flood of GET requests to the web server, reducing the website’s response time by 80%. The network engineer contacts the penetration tester to determine if these GET requests are part of the test. Which of the following BEST describes the purpose of checking with the penetration tester?
A Chief Information Security Officer wants a penetration tester to evaluate whether a recently installed firewall is protecting a subnetwork on which many decades- old legacy systems are connected. The penetration tester decides to run an OS discovery and a full port scan to identify all the systems and any potential vulnerability. Which of the following should the penetration tester consider BEFORE running a scan?
During a penetration test, a tester is able to change values in the URL from example.com/login.php?id=5 to example.com/login.php?id=10 and gain access to a web application. Which of the following vulnerabilities has the penetration tester exploited?
A penetration tester is conducting a penetration test. The tester obtains a root-level shell on a Linux server and discovers the following data in a file named password.txt in the /home/svsacct directory:
U3VQZXIkM2NyZXQhCg==
Which of the following commands should the tester use NEXT to decode the contents of the file?
A penetration tester is conducting an unknown environment test and gathering additional information that can be used for later stages of an assessment. Which of the following would most likely produce useful information for additional testing?
A penetration tester is conducting a penetration test and discovers a vulnerability on a web server that is owned by the client. Exploiting the vulnerability allows the tester to open a reverse shell. Enumerating the server for privilege escalation, the tester discovers the following:
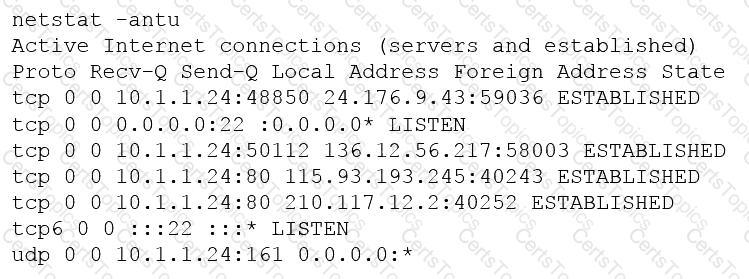
Which of the following should the penetration tester do NEXT?
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following:

Which of the following combinations of tools would the penetration tester use to exploit this script?
Which of the following assessment methods is MOST likely to cause harm to an ICS environment?
During an internal penetration test against a company, a penetration tester was able to navigate to another part of the network and locate a folder containing customer information such as addresses, phone numbers, and credit card numbers. To be PCI compliant, which of the following should the company have implemented to BEST protect this data?
A penetration tester, who is doing an assessment, discovers an administrator has been exfiltrating proprietary company information. The administrator offers to pay the tester to keep quiet. Which of the following is the BEST action for the tester to take?
The output from a penetration testing tool shows 100 hosts contained findings due to improper patch management. Which of the following did the penetration tester perform?
A penetration tester needs to upload the results of a port scan to a centralized security tool. Which of the following commands would allow the tester to save the results in an interchangeable format?
A penetration tester found several critical SQL injection vulnerabilities during an assessment of a client's system. The tester would like to suggest mitigation to the client as soon as possible.
Which of the following remediation techniques would be the BEST to recommend? (Choose two.)
A penetration tester wrote the following comment in the final report: "Eighty-five percent of the systems tested were found to be prone to unauthorized access from the internet." Which of the following audiences was this message intended?
A penetration tester is testing a new API for the company's existing services and is preparing the following script:
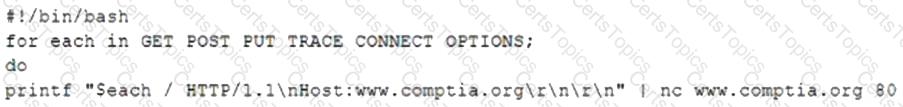
Which of the following would the test discover?
A penetration tester has extracted password hashes from the lsass.exe memory process. Which of the following should the tester perform NEXT to pass the hash and provide persistence with the newly acquired credentials?
During a penetration tester found a web component with no authentication requirements. The web component also allows file uploads and is hosted on one of the target public web the following actions should the penetration tester perform next?
Which of the following factors would a penetration tester most likely consider when testing at a location?
