The Swift user has an sFTP server to push files to an outsourcing agent hosting the Swift users own Communication interface. What is their architecture type?

Which user roles are available in Alliance Cloud by default. (Choose all that apply.)

Penetration testing must be performed at application level against the Swift-related components, such as the interfaces, Swift and customer connectors?

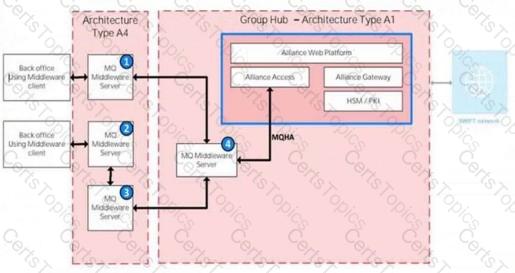
In the illustration, identify the component type of each of the numbered components.

The SWIFT user has installed its own Communication Interface on a dedicated virtual machine offered by a public cloud provider. Under which provider category does the public cloud provider fit, and what is the CSP impact? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
A Swift user uses an application integrating a sFTP client to push files to a service bureau sFTP server What architecture type is the Swift user? (Choose all that apply.)

What are the three main objectives of the Customer Security Controls Framework? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
Is the restriction of Internet access only relevant when having Swift-related components in a secure zone?

Which ones are Alliance Lite2 key components? (Choose all that apply.)

Which statements are correct about the Alliance Access LSO and RSO? (Select the two correct answers that apply)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
Using the outsourcing agent diagram. Which components must be placed in a secure zone? (Choose all that apply.)

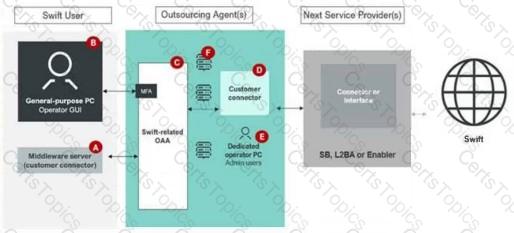
Select the components a SwiftNet Link (SNL) may communicate with. (Choose all that apply.)

The messaging operator in Alliance Lite2… (Select the two correct answers that apply)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
Can a Swift user choose to implement the security controls (example: logging and monitoring) in systems which are not directly in scope of the CSCE?

What does the CSCF expect in terms of Database Integrity? (Select the two correct answers that apply)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
The internet connectivity restriction control prevents having internet access on any CSCE m-scope components.

The control SWIFT Environment Protection supports several objectives. (Select the one that does not apply)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
Must all CSCF controls be subject to an assessment? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
As a Swift CSP Certified Assessor, I left the listed provider and started to work independently. Can I continue to perform CSP assessments?

What are the possible impacts for a SWIFT user to be non-compliant to CSP? (Select the two correct answers that apply)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
A SWIFT user has had part of controls assessed by their internal audit department, and the other remaining controls using an external assessor company. Is this acceptable? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
Which of the following infrastructures has the smallest Swift footprint?

The outsourcing agent of the SWIFT user provided them with an independent assessment report covering the CSP components in their scope, and using the latest CSCF version for testing. Is it enough to support the CSP attestation for the outsourced components? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
A Swift user has moved from one Service Bureau to another What are the obligations of the Swift user in the CSP context?

The SWIFT VPN boxes are located between the Messaging and Communication interface.
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
What are the conditions required to permit reliance on the compliance conclusion of a control assessed in the previous year? (Choose all that apply.)

What type of control effectiveness needs to be validated for an independent assessment?

Which operator session flows are expected to be protected in terms of confidentiality and integrity? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
Which of the following statements best describes the difference between an audit and an assessment as per SWIFT CSP definitions? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
Which statement(s) is/are correct about the LSO/RSO accounts on a Swift Alliance Access? (Choose all that apply.)

The Physical Security control also includes a regular review of physical access lists of the SWIFT-related servers' locations.
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
A SWIFT user owns a customer connector and a communication interface. What architecture type is the SWIFT user? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
What are the key elements that usually need to be considered by a cloud provider in an IaaS cloud model? (Select the two correct answers that apply)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
Which operator session flows are expected to be protected in terms of confidentiality and integrity? (Choose all that apply.)
