There are three key factors in selecting a biometric mechanism. What are they?
What advantage does a Client-to-Client VPN have over other types of VPNs?
What type of attack can be performed against a wireless network using the tool Kismet?
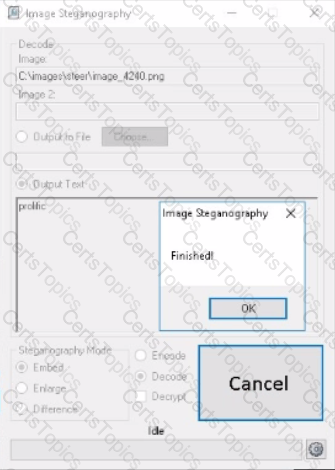
In the directory C:\lmages\steer there Is an Image file lmage_4240.png with a data string encoded inside the file. What word is hidden in the file?