A penetration tester breaks into a company's office building and discovers the company does not have a shredding service. Which of the following attacks should the penetration tester try next?
Given the following script:
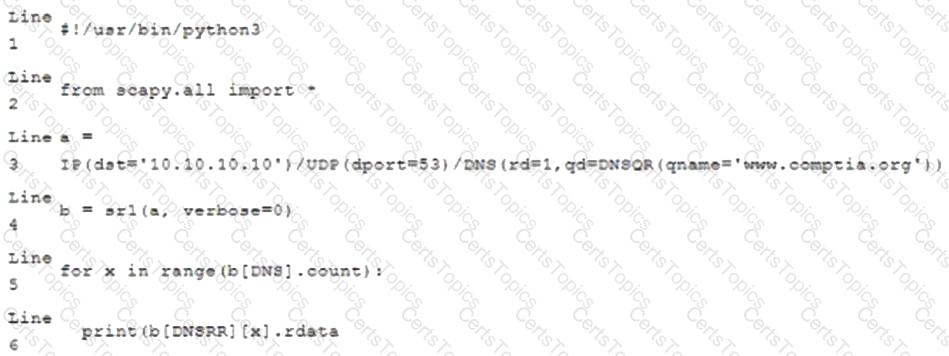
Which of the following BEST characterizes the function performed by lines 5 and 6?
A private investigation firm is requesting a penetration test to determine the likelihood that attackers can gain access to mobile devices and then exfiltrate data from those devices. Which of the following is a social-engineering method that, if successful, would MOST likely enable both objectives?
A client would like to have a penetration test performed that leverages a continuously updated TTPs framework and covers a wide variety of enterprise systems and networks. Which of the following methodologies should be used to BEST meet the client's expectations?
A red team completed an engagement and provided the following example in the report to describe how the team gained access to a web server:
x’ OR role LIKE '%admin%
Which of the following should be recommended to remediate this vulnerability?
A penetration-testing team needs to test the security of electronic records in a company's office. Per the terms of engagement, the penetration test is to be conducted after hours and should not include circumventing the alarm or performing destructive entry. During outside reconnaissance, the team sees an open door from an adjoining building. Which of the following would be allowed under the terms of the engagement?
Penetration tester who was exclusively authorized to conduct a physical assessment noticed there were no cameras pointed at the dumpster for company. The penetration tester returned at night and collected garbage that contained receipts for recently purchased networking :. The models of equipment purchased are vulnerable to attack. Which of the following is the most likely next step for the penetration?
A penetration tester wrote the following Bash script to brute force a local service password:
..ting as expected. Which of the following changes should the penetration tester make to get the script to work?
A penetration tester opened a shell on a laptop at a client's office but is unable to pivot because of restrictive ACLs on the wireless subnet. The tester is also aware that all laptop users have a hard-wired connection available at their desks. Which of the following is the BEST method available to pivot and gain additional access to the network?
Penetration tester is developing exploits to attack multiple versions of a common software package. The versions have different menus and )ut.. they have a common log-in screen that the exploit must use. The penetration tester develops code to perform the log-in that can be each of the exploits targeted to a specific version. Which of the following terms is used to describe this common log-in code example?
A penetration tester is able to capture the NTLM challenge-response traffic between a client and a server.
Which of the following can be done with the pcap to gain access to the server?
Given the following code:
Which of the following are the BEST methods to prevent against this type of attack? (Choose two.)
A penetration tester runs the unshadow command on a machine. Which of the following tools will the tester most likely use NEXT?
A penetration tester received a .pcap file to look for credentials to use in an engagement.
Which of the following tools should the tester utilize to open and read the .pcap file?
Running a vulnerability scanner on a hybrid network segment that includes general IT servers and industrial control systems:
Which of the following tools provides Python classes for interacting with network protocols?
Which of the following should a penetration tester do NEXT after identifying that an application being tested has already been compromised with malware?
An assessor wants to use Nmap to help map out a stateful firewall rule set. Which of the following scans will the assessor MOST likely run?
A client wants a security assessment company to perform a penetration test against its hot site. The purpose of the test is to determine the effectiveness of the defenses that protect against disruptions to business continuity. Which of the following is the MOST important action to take before starting this type of assessment?
