Which ones are Alliance Lite2 key components? (Choose all that apply.)

A web interface
An AutoClient
A HSM box
A WebSphere MQ Server
This question identifies the key components of Alliance Lite2 under theSwift Customer Security Programme (CSP).
Step 1: Understand Alliance Lite2 Components
Alliance Lite2 is a browser-based Swift solution for smaller institutions, with a simplified architecture. Its components are detailed in theSwift Alliance Lite2 User Guideand referenced in theCSCF v2024context.
Step 2: Evaluate Each Option
A. A web interfaceThe web interface is the primary user access point for Alliance Lite2, enabling message sending and receiving via a browser. This is a core component, as confirmed in theSwift Alliance Lite2 User Guide.Conclusion: Correct.
B. An AutoClientThe AutoClient is an optional automated client for batch processing and integration with back-office systems, considered a key component for enhanced functionality, per theSwift Alliance Lite2 Technical Documentation.Conclusion: Correct.
C. A HSM boxWhile HSMs are used for cryptographic security in Swift environments, Alliance Lite2 relies on Swift-managed HSM infrastructure, not user-managed HSM boxes. It is not a key user-side component, per theSwift Security Best Practices.Conclusion: Incorrect.
D. A WebSphere MQ ServerWebSphere MQ is a middleware solution not integral to Alliance Lite2, which uses a lightweight architecture without requiring such servers. TheSwift Alliance Lite2 User Guidedoes not list it as a component.Conclusion: Incorrect.
Step 3: Conclusion and Verification
The correct answers areAandB, as the web interface and AutoClient are the key user-side components of Alliance Lite2, consistent with theSwift Alliance Lite2 User GuideandCSCF v2024.
References
Swift Alliance Lite2 User Guide, Section: System Components.
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection.
Swift Alliance Lite2 Technical Documentation, Section: Architecture.
Which statements are correct about the Alliance Access LSO and RSO? (Select the two correct answers that apply)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
They are Alliance Security Officers
Their PKI certificates are stored either on an HSM Token or on an HSM-box
They are the business profiles that can sign the SWIFT financial transactions
They are responsible for the configuration and management of the security functions in the messaging interface
The Local Security Officer (LSO) and Remote Security Officer (RSO) are roles defined within the SWIFT Alliance suite, particularly for managing security in messaging interfaces like Alliance Access. Let’s evaluate each option:
•Option A: They are Alliance Security Officers
This is correct. The LSO and RSO are collectively referred to as Alliance Security Officers within the SWIFT ecosystem. The LSO is typically an on-site officer responsible for local security management, while the RSO can perform similar functions remotely, often for distributed environments. These roles are critical for configuring and maintaining security settings in Alliance Access, as outlined in SWIFT’s operational documentation. The CSCF Control "6.1 Security Awareness" emphasizes the importance of trained security officers, which aligns with the LSO/RSO roles.
•Option B: Their PKI certificates are stored either on an HSM Token or on an HSM-box
This is incorrect. While PKI certificates are used for authentication and are managed within the SWIFT environment, they are not specifically tied to the LSO or RSO roles in terms of storage. PKI certificates for SWIFTNet are stored and managed by the Hardware Security Module (HSM), either as an HSM token (e.g., a smart card) or an HSM-box (e.g., a physical or virtual HSM device). However, these certificates are associated with the SWIFT application or user roles (e.g., for message signing), not the LSO/RSO profiles themselves. The LSO/RSO uses these certificates as part of their duties, but the statement implies ownership or storage, which is inaccurate. CSCF Control "1.3 Cryptographic Failover" specifies HSM management, not LSO/RSO certificate storage.
•Option C: They are the business profiles that can sign the SWIFT financial transactions
This is incorrect. The LSO and RSO are security management roles, not business profiles authorized to sign financial transactions. Signing SWIFT financial transactions (e.g., MT103 messages) is the responsibility of authorized business users or automated processes within Alliance Access, who use PKI certificates managed by the HSM. The LSO/RSO’s role is to configure and oversee security, not to perform transactional activities. This distinction is clear in SWIFT’s role-based access control documentation.
