You have reason to believe someone with a domain user account has been accessing and modifying sensitive spreadsheets on one of your application servers. You decide to enable auditing for the files to see who is accessing and changing them. You enable the Audit Object Access policy on the files via Group Policy. Two weeks later, when you check on the audit logs, you see they are empty. What is the most likely reason this has happened?
Which of the following would be a valid reason to use a Windows workgroup?
Which of the following heights of fence deters only casual trespassers?
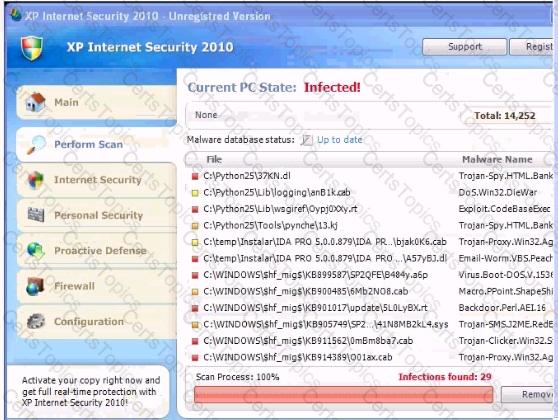
Analyze the screenshot below. What is the purpose of this message?