A penetration tester who is conducting a vulnerability assessment discovers that ICMP is disabled on a network segment. Which of the following could be used for a denial-of-service attack on the network segment?
A penetration tester is looking for a vulnerability that enables attackers to open doors via a specialized TCP service that is used for a physical access control system. The service exists on more than 100 different hosts, so the tester would like to automate the assessment. Identification requires the penetration tester to:
Have a full TCP connection
Send a “hello” payload
Walt for a response
Send a string of characters longer than 16 bytes
Which of the following approaches would BEST support the objective?
A penetration tester has completed an analysis of the various software products produced by the company under assessment. The tester found that over the past several years the company has been including vulnerable third-party modules in multiple products, even though the quality of the organic code being developed is very good. Which of the following recommendations should the penetration tester include in the report?
A penetration tester would like to obtain FTP credentials by deploying a workstation as an on-path attack between the target and the server that has the FTP protocol. Which of the following methods would be the BEST to accomplish this objective?
A penetration tester has found indicators that a privileged user's password might be the same on 30 different Linux systems. Which of the following tools can help the tester identify the number of systems on which the password can be used?
Which of the following are the MOST important items to include in the final report for a penetration test? (Choose two.)
A company is concerned that its cloud service provider is not adequately protecting the VMs housing its software development. The VMs are housed in a datacenter with other companies sharing physical resources. Which of the following attack types is MOST concerning to the company?
Which of the following documents describes specific activities, deliverables, and schedules for a penetration tester?
An Nmap network scan has found five open ports with identified services. Which of the following tools should a penetration tester use NEXT to determine if any vulnerabilities with associated exploits exist on the open ports?
A software development team is concerned that a new product's 64-bit Windows binaries can be deconstructed to the underlying code. Which of the following tools can a penetration tester utilize to help the team gauge what an attacker might see in the binaries?
A penetration tester exploited a unique flaw on a recent penetration test of a bank. After the test was completed, the tester posted information about the exploit online along with the IP addresses of the exploited machines. Which of the following documents could hold the penetration tester accountable for this action?