•Option D: They are responsible for the configuration and management of the security functions in the messaging interface
This is correct. The LSO and RSO are tasked with configuring and managing security functions within Alliance Access, such as user access control, authentication settings, and compliance with CSCF requirements. This includes managing PKI certificate usage, setting up secure communication channels, and ensuring the messaging interface adheres to security policies. For example, the LSO can define security profiles and monitor access, as detailed in the Alliance Access Administration Guide, aligning with CSCF Control "2.1 Internal Data Transmission Security."
Summary of Correct Answers:
The LSO and RSO are Alliance Security Officers (A) and are responsible for the configuration and management of security functions in the messaging interface (D). Their PKI certificates are not stored by them, and they do not sign transactions.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Control 6.1 highlights the role of security officers like LSO/RSO.
•SWIFT Alliance Access Documentation: Describes LSO/RSO responsibilities for security configuration.
•SWIFT Security Guidelines: Details PKI certificate management by HSM, not LSO/RSO.
========
Using the outsourcing agent diagram. Which components must be placed in a secure zone? (Choose all that apply.)

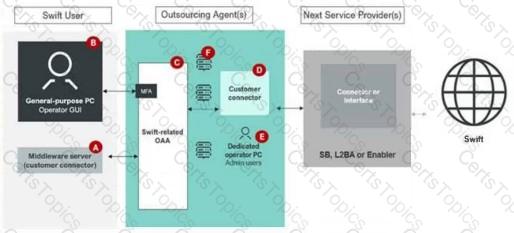
Component A
Component B
Component C
Component D
The diagram provided represents a Swift user environment with an outsourcing agent, showing various components involved in the Swift workflow. The Swift Customer Security Programme (CSP) mandates specific security controls to protect critical components, particularly those handling Swift-related data or connectivity. Let’s analyze the diagram and determine which components must be placed in asecure zoneas per theCSCF v2024.
Step 1: Understand the Secure Zone Requirement
Asecure zonein the Swift CSP context refers to a segregated, protected environment where critical Swift-related components are isolated from general-purpose systems to minimize risks. This is outlined inControl 1.1: Swift Environment Protectionof theCSCF v2024, which mandates that Swift infrastructure (e.g., messaging interfaces, connectors, and related systems) must be logically and physically separated from non-Swift systems. The secure zone ensures that only authorized systems and users can interact with Swift components.
Step 2: Analyze the Diagram and Identify Components
The diagram includes the following components:
A. Middleware server (customer connector): Labeled as Component A, this server facilitates connectivity between the Swift user’s systems and the outsourcing agent’s infrastructure.
B. General-purpose PC Operator GUI: This is a general-purpose system used by an operator to interact with the Swift environment.
C. Swift-related OAA (Operational Application Architecture): Labeled as Component C, this represents the Swift messaging interface (e.g., Alliance Access/Entry) managed by the outsourcing agent.
D. Customer connector: This component, within the outsourcing agent’s environment, interfaces directly with the Swift connector or interface.
E. Dedicated PC Admin users: This represents administrative systems used to manage the Swift environment.Additionally, there’s aConnector or Interface(SB, L2BA, or Enabler) connecting to the Swift network.
Step 3: Determine Which Components Belong in a Secure Zone
A. Middleware server (customer connector):This component facilitates connectivity between the Swift user and the outsourcing agent’s Swift-related systems. According toControl 1.1: Swift Environment Protection, any system that directly interacts with the Swift messaging infrastructure (e.g., as a connector) must reside in a secure zone to prevent unauthorized access or tampering. Since this middleware server is part of the Swift data flow, it must be in a secure zone.Conclusion: Component A must be in a secure zone.
B. General-purpose PC Operator GUI:This is a general-purpose system used by operators, not a core Swift component. TheCSCF v2024underControl 1.2: Logical Access Controlrecommends that operator systems (e.g., GUIclients) should not reside in the same secure zone as critical Swift infrastructure to avoid introducing vulnerabilities from general-purpose systems. These systems typically connect to the secure zone via controlled interfaces (e.g., VPN or jump servers) but are not part of it.Conclusion: Component B does not need to be in a secure zone.
