Which of the following digital forensics activities would a security team perform when responding to legal requests in a pending investigation?
A company prevented direct access from the database administrators’ workstations to the network segment that contains database servers. Which of the following should a database administrator use to access the database servers?
An organization failed to account for the right-to-be-forgotten regulations. Which of the following impacts might this action have on the company?
Which of the following can assist in recovering data if the decryption key is lost?
A security analyst reviews domain activity logs and notices the following:
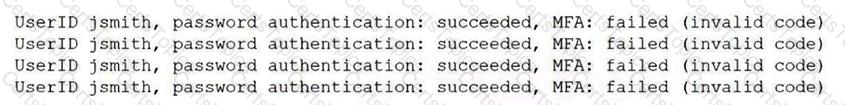
Which of the following is the best explanation for what the security analyst has discovered?
An administrator learns that users are receiving large quantities of unsolicited messages. The administrator checks the content filter and sees hundreds of messages sent to multiple users. Which of the following best describes this kind of attack?
A visitor plugs a laptop into a network jack in the lobby and is able to connect to the company's network. Which of the following should be configured on the existing network infrastructure to best prevent this activity?
A company evaluates several options that would allow employees to have remote access to the network. The security team wants to ensure the solution includes AAA to comply with internal security policies. Which of the following should the security team recommend?
A company is developing a critical system for the government and storing project information on a fileshare. Which of the following describes how this data will most likely be classified? (Select two).
Which of the following can be best used to discover a company's publicly available breach information?
Which of the following is a primary security concern for a company setting up a BYOD program?
A security engineer configured a remote access VPN. The remote access VPN allows end users to connect to the network by using an agent that is installed on the endpoint, which establishes an encrypted tunnel. Which of the following protocols did the engineer most likely implement?
A security analyst is examining a penetration test report and notices that the tester pivoted to critical internal systems with the same local user ID and password. Which of the following would help prevent this in the future?
A penetration tester is testing the security of a building’s alarm system. Which type of penetration test is being conducted?
A security analyst must prevent remote users from accessing malicious URLs. The sites need to be checked inline for reputation, content, or categorization. Which of the following technologies will help secure the enterprise?
An organization needs to monitor its users' activities to prevent insider threats. Which of the following solutions would help the organization achieve this goal?
An IT team rolls out a new management application that uses a randomly generated MFA token sent to the administrator’s phone. Despite this new MFA precaution, there is a security breach of the same software. Which of the following describes this kind of attack?
After a company was compromised, customers initiated a lawsuit. The company's attorneys have requested that the security team initiate a legal hold in response to the lawsuit. Which of the following describes the action the security team will most likely be required to take?
The Chief Information Security Officer (CISO) requires that new servers include hardware-level memory encryption. Which of the following data states does the CISO want to protect?
A cybersecurity incident response team at a large company receives notification that malware is present on several corporate desktops No known Indicators of compromise have been found on the network. Which of the following should the team do first to secure the environment?
A systems administrator needs to ensure the secure communication of sensitive data within the organization's private cloud. Which of the following is the best choice for the administrator to implement?
A security team is reviewing the findings in a report that was delivered after a third party performed a penetration test. One of the findings indicated that a web application form field is vulnerable to cross-site scripting. Which of the following application security techniques should the security analyst recommend the developer implement to prevent this vulnerability?
Which of the following topics would most likely be included within an organization's SDLC?
A security architect wants to prevent employees from receiving malicious attachments by email. Which of the following functions should the chosen solution do?
Attackers created a new domain name that looks similar to a popular file-sharing website. Which of the following threat vectors is being used?
Which of the following describes the difference between encryption and hashing?
Which of the following should be used to select a label for a file based on the file's value, sensitivity, or applicable regulations?
After a recent vulnerability scan, a security engineer needs to harden the routers within the corporate network. Which of the following is the most appropriate to disable?
An organization has been experiencing issues with deleted network share data and improperly assigned permissions. Which of the following would best help track and remediate these issues?
A security analyst scans a company's public network and discovers a host is running a remote desktop that can be used to access the production network. Which of the following changes should the security analyst recommend?
The number of tickets the help desk has been receiving has increased recently due to numerous false-positive phishing reports. Which of the following would be best to help to reduce the false positives?
Which of the following security control types does an acceptable use policy best represent?
Which of the following can best contribute to prioritizing patch applications?
A company is in the process of migrating to cloud-based services. The company's IT department has limited resources for migration and ongoing support. Which of the following best meets the company's needs?
Employees sign an agreement that restricts specific activities when leaving the company. Violating the agreement can result in legal consequences. Which of the following agreements does this best describe?
Which of the following factors are the most important to address when formulating a training curriculum plan for a security awareness program? (Select two).
A security analyst is creating the first draft of a network diagram for the company's new customer-facing payment application that will be hosted by a third-party cloud service
provider.
Which of the following allows an exploit to go undetected by the operating system?