You are a penetration tester reviewing a client’s website through a web browser.
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
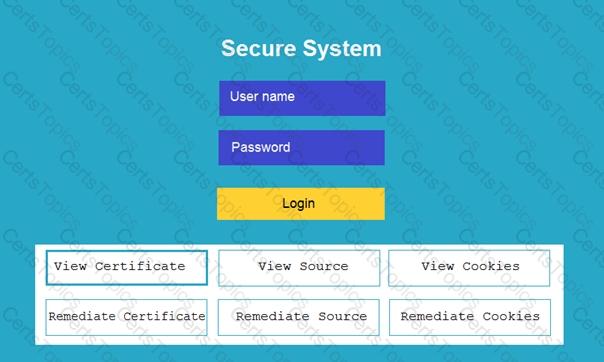
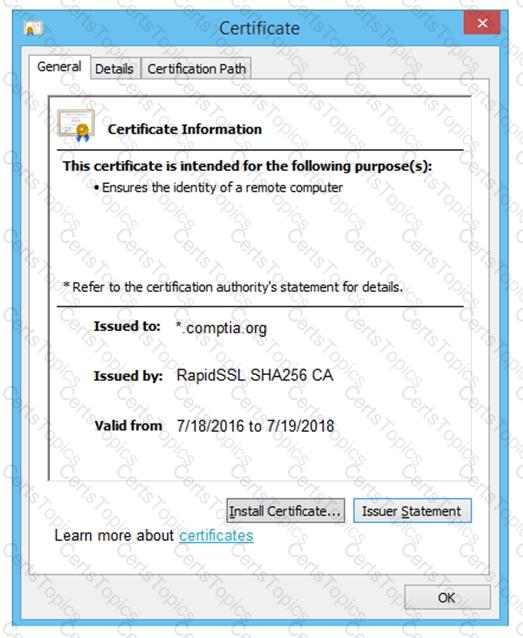

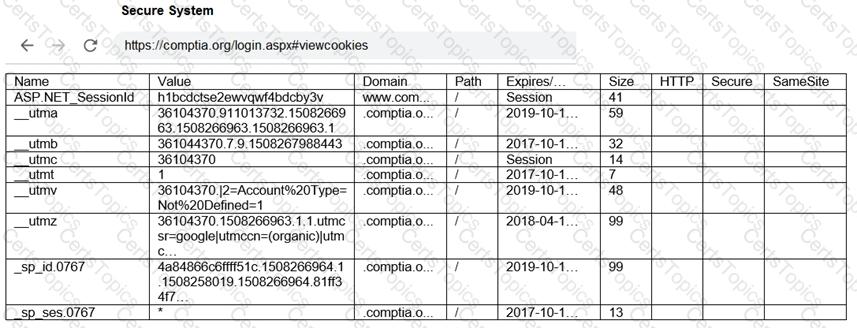
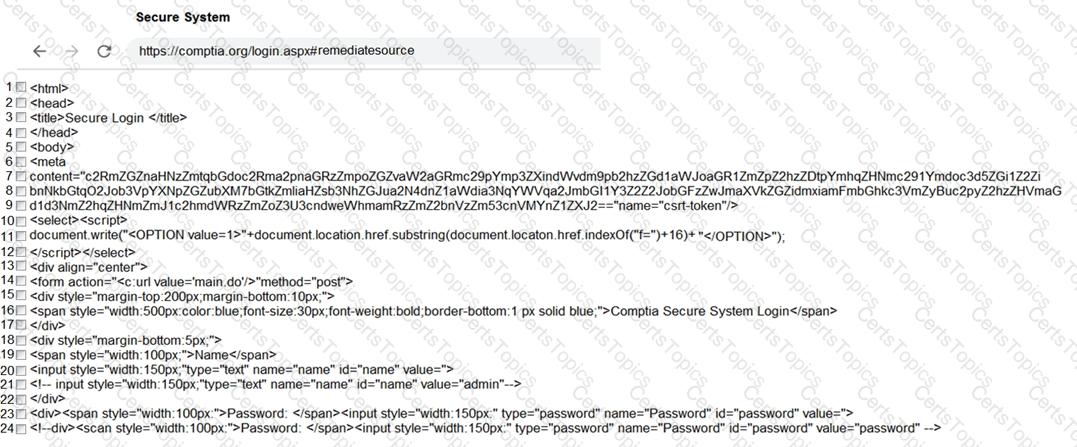
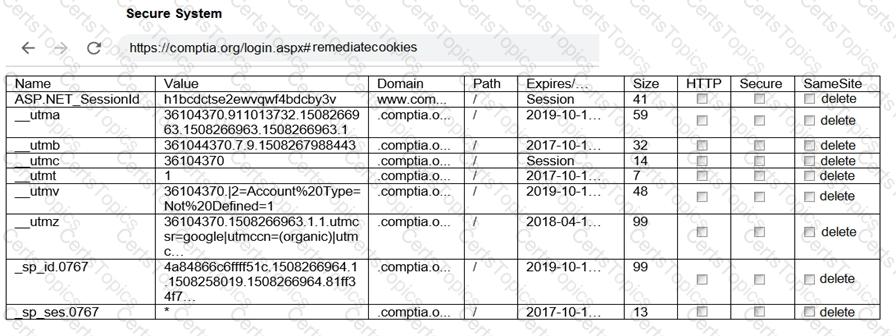
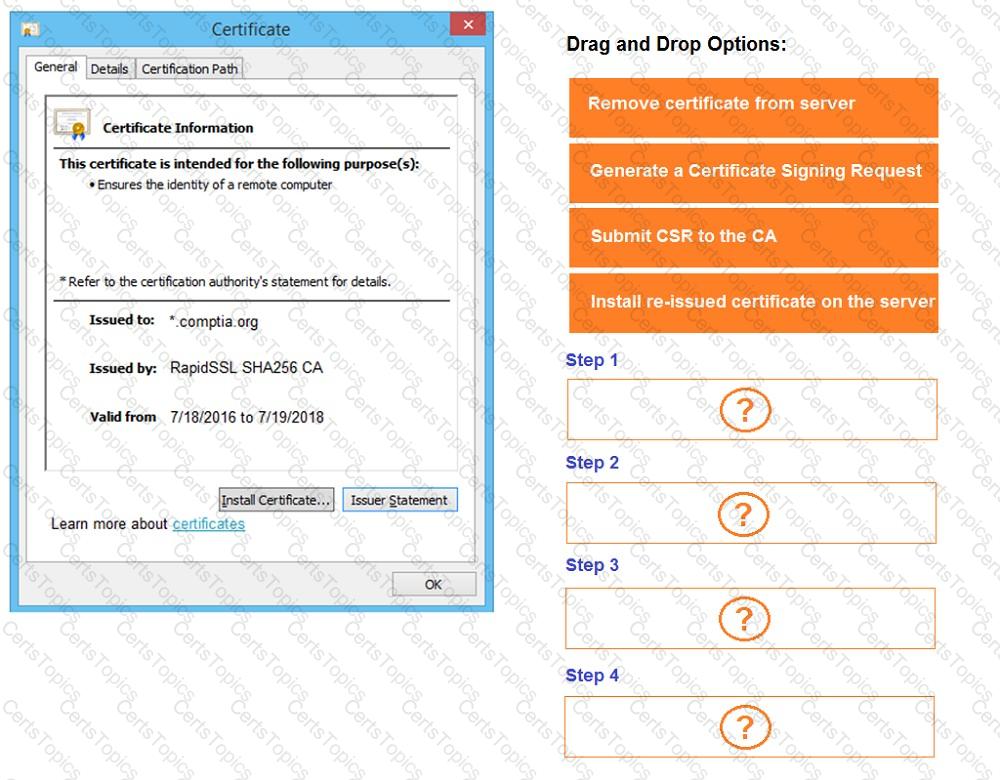
The results of an Nmap scan are as follows:
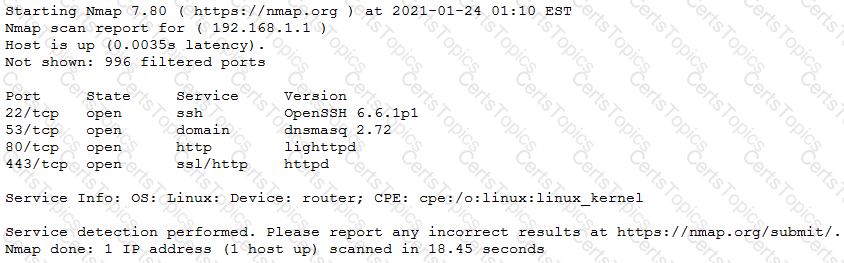
Which of the following would be the BEST conclusion about this device?
A penetration tester wrote the following script to be used in one engagement:
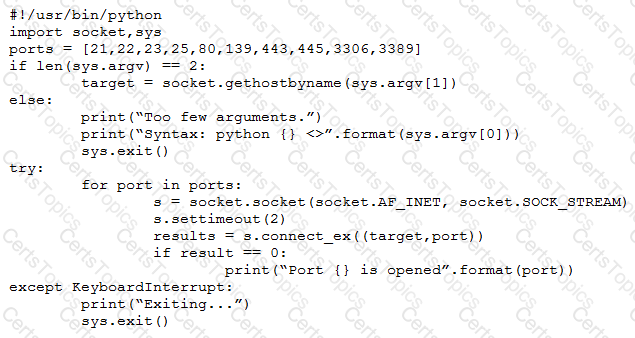
Which of the following actions will this script perform?
Deconfliction is necessary when the penetration test:
A penetration tester wants to scan a target network without being detected by the client’s IDS. Which of the following scans is MOST likely to avoid detection?
A penetration tester was able to gain access to a system using an exploit. The following is a snippet of the code that was utilized:
exploit = “POST ”
exploit += “/cgi-bin/index.cgi?action=login&Path=%27%0A/bin/sh${IFS} –
he;${IFS}chmod${IFS}777${IFS}apache;${IFS}./apache’%0A%27&loginUser=a&Pwd=a”
exploit += “HTTP/1.1”
Which of the following commands should the penetration tester run post-engagement?
