A web application requires multifactor authentication when a user accesses the application from a home office but does not require this when the user is in the office. What access control model is this describing?
What is the maximum passphrase length in Windows 2000/XP/2003?
What technique makes it difficult for attackers to predict the memory address space location for code execution?
Which of the following features of Windows 7 allows an administrator to both passively review installed software and configure policies to prevent out-of-date or insecure software from running?
What is the main problem with relying solely on firewalls to protect your company's sensitive data?
What is a recommended defense against SQL injection, OS injection, and buffer overflows?
Which of the following is a potential WPA3 security issue?
Which Defense-in-Depth principle starts with an awareness of the value of each section of information within an organization?
Which of the following applications would be BEST implemented with UDP instead of TCP?
Which logging capability is provided natively by syslog?
Which port category does the port 110 fall into?
Which of the following defines the communication link between a Web server and Web applications?
You have reason to believe someone with a domain user account has been accessing and modifying sensitive spreadsheets on one of your application servers. You decide to enable auditing for the files to see who is accessing and changing them. You enable the Audit Object Access policy on the files via Group Policy. Two weeks later, when you check on the audit logs, you see they are empty. What is the most likely reason this has happened?
Which of the following would be a valid reason to use a Windows workgroup?
Which of the following heights of fence deters only casual trespassers?
Analyze the screenshot below. What is the purpose of this message?
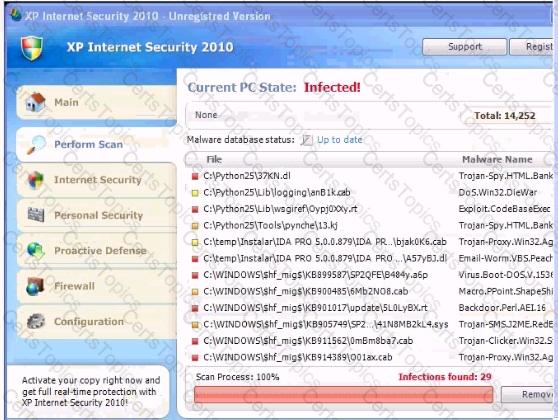
Which of the following tasks is the responsibility of a Linux systems administrator who is deploying hardening scripts to his systems?
An application developer would like to replace Triple DES in their software with a stronger algorithm of the same type. Which of the following should they use?
What is the function of the TTL (Time to Live) field in IPv4 and the Hop Limit field in IPv6 In an IP Packet header?
When should you create the initial database for a Linux file integrity checker?
Which of the following elements is the most important requirement to ensuring the success of a business continuity plan?
The previous system administrator at your company used to rely heavily on email lists, such as vendor lists and Bug Traq to get information about updates and patches. While a useful means of acquiring data, this requires time and effort to read through. In an effort to speed things up, you decide to switch to completely automated updates and patching. You set up your systems to automatically patch your production servers using a cron job and a scripted apt-get upgrade command. Of the following reasons, which explains why you may want to avoid this plan?
During which of the following steps is the public/private key-pair generated for Public Key Infrastructure (PKI)?
Which of the following networking topologies uses a hub to connect computers?
An attacker gained physical access to an internal computer to access company proprietary data. The facility is protected by a fingerprint biometric system that records both failed and successful entry attempts. No failures were logged during the time periods of the recent breach. The account used when the attacker entered the facility shortly before each incident belongs to an employee who was out of the area. With respect to the biometric entry system, which of the following actions will help mitigate unauthorized physical access to the facility?
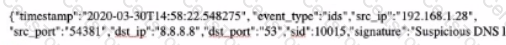
You are examining a packet capture session in Wire shark and see the packet shown in the accompanying image. Based on what you see, what is the appropriate protection against this type of attempted attack?
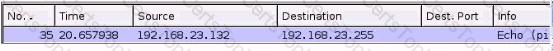
Which of the following terms is used for the process of securing a system or a device on a network infrastructure?