Which of the following is an example of memory injection?
A systems administrator is creating a script that would save time and prevent human error when performing account creation for a large number of end users. Which of the following would be a good use case for this task?
Which of the following would best explain why a security analyst is running daily vulnerability scans on all corporate endpoints?
A company decided to reduce the cost of its annual cyber insurance policy by removing the coverage for ransomware attacks.
Which of the following analysis elements did the company most likely use in making this decision?
During a recent log review, an analyst discovers evidence of successful injection attacks. Which of the following will best address this issue?
Which of the following is the primary purpose of a service that tracks log-ins and time spent using the service?
A user would like to install software and features that are not available with a smartphone's default software. Which of the following would allow the user to install unauthorized software and enable new features?
A customer of a large company receives a phone call from someone claiming to work for the company and asking for the customer's credit card information. The customer sees the caller ID is the same as the company's main phone number. Which of the following attacks is the customer most likely a target of?
An administrator was notified that a user logged in remotely after hours and copied large amounts of data to a personal device.
Which of the following best describes the user’s activity?
An administrator discovers a cross-site scripting vulnerability on a company website. Which of the following will most likely remediate the issue?
A website user is locked out of an account after clicking an email link and visiting a different website Web server logs show the user's password was changed, even though the user did not change the password. Which of the following is the most likely cause?
Which of the following is a social engineering attack in which a bad actor impersonates a web URL?
Which of the following should be used to ensure a device is inaccessible to a network-connected resource?
Which of the following describes the understanding between a company and a client about what will be provided and the accepted time needed to provide the company with the resources?
Which of the following has been implemented when a host-based firewall on a legacy Linux system allows connections from only specific internal IP addresses?
Which of the following agreement types defines the time frame in which a vendor needs to respond?
An attacker submits a request containing unexpected characters in an attempt to gain unauthorized access to information within the underlying systems. Which of the following best describes this attack?
Which of the following would be the best solution to deploy a low-cost standby site that includes hardware and internet access?
Which of the following is most likely associated with introducing vulnerabilities on a corporate network by the deployment of unapproved software?
An accounting employee recently used software that was not approved by the company. Which of the following risks does this most likely represent?
A security administrator would like to protect data on employees’ laptops. Which of the following encryption techniques should the security administrator use?
Which of the following alert types is the most likely to be ignored over time?
An organization maintains intellectual property that it wants to protect. Which of the following concepts would be most beneficial to add to the company's security awareness training program?
Which of the following is a benefit of an RTO when conducting a business impact analysis?
The Chief Information Security Officer (CISO) has determined the company is non-compliant with local data privacy regulations. The CISO needs to justify the budget request for more resources. Which of the following should the CISO present to the board as the direct consequence of non-compliance?
Which of the following technologies assists in passively verifying the expired status of a digital certificate?
An organization is required to provide assurance that its controls are properly designed and operating effectively. Which of the following reports will best achieve the objective?
An organization implemented cloud-managed IP cameras to monitor building entry points and sensitive areas. The service provider enables direct TCP/IP connection to stream live video footage from each camera. The organization wants to ensure this stream is encrypted and authenticated. Which of the following protocols should be implemented to best meet this objective?
Various company stakeholders meet to discuss roles and responsibilities in the event of a security breach that would affect offshore offices. Which of the following is this an example of?
After a series of account compromises and credential misuse, a company hires a security manager to develop a security program. Which of the following steps should the security manager take first to increase security awareness?
Which of the following describes the process of concealing code or text inside a graphical image?
Which of the following is the most important element when defining effective security governance?
Which of the following is the most effective way to protect an application server running software that is no longer supported from network threats?
A company’s legal department drafted sensitive documents in a SaaS application and wants to ensure the documents cannot be accessed by individuals in high-risk countries. Which of the following is the most effective way to limit this access?
For which of the following reasons would a systems administrator leverage a 3DES hash from an installer file that is posted on a vendor's website?
Which of the following is a vulnerability concern for end-of-life hardware?
Which of the following is a technical security control?
Which of the following describes a situation where a user is authorized before being authenticated?
A company is redesigning its infrastructure and wants to reduce the number of physical servers in use. Which of the following architectures is best suited for this goal?
Which of the following best explains a concern with OS-based vulnerabilities?
The internal audit team determines a software application is no longer in scope for external reporting requirements. Which of the following will confirm management’s perspective that the application is no longer applicable?
A new employee accessed an unauthorized website. An investigation found that the employee violated the company's rules. Which of the following did the employee violate?
A systems administrator is concerned about vulnerabilities within cloud computing instances Which of the following is most important for the administrator to consider when architecting a cloud computing environment?
Which of the following actions is best performed by ticketing automation to ensure that incidents receive the correct level of attention and response?
A store is setting up wireless access for their employees. Management wants to limit the number of access points while ensuring all areas of the store are covered. Which of the following tools will help management determine the number of access points needed?
