Included below is the output from a resource kit utility run against local host.
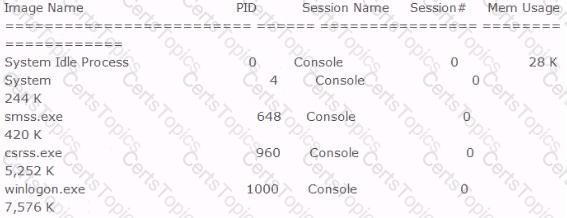
Which command could have produced this output?
Which of the following are the types of intrusion detection systems?
Each correct answer represents a complete solution. Choose all that apply.
A Network Engineer is charged with maintaining and protecting a network with a high availability requirement. In addition to other defenses, they have chosen to implement a NIPS. How should the NIPS failure conditions be configured to ensure availability if the NIPS is installed in front of the Firewall that protects the DMZ?
What type of HTTP session tracking artifact is designed to expire once a user’s web browser session is closed?