Mark works as a Network Administrator for NetTech Inc. The company has a Windows 2003 domain- based network. The network contains ten Windows 2003 member servers, 150 Windows XP Professional client computers. According to the company's security policy, Mark needs to check whether all the computers in the network have all available security updates and shared folders. He also needs to check the file system type on each computer's hard disk. Mark installs and runs MBSACLI.EXE with the appropriate switches on a server. Which of the following tasks will he accomplish?
For most organizations, which of the following should be the highest priority when it comes to physical security concerns?
Which of the following is a characteristic of hash operations?
Many IIS servers connect to Microsoft SQL databases. Which of the following statements about SQL server security is TRUE?
What is log, pre-processing?
What does PowerShell remoting use to authenticate to another host in a domain environment?
Which of the following is an advantage of an Intrusion Detection System?
An email system administrator deploys a configuration blocking all inbound and outbound executable files due to security concerns.
What Defense in Depth approach is being used?
The following three steps belong to the chain of custody for federal rules of evidence. What additional step is recommended between steps 2 and 3?
STEP 1 - Take notes: who, what, where, when and record serial numbers of machine(s) in question.
STEP 2 - Do a binary backup if data is being collected.
STEP 3 - Deliver collected evidence to law enforcement officials.
How often is session information sent to the web server from the browser once the session information has been established?
You are implementing wireless access at a defense contractor. Specifications say, you must implement the AES Encryption algorithm. Which encryption standard should you choose?
Which of the following is a backup strategy?
Which of the following protocols provides maintenance and error reporting function?
You work as a Network Administrator for Net Soft Inc. You are designing a data backup plan for your company's network. The backup policy of the company requires high security and easy recovery of data. Which of the following options will you choose to accomplish this?
What is the name of the registry key that is used to manage remote registry share permissions for the whole registry?
Which file would the entry below be found in?
net.ipv6.conf.all.acctpt-ra=0
There are three key factors in selecting a biometric mechanism. What are they?
What advantage does a Client-to-Client VPN have over other types of VPNs?
What type of attack can be performed against a wireless network using the tool Kismet?
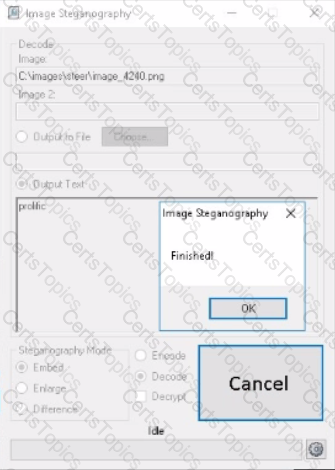
In the directory C:\lmages\steer there Is an Image file lmage_4240.png with a data string encoded inside the file. What word is hidden in the file?

Which of the following are used to suppress gasoline and oil fires? Each correct answer represents a complete solution. Choose three.
SSL session keys are available in which of the following lengths?
You have implemented a firewall on the company's network for blocking unauthorized network connections. Which of the following types of security control is implemented in this case?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He is currently working on his C based new traceroute program. Since, many processes are running together on the system, he wants to give the highest priority to the cc command process so that he can test his program, remove bugs, and submit it to the office in time. Which of the following commands will John use to give the highest priority to the cc command process?
Which of the following protocols are used to provide secure communication between a client and a server over the Internet?
Each correct answer represents a part of the solution. Choose two.
Use PowerShell ISE to
examineC:\Windows\security\templates\WorkstationSecureTemplate.inf. Which setting is configured in the template?