Which of the following explains how a supply chain service provider could introduce a security vulnerability into an organization?
Which of the following definitions best describes the concept of log co-relation?
Which of the following best represents an application that does not have an on-premises requirement and is accessible from anywhere?
A security engineer at a large company needs to enhance IAM to ensure that employees can only access corporate systems during their shifts. Which of the following access controls should the security engineer implement?
A company's marketing department collects, modifies, and stores sensitive customer data. The infrastructure team is responsible for securing the data while in transit and at rest. Which of the following data roles describes the customer?
An administrator is creating a secure method for a contractor to access a test environment. Which of the following would provide the contractor with the best access to the test environment?
The Chief Information Security Officer (CISO) at a large company would like to gain an understanding of how the company's security policies compare to the requirements imposed by external regulators. Which of the following should the CISO use?
An administrator at a small business notices an increase in support calls from employees who receive a blocked page message after trying to navigate to a spoofed website. Which of the following should the administrator do?
An employee clicks a malicious link in an email that appears to be from the company's Chief Executive Officer. The employee's computer is infected with ransomware that encrypts the company's files. Which of the following is the most effective way for the company to prevent similar incidents in the future?
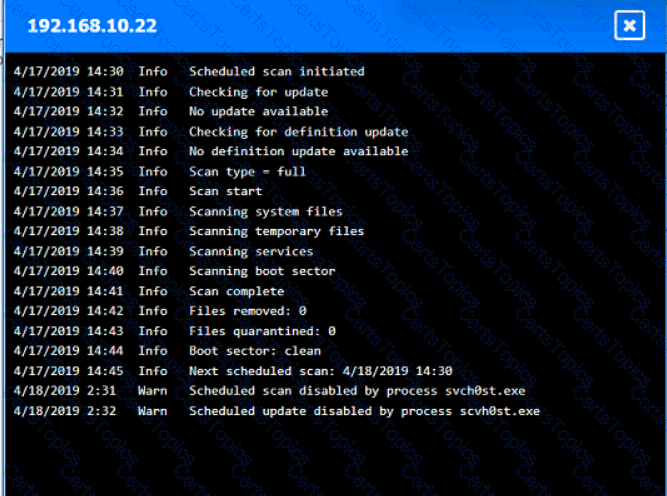
You are security administrator investigating a potential infection on a network.
Click on each host and firewall. Review all logs to determine which host originated the Infecton and then deny each remaining hosts clean or infected.
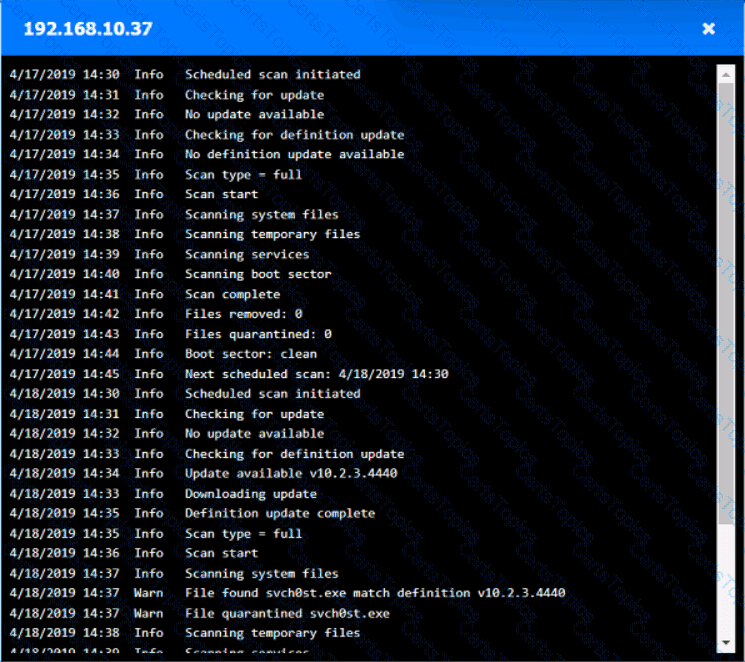
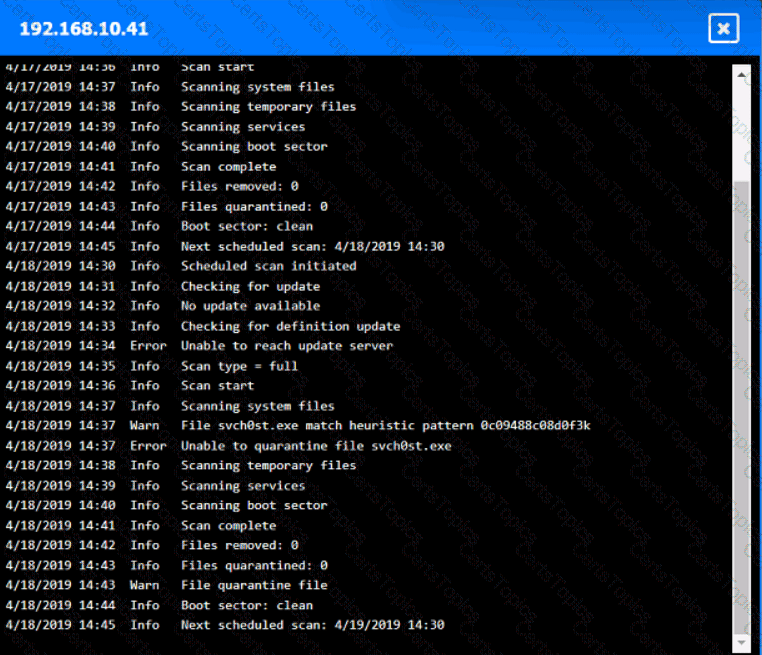
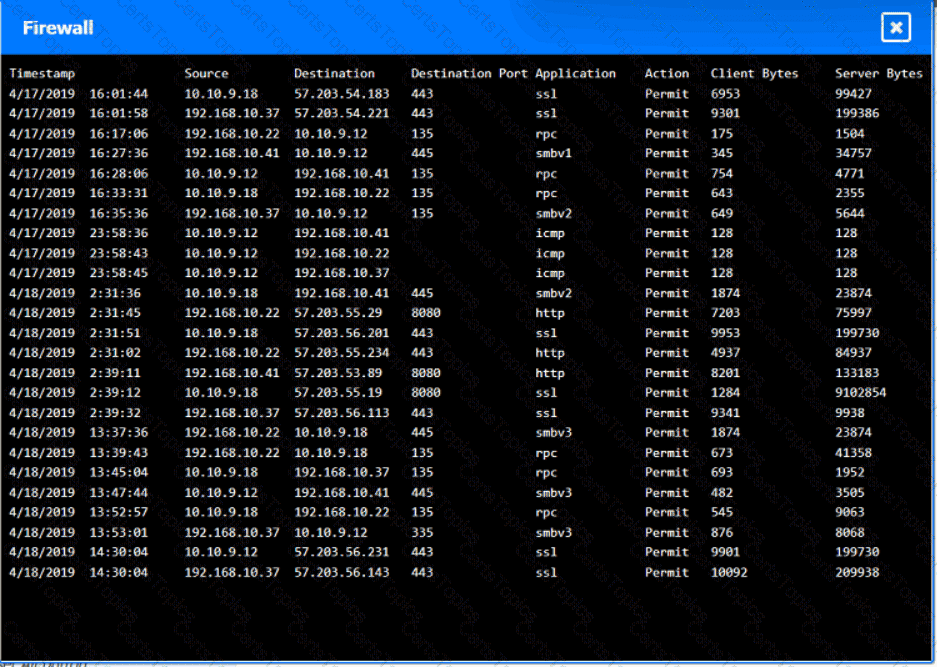
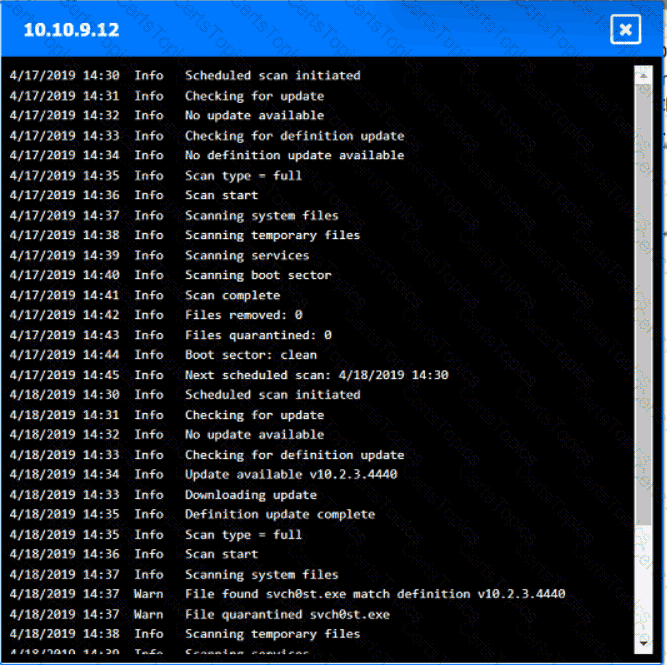
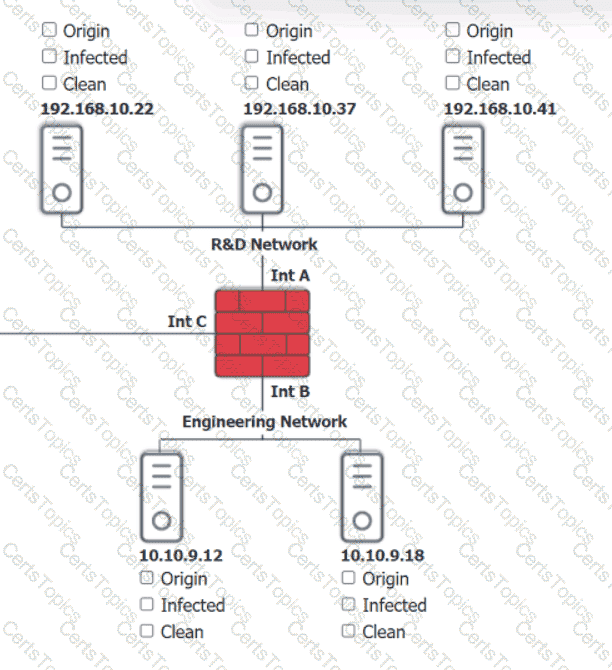
Which of the following provides resilience by hosting critical VMs within different IaaS providers while being maintained by internal application owners?