A penetration tester is working on a scoping document with a new client. The methodology the client uses includes the following:
Pre-engagement interaction (scoping and ROE)
Intelligence gathering (reconnaissance)
Threat modeling
Vulnerability analysis
Exploitation and post exploitation
Reporting
Which of the following methodologies does the client use?
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
INSTRUCTIONS
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A penetration tester needs to access a building that is guarded by locked gates, a security team, and cameras. Which of the following is a technique the tester can use to gain access to the IT framework without being detected?
In the process of active service enumeration, a penetration tester identifies an SMTP daemon running on one of the target company’s servers. Which of the following actions would BEST enable the tester to perform
phishing in a later stage of the assessment?
A penetration tester has gained access to a network device that has a previously unknown IP range on an interface. Further research determines this is an always-on VPN tunnel to a third-party supplier.
Which of the following is the BEST action for the penetration tester to take?
A penetration tester has obtained shell access to a Windows host and wants to run a specially crafted binary for later execution using the wmic.exe process call create function. Which of the following OS or filesystem mechanisms is MOST likely to support this objective?
A penetration tester has gained access to part of an internal network and wants to exploit on a different network segment. Using Scapy, the tester runs the following command:
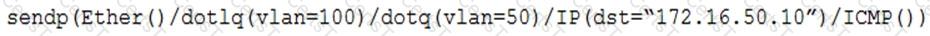
Which of the following represents what the penetration tester is attempting to accomplish?
When preparing for an engagement with an enterprise organization, which of the following is one of the MOST important items to develop fully prior to beginning the penetration testing activities?
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following:
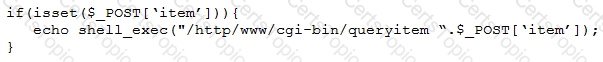
Which of the following tools will help the tester prepare an attack for this scenario?
A large client wants a penetration tester to scan for devices within its network that are Internet facing. The client is specifically looking for Cisco devices with no authentication requirements. Which of the following settings in Shodan would meet the client’s requirements?
A company hired a penetration tester to do a social-engineering test against its employees. Although the tester did not find any employees’ phone numbers on the company’s website, the tester has learned the complete phone catalog was published there a few months ago.
In which of the following places should the penetration tester look FIRST for the employees’ numbers?
A penetration tester received a 16-bit network block that was scoped for an assessment. During the assessment, the tester realized no hosts were active in the provided block of IPs and reported this to the company. The company then provided an updated block of IPs to the tester. Which of the following would be the most appropriate NEXT step?
A penetration tester was conducting a penetration test and discovered the network traffic was no longer reaching the client’s IP address. The tester later discovered the SOC had used sinkholing on the penetration tester’s IP address. Which of the following BEST describes what happened?
A penetration tester conducted a discovery scan that generated the following:
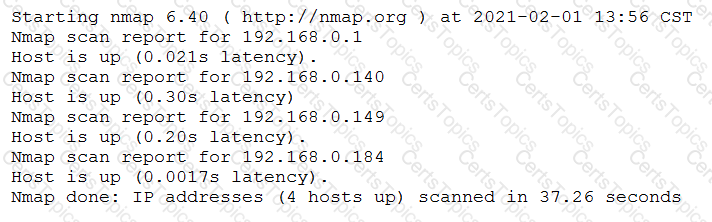
Which of the following commands generated the results above and will transform them into a list of active hosts for further analysis?
A security engineer identified a new server on the network and wants to scan the host to determine if it is running an approved version of Linux and a patched version of Apache. Which of the following commands will accomplish this task?
A penetration tester found the following valid URL while doing a manual assessment of a web application:
Which of the following automated tools would be best to use NEXT to try to identify a vulnerability in this URL?
A penetration tester has obtained root access to a Linux-based file server and would like to maintain persistence after reboot. Which of the following techniques would BEST support this objective?
Which of the following protocols or technologies would provide in-transit confidentiality protection for emailing the final security assessment report?
A penetration tester has obtained a low-privilege shell on a Windows server with a default configuration and now wants to explore the ability to exploit misconfigured service permissions. Which of the following commands would help the tester START this process?