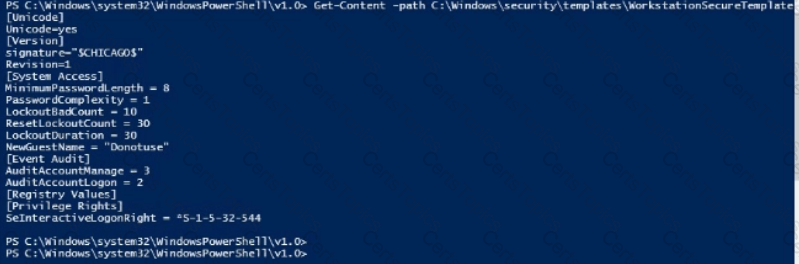
Which Windows event log would you look in if you wanted information about whether or not a specific diver was running at start up?
Which of the following is a Personal Area Network enabled device?
Included below is the output from a resource kit utility run against local host.
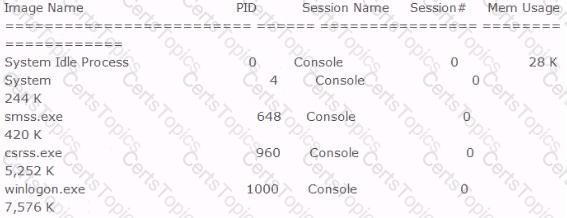
Which command could have produced this output?
Which of the following are the types of intrusion detection systems?
Each correct answer represents a complete solution. Choose all that apply.
A Network Engineer is charged with maintaining and protecting a network with a high availability requirement. In addition to other defenses, they have chosen to implement a NIPS. How should the NIPS failure conditions be configured to ensure availability if the NIPS is installed in front of the Firewall that protects the DMZ?
What type of HTTP session tracking artifact is designed to expire once a user’s web browser session is closed?
How many clients Is a single WSUS server designed to support when the minimum system requirements are met?
What does Authentication Header (AH) add to the packet in order to prevent an attacker from lying about the source?
What Windows log should be checked to troubleshoot a Windows service that is falling to start?
Which of the following are advantages of Network Intrusion Detection Systems (NIDS)?
Which of the following is NOT a recommended best practice for securing Terminal Services and Remote Desktop?
A folder D:\Files\Marketing has the following NTFS permissions:
• Administrators: Full Control
• Marketing: Change and Authenticated
• Users: Read
It has been shared on the server as "MARKETING", with the following share permissions:
• Full Control share permissions for the Marketing group
Which of the following effective permissions apply if a user from the Sales group accesses the \\FILESERVER\MARKETING shared folder?
The Linux command to make the /etc/shadow file, already owned by root, readable only by root is which of the following?
Which of the following TCP dump output lines indicates the first step in the TCP 3-way handshake?
How are differences in configuration settings handled between Domain and Local Group Policy Objects (GPOs)?
What dots Office 365 use natively for authentication?
Which of the following applications cannot proactively detect anomalies related to a computer?
Which field in the IPv6 header is used for QoS. or specifying the priority of the packet?
What method do Unix-type systems use to prevent attackers from cracking passwords using pre-computed hashes?
Which of the following statements about Network Address Translation (NAT) are true? Each correct answer represents a complete solution. Choose two.
Which of the following is used to allow or deny access to network resources?
Which of the following are the types of access controls?
Each correct answer represents a complete solution. Choose three.
What could be used to mitigate hash collisions?
Which of the following statements about the authentication concept of information security management is true?
How can an adversary utilize a stolen database of unsalted password hashes?
Your organization is developing a network protection plan. No single aspect of your network seems more important than any other. You decide to avoid separating your network into segments or categorizing the systems on the network. Each device on the network is essentially protected in the same manner as all other devices.
This style of defense-in-depth protection is best described as which of the following?
What defensive measure could have been taken that would have protected the confidentiality of files that were divulged by systems that were compromised by malware?
A system administrator sees the following URL in the webserver logs:
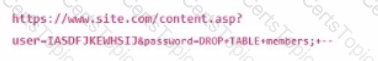
Which action will mitigate against this attack?
Which of the following statements about Hypertext Transfer Protocol Secure (HTTPS) are true? Each correct answer represents a complete solution. Choose two.