An organization recently updated its security policy to include the following statement:
Regular expressions are included in source code to remove special characters such as $, |, ;. &, `, and ? from variables set by forms in a web application.
Which of the following best explains the security technique the organization adopted by making this addition to the policy?
Which of the following is the most likely outcome if a large bank fails an internal PCI DSS compliance assessment?
A security analyst is reviewing logs to identify the destination of command-and-control traffic originating from a compromised device within the on-premises network. Which of the following is the best log to review?
Which of the following security measures is required when using a cloud-based platform for loT management?
Which of the following would best prepare a security team for a specific incident response scenario?
Which of the following is the best way to validate the integrity and availability of a disaster recovery site?
A financial institution would like to store its customer data m the cloud but still allow the data to be accessed and manipulated while encrypted. Doing so would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution Is not concerned about computational overheads and slow speeds. Which of the following cryptographic techniques would best meet the requirement?
A service provider wants a cost-effective way to rapidly expand from providing internet links to managing them. Which of the following methods will allow the service provider to best scale its services while maintaining performance consistency?
Which of the following aspects of the data management life cycle is most directly impacted by local and international regulations?
Which of the following is the best way to consistently determine on a daily basis whether security settings on servers have been modified?
A business is expanding to a new country and must protect customers from accidental disclosure of specific national identity information. Which of the following should the security engineer update to best meet business requirements?
A company wants to ensure employees are allowed to copy files from a virtual desktop during the workday but are restricted during non-working hours. Which of the following security measures should the company set up?
While investigating a recent security breach an analyst finds that an attacker gained access by SOL infection through a company website. Which of the following should the analyst recommend to the website developers to prevent this from reoccurring?
A new employee logs in to the email system for the first time and notices a message from human resources about onboarding. The employee hovers over a few of the links within the email and discovers that the links do not correspond to links associated with the company. Which of the following attack vectors is most likely being used?
Which of the following environments utilizes a subset of customer data and is most likely to be used to assess the impacts of major system upgrades and demonstrate system features?
While a user reviews their email, a host gets infected by malware from an external hard drive plugged into the host. The malware steals all the user's credentials stored in the browser. Which of the following training topics should the user review to prevent this situation from reoccurring?
An alert references attacks associated with a zero-day exploit. An analyst places a bastion host in the network to reduce the risk of the exploit. Which of the following types of controls is the analyst implementing?
The analyst wants to move data from production to the UAT server for testing the latest release. Which of the following strategies to protect data should the analyst use?
An administrator assists the legal and compliance team with ensuring information about customer transactions is archived for the proper time period. Which of the following data policies is the administrator carrying out?
Which of the following examples would be best mitigated by input sanitization?
An administrator investigating an incident is concerned about the downtime of a critical server due to a failed drive. Which of the following would the administrator use to estimate the time needed to fix the issue?
In which of the following scenarios is tokenization the best privacy technique 10 use?
A remote employee navigates to a shopping website on their company-owned computer. The employee clicks a link that contains a malicious file. Which of the following would prevent this file from downloading?
Which of the following describes the maximum allowance of accepted risk?
Which of the following is the most likely reason a security analyst would review SIEM logs?
A security manager wants to reduce the number of steps required to identify and contain basic threats. Which of the following will help achieve this goal?
Which of the following is an algorithm performed to verify that data has not been modified?
A security analyst is assessing several company firewalls. Which of the following cools would The analyst most likely use to generate custom packets to use during the assessment?
Which of the following technologies can achieve microsegmentation?
A government worker secretly copies classified files that contain defense tactics information to an external drive. The government worker then gives the external drive to a corrupt organization. Which of the following best describes the motivation of the worker?
A newly identified network access vulnerability has been found in the OS of legacy loT devices. Which of the following would best mitigate this vulnerability quickly?
The management team notices that new accounts that are set up manually do not always have correct access or permissions.