C. Swift-related OAA:This represents the Swift messaging interface (e.g., Alliance Access/Entry), which is a core component of the Swift environment.Control 1.1explicitly requires that messaging interfaces be placed in a secure zone to protect them from external threats and ensure segregation from non-Swift systems. Since this component is directly involved in Swift message processing, it must be in a secure zone.Conclusion: Component C must be in a secure zone.
D. Customer connector:This connector interfaces directly with the Swift connector or interface (SB, L2BA, or Enabler) to facilitate communication with the Swift network. As perControl 1.1, any component that directly connects to the Swift network or handles Swift traffic must be in a secure zone to ensure end-to-end security of the communication chain. This applies to the customer connector within the outsourcing agent’s environment.Conclusion: Component D must be in a secure zone.
E. Dedicated PC Admin users:Administrative systems used to manage the Swift environment are typically not placed in the same secure zone as the operational Swift components. According toControl 1.2: Logical Access Control, administrative access should be tightly controlled and segregated, often using jump servers or bastion hosts to access the secure zone. While these systems need secure access, they are not part of the secure zone itself.Conclusion: Component E does not need to be in a secure zone.
Step 4: Conclusion and Verification
Based on theCSCF v2024requirements, the components that must be placed in a secure zone are those directly involved in Swift message processing or connectivity to the Swift network. These are:
A. Middleware server (customer connector)
C. Swift-related OAA
D. Customer connectorComponent B (general-purpose PC) and Component E (admin PC) are not required to be in the secure zone, as they are operator or administrative systems that should be segregated from the Swift operational environment.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection.
Swift Customer Security Programme – Security Best Practices, Section: Secure Zone Configuration.
CSCF v2024, Control 1.2: Logical Access Control.
Select the components a SwiftNet Link (SNL) may communicate with. (Choose all that apply.)

The Graphical User Interface
The VPN boxes
The HSM device
The messaging interface (such as Alliance Access)
This question identifies the components with which the SwiftNet Link (SNL) communicates, based on its role in the Swift ecosystem under theSwift Customer Security Controls Framework (CSCF) v2024.
Step 1: Understand the Role of SwiftNet Link (SNL)
The SNL is a communication layer that facilitates secure connectivity between a Swift user’s environment and the Swift network. It handles encrypted data transmission and interacts with specific infrastructure components, as detailed in theSwift Alliance Gateway Technical DocumentationandControl 1.1: Swift Environment Protectionof theCSCF v2024.
Step 2: Evaluate Each Option
A. The Graphical User InterfaceThe GUI (e.g., operator interface) is used by personnel to interact with Swift applications (e.g., Alliance Access), but it does not directly communicate with the SNL. The SNL operates at the network and security layer, not the user interface layer, per theSwift User Handbook.Conclusion: Incorrect.
B. The VPN boxesThe SNL communicates with VPN boxes to establish secure tunnels (e.g., using NTLS) for data transmission to the Swift network, as specified in theSwift Security Best PracticesandControl 2.6: Internet Accessibility Restriction.Conclusion: Correct.
C. The HSM deviceThe SNL interacts with the Hardware Security Module (HSM) to manage cryptographic keys and secure communications, as outlined inControl 2.5B: Cryptographic Key Managementand theSwift Alliance Gateway Technical Documentation.Conclusion: Correct.
D. The messaging interface (such as Alliance Access)The SNL connects to the messaging interface (e.g., Alliance Access or Entry) to transmit and receive Swift messages, a core function described in theCSCF v2024underControl 1.1.Conclusion: Correct.
Step 3: Conclusion and Verification
The correct answers areB, C, and D, as the SNL communicates with VPN boxes, HSM devices, and messaging interfaces to ensure secure and functional connectivity to the Swift network, consistent withCSCF v2024and related documentation.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection, Control 2.5B: Cryptographic Key Management, Control 2.6: Internet Accessibility Restriction.
Swift Alliance Gateway Technical Documentation, Section: SNL Communication.
Swift Security Best Practices, Section: Network Infrastructure.
Copyright © 2021-2025 CertsTopics. All Rights Reserved

