A company recently acquired a SaaS company and performed a gap analysis. The results of the gap analysis indicate security controls are absent throughout the SDLC and have led to several vulnerable production releases. Which of the following security tools best reduces the risk of vulnerable code being pushed to production in the future?
A security analyst is reviewing the following output from a vulnerability scan from an organization's internet-facing web services:
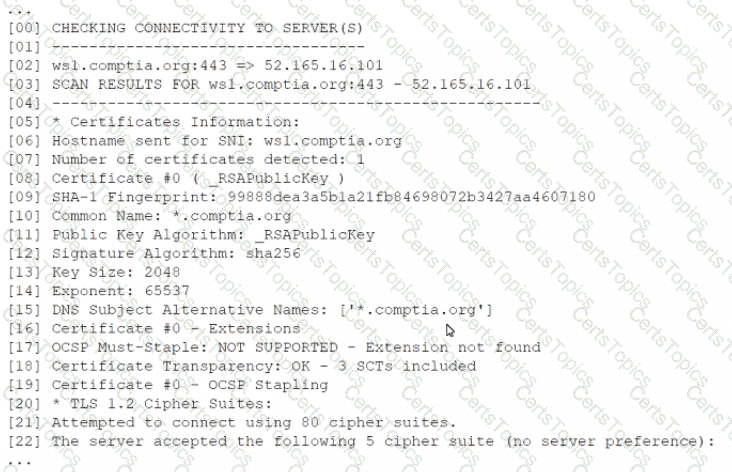
Which of the following indicates a susceptibility whereby an attacker can take advantage of the trust relationship between the client and the server?
A CRM company leverages a CSP PaaS service to host and publish its SaaS product. Recently, a large customer requested that all infrastructure components must meet strict regulatory requirements, including configuration management, patch management, and life-cycle management. Which of the following organizations is responsible for ensuring those regulatory requirements are met?
Which of the following describes how a risk assessment is performed when an organization has a critical vendor that provides multiple products?