Which of the following automation techniques should a systems administrator use to streamline account creation?
During the onboarding process, an employee needs to create a password for an intranet account. The password must include ten characters, numbers, and letters, and two special characters. Oncethe password is created, the company will grant the employee access to other company-owned websites based on the intranet profile. Which of the following access management concepts is the company most likely using to safeguard intranet accounts and grant access to multiple sites based on a user's intranet account? (Select two).
Which of the following attacks primarily targets insecure networks?
A customer has a contract with a CSP and wants to identify which controls should be implemented in the IaaS enclave. Which of the following is most likely to contain this information?
Which of the following control types describes an alert from a SIEM tool?
The management team wants to assess the cybersecurity team's readiness to respond to a threat scenario. Which of the following will adequately assess and formalize a response within a short time?
A growing organization, which hosts an externally accessible application, adds multiple virtual servers to improve application performance and decrease the resource usage on individual servers Which of the following solutions is the organization most likely to employ to further increase performance and availability?
Which of the following would best allow a company to prevent access to systems from the Internet?
An organization recently started hosting a new service that customers access through a web portal. A security engineer needs to add to the existing security devices a new solution to protect this new service. Which of the following is the engineer most likely to deploy?
A security manager needs an automated solution that will take immediate action to protect an organization against inbound malicious traffic. Which of the following is the best solution?
An organization is leveraging a VPN between its headquarters and a branch location. Which of the following is the VPN protecting?
A systems administrator is concerned users are accessing emails through a duplicate site that is not run by the company. Which of the following is used in this scenario?
Which of the following allows a systems administrator to tune permissions for a file?
A company wants to reduce the time and expense associated with code deployment. Which of the following technologies should the company utilize?
An organization is evaluating the cost of licensing a new solution to prevent ransomware. Which of the following is the most helpful in making this decision?
A company is in the process of cutting jobs to manage costs. The Chief Information Security Officer is concerned about the increased risk of an insider threat. Which of the following would most likely help the security awareness team address this potential threat?
Which of the following should a security analyst consider when prioritizing remediation efforts against known vulnerabilities?
A company is discarding a classified storage array and hires an outside vendor to complete the disposal. Which of the following should the company request from the vendor?
Which of the following describes the reason for using an MDM solution to prevent jailbreaking?
Which of the following would be most useful in determining whether the long-term cost to transfer a risk is less than the impact of the risk?
A company is experiencing issues with employees leaving the company for a competitor and taking customer contact information with them. Which of the following tools will help prevent this from reoccurring?
A company's Chief Information Security Officer (CISO) wants to enhance the capabilities of the incident response team. The CISO directs the incident response team to deploy a tool that rapidlyanalyzes host and network data from potentially compromised systems and forwards the data for further review. Which of the following tools should the incident response team deploy?
A security analyst and the management team are reviewing the organizational performance of a recent phishing campaign. The user click-through rate exceeded the acceptable risk threshold, and the management team wants to reduce the impact when a user clicks on a link in a phishing message. Which of the following should the analyst do?
Which of the following practices would be best to prevent an insider from introducing malicious code into a company's development process?
An administrator implements web-filtering products but still sees that users are visiting malicious links. Which of the following configuration items does the security administrator need to review?
A security administrator needs a method to secure data in an environment that includes some form of checks so that the administrator can track any changes. Which of the following should the administrator set up to achieve this goal?
A company is implementing a policy to allow employees to use their personal equipment for work. However, the company wants to ensure that only company-approved applications can be installed. Which of the following addresses this concern?
Which of the following involves an attempt to take advantage of database misconfigurations?
Malware spread across a company's network after an employee visited a compromised industry blog. Which of the following best describes this type of attack?
A company wants to get alerts when others are researching and doing reconnaissance on the company One approach would be to host a part of the Infrastructure online with known vulnerabilities that would appear to be company assets. Which of the following describes this approach?
Which of the following architecture models ensures that critical systems are physically isolated from the network to prevent access from users with remote access privileges?
A security engineer is implementing FDE for all laptops in an organization. Which of the following are the most important for the engineer to consider as part of the planning process? (Select two).
A new corporate policy requires all staff to use multifactor authentication to access company resources. Which of the following can be utilized to set up this form of identity and access management? (Select two)
Which of the following is the act of proving to a customer that software developers are trained on secure coding?
Which of the following should a systems administrator use to ensure an easy deployment of resources within the cloud provider?
Which of the following phases of the incident response process attempts to minimize disruption?
An employee emailed a new systems administrator a malicious web link and convinced the administrator to change the email server's password. The employee used this access to remove the mailboxes of key personnel. Which of the following security awareness concepts would help prevent this threat in the future?
Two companies are in the process of merging. The companies need to decide how to standardize their information security programs. Which of the following would best align the security programs?
Several employees received a fraudulent text message from someone claiming to be the Chief Executive Officer (CEO). The message stated:
“I’m in an airport right now with no access to email. I need you to buy gift cards for employee recognition awards. Please send the gift cards to following email address.”
