A company has wired VolP phones, which transmit tagged traffic and connect to AOS-CX switches. The company wants to tunnel the phones' traffic to an HPE
Aruba Networking gateway for applying security policies.
What is part of the correct configuration on the AOS-CX switches?
What role can Internet Key Exchange (IKE)/IKEv2 play in an HPE Aruba Networking client-to-site VPN?
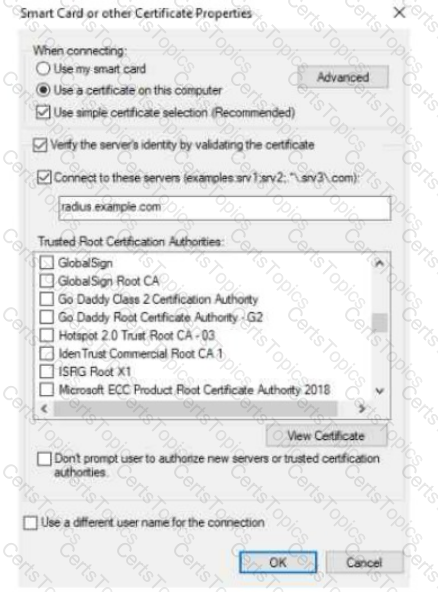
The exhibit shows the 802.1X-related settings for Windows domain clients. What should admins change to make the settings follow best security practices?
A company has a variety of HPE Aruba Networking solutions, including an HPE Aruba Networking infrastructure and HPE Aruba Networking ClearPass Policy Manager (CPPM). The company passes traffic from the corporate LAN destined to the data center through a third-party SRX firewall. The company would like to further protect itself from internal threats. What is one solution that you can recommend?