Which of the following resources is a knowledge base of real-world observed adversary tactics and techniques?
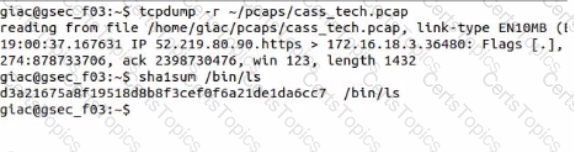
What is the SHA1 hash of the Ale /bin/Is?

Which of the following is the reason of using Faraday cage?
You work as a Network Administrator for Tech2tech Inc. You have configured a network-based IDS for your company. You have physically installed sensors at all key positions throughout the network such that they all report to the command console.
What will be the key functions of the sensors in such a physical layout?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for World Perfect Inc. The company has a Linux-based network. You have configured a Linux Web server on the network. A user complains that the Web server is not responding to requests. The process list on the server shows multiple instances of the HTTPD process. You are required to stop the Web service. Which of the following commands will you use to resolve the issue?
You work as a Network Administrator for Rick International. The company has a TCP/IP-based network. A user named Kevin wants to set an SSH terminal at home to connect to the company's network. You have to configure your company's router for it. By default, which of the following standard ports does the SSH protocol use for connection?
Which of the following commands is used to change file access permissions in Linux?
A US case involving malicious code is brought to trial. An employee had opened a helpdesk ticket to report specific instances of strange behavior on her system. The IT helpdesk representative collected information by interviewing the user and escalated the ticket to the system administrators. As the user had regulated and sensitive data on her computer, the system administrators had the hard drive sent to the company's forensic consultant for analysis and configured a new hard drive for the user. Based on the recommendations from the forensic consultant and the company's legal department, the CEO decided to prosecute the author of the malicious code. During the court case, which of the following would be able to provide direct evidence?
The TTL can be found in which protocol header?
What is the command-line tool for Windows XP and later that allows administrators the ability to get or set configuration data for a very wide variety of computer and user account settings?
Which of the following logging tasks should be evaluated in real-time?
Training an organization on possible phishing attacks would be included under which NIST Framework Core guidelines?
Which of the following are network connectivity devices?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following terms refers to the process in which headers and trailers are added around user data?
What is the motivation behind SYN/FIN scanning?
When discussing access controls, which of the following terms describes the process of determining the activities or functions that an Individual is permitted to perform?
Why are false positives such a problem with IPS technology?
Which of the following items are examples of preventive physical controls? Each correct answer represents a complete solution. Choose three.
Which of the following statements would be seen in a Disaster Recovery Plan?
Which layer of the TCP/IP Protocol Stack Is responsible for port numbers?
Why would someone use port 80 for deployment of unauthorized services?
A Host-based Intrusion Prevention System (HIPS) software vendor records how the Firefox Web browser interacts with the operating system and other applications, and identifies all areas of Firefox functionality. After collecting all the data about how Firefox should work, a database is created with this information, and it is fed into the HIPS software. The HIPS then monitors Firefox whenever it's in use. What feature of HIPS is being described in this scenario?
What must be added to VLANs to improve security?
Which access control mechanism requires a high amount of maintenance since all data must be classified, and all users granted appropriate clearance?
When you log into your Windows desktop what information does your Security Access Token (SAT) contain?
Which of the following SIP methods is used to setup a new session and add a caller?
In PKI, when someone wants to verify that the certificate is valid, what do they use to decrypt the signature?
Which of the following statements about policy is FALSE?
You work as a Network Administrator for McNeil Inc. The company has a Linux-based network. David, a Sales Manager, wants to know the name of the shell that he is currently using. Which of the following commands will he use to accomplish the task?
Which of the following correctly describes a stateless packet filter?
An attacker is able to trick an IDS into ignoring malicious traffic through obfuscation of the packet payload. What type of IDS error has occurred?
What does it mean if a protocol such as HTTP is stateless?