Which of the following are the best responses to this situation? (Choose two).
A legal department must maintain a backup from all devices that have been shredded and recycled by a third party. Which of the following best describes this requirement?
Which of the following is the first step to take when creating an anomaly detection process?
An employee clicked a link in an email from a payment website that asked the employee to update contact information. The employee entered the log-in information but received a “page not found” error message. Which of the following types of social engineering attacks occurred?
A company expects its provider to ensure servers and networks maintain 97% uptime. Which of the following would most likely list this expectation?
A company is planning a disaster recovery site and needs to ensure that a single natural disaster would not result in the complete loss of regulated backup data. Which of the following should the company consider?
Which of the following technologies must be used in an organization that intends to automate infrastructure deployment?
A security administrator is reissuing a former employee's laptop. Which of the following is the best combination of data handling activities for the administrator to perform? (Select two).
Which of the following would be the best way to handle a critical business application that is running on a legacy server?
A security analyst is investigating an alert that was produced by endpoint protection software. The analyst determines this event was a false positive triggered by an employee who attempted to download a file. Which of the following is the most likely reason the download was blocked?
During a SQL update of a database, a temporary field used as part of the update sequence was modified by an attacker before the update completed in order to allow access to the system. Which of the following best describes this type of vulnerability?
Which of the following automation use cases would best enhance the security posture of an organization by rapidly updating permissions when employees leave a company?
The Chief Information Security Officer wants to put security measures in place to protect PlI. The organization needs to use its existing labeling and classification system to accomplish this goal. Which of the following would most likely be configured to meet the requirements?
Client files can only be accessed by employees who need to know the information and have specified roles in the company. Which of the following best describes this security concept?
Which of the following activities should be performed first to compile a list of vulnerabilities in an environment?
The Chief Information Security Officer of an organization needs to ensure recovery from ransomware would likely occur within the organization's agreed-upon RPOs end RTOs. Which of the following backup scenarios would best ensure recovery?
A company installed cameras and added signs to alert visitors that they are being recorded. Which of the following controls did the company implement? (Select two).
A bank insists all of its vendors must prevent data loss on stolen laptops. Which of the following strategies is the bank requiring?
Which of the following is the best safeguard to protect against an extended power failure?
An organization has issues with deleted network share data and improper permissions. Which solution helps track and remediate these?
Which of the following is the most likely to be used to document risks, responsible parties, and thresholds?
Which of the following is prevented by proper data sanitization?
Which of the following is a directive managerial control?
A software development manager wants to ensure the authenticity of the code created by the company. Which of the following options is the most appropriate?
The executive management team is mandating the company develop a disaster recovery plan. The cost must be kept to a minimum, and the money to fund additional internet connections is not available. Which of the following would be the best option?
While conducting a business continuity tabletop exercise, the security team becomes concerned by potential impacts if a generator fails during failover. Which of the following is the team most likely to consider in regard to risk management activities?
Which of the following are the most important considerations when encrypting data? (Select two).
Which of the following is a type of vulnerability that refers to the unauthorized installation of applications on a device through means other than the official application store?
A security analyst sees an increase of vulnerabilities on workstations after a deployment of a company group policy. Which of the following vulnerability types will the analyst most likely find on the workstations?
A security administrator recently reset local passwords and the following values were recorded in the system:
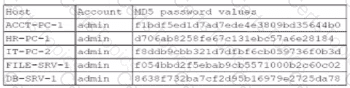
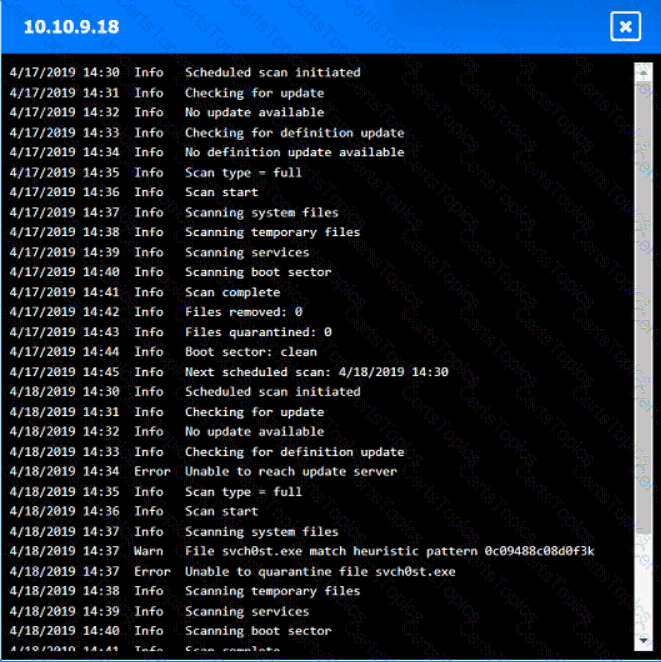
Which of the following in the security administrator most likely protecting against?
