Refer to the exhibit.
What is the potential threat identified in this Stealthwatch dashboard?
Refer to the exhibit.
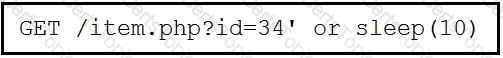
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
An analyst is investigating an incident in a SOC environment. Which method is used to identify a session from a group of logs?
Which tool provides a full packet capture from network traffic?