Which element is included in an incident response plan as stated m NIST SP800-617
How does agentless monitoring differ from agent-based monitoring?
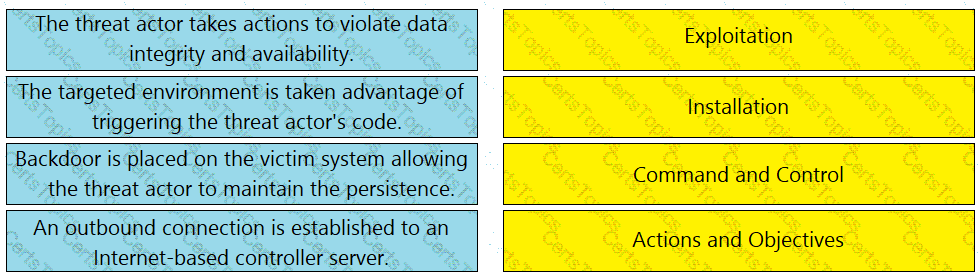
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
What is the purpose of command and control for network-aware malware?