Which of the following is used to validate a certificate when it is presented to a user?
Which of the following would most likely be deployed to obtain and analyze attacker activity and techniques?
While considering the organization's cloud-adoption strategy, the Chief Information Security Officer sets a goal to outsource patching of firmware, operating systems, and applications to the chosen cloud vendor. Which of the following best meets this goal?
An administrator is installing an SSL certificate on a new system. During testing, errors indicate that the certificate is not trusted. The administrator has verified with the issuing CA and has validated the private key. Which of the following should the administrator check for next?
A technician is opening ports on a firewall for a new system being deployed and supported by a SaaS provider. Which of the following is a risk in the new system?
Which of the following techniques would identify whether data has been modified in transit?
An organization disabled unneeded services and placed a firewall in front of a business-critical legacy system. Which of the following best describes the actions taken by the organization?
Which of the following should an internal auditor check for first when conducting an audit of the organization's risk management program?
After a recent ransomware attack on a company's system, an administrator reviewed the log files. Which of the following control types did the administrator use?
A Chief Security Officer signs off on a request to allow inbound SMB and RDP from the internet to a single VLAN. Which of the following is the most likely explanation for this activity?
An engineer needs to find a solution that creates an added layer of security by preventing unauthorized access to internal company resources. Which of the following would be the best solution?
An organization is struggling with scaling issues on its VPN concentrator and internet circuit due to remote work. The organization is looking for a software solution that will allow it to reduce traffic on the VPN and internet circuit, while still providing encrypted tunnel access to the data center and monitoring of remote employee internet traffic. Which of the following will help achieve these objectives?
A company that has a large IT operation is looking to better control, standardize, and lower the time required to build new servers. Which of the following architectures will best achieve the company’s objectives?
Which of the following is a reason environmental variables are a concern when reviewing potential system vulnerabilities?
Which of the following strategies should an organization use to efficiently manage and analyze multiple types of logs?
A software developer released a new application and is distributing application files via the developer’s website. Which of the following should the developer post on the website to allow users to verify the integrity of the downloaded files?
Which of the following would most likely prevent exploitation of an end-of-life, business-critical system?
Which of the following would a systems administrator follow when upgrading the firmware of an organization's router?
A security analyst estimates that a small security incident will cost $10,000 and will occur twice per year. The analyst recommends a budget of $20,000 for next year. Which of the following does the $10,000 represent?
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 002.1X for access control. To be allowed on the network, a device must have a Known hardware address, and a valid user name and password must be entered in a captive portal. The following is the audit report:
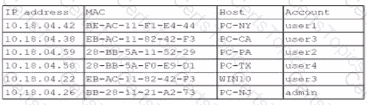
Which of the following is the most likely way a rogue device was allowed to connect?
A security analyst determines that a security breach will have a financial impact of $15,000 and is expected to occur twice within a three-year period. Which of the following is the ALE for this risk?
The Chief Information Security Officer gives the security community the opportunity to report vulnerabilities on the organization’s public-facing assets. Which of the following does this scenario best describe?
A security analyst is reviewing the following logs about a suspicious activity alert for a user's VPN log-ins. Which of the following malicious activity indicators triggered the alert?
✅Log Summary:
User logs in fromChicago, ILmultiple times, then suddenly a successful login appears fromRome, Italy, followed again by Chicago logins — all within ashort time span.
A business received a small grant to migrate its infrastructure to an off-premises solution. Which of the following should be considered first?
The Chief Information Security Officer wants to discuss options for a disaster recovery site that allows the business to resume operations as quickly as possible. Which of the following solutions meets this requirement?
Which of the following is the best reason to perform a tabletop exercise?
A security analyst is investigating an application server and discovers that software on the server is behaving abnormally. The software normally runs batch jobs locally and does not generate traffic, but the process is now generating outbound traffic over random high ports. Which of the following vulnerabilities has likely been exploited in this software?
A software developer would like to ensure. The source code cannot be reverse engineered or debugged. Which of the following should the developer consider?
A company is concerned about the theft of client data from decommissioned laptops. Which of the following is the most cost-effective method to decrease this risk?
Which of the following methods to secure credit card data is best to use when a requirement is to see only the last four numbers on a credit card?
As part of new compliance audit requirements, multiple servers need to be segmented on different networks and should be reachable only from authorized internal systems. Which of the following would meet the requirements?
A government official receives a blank envelope containing photos and a note instructing the official to wire a large sum of money by midnight to prevent the photos from being leaked on the Internet. Which of the following best describes the threat actor's intent?
Which of the following objectives is best achieved by a tabletop exercise?
An employee used a company's billing system to issue fraudulent checks. The administrator is looking for evidence of other occurrences of this activity. Which of the following should the administrator examine?