An incident responder suspects that a host behind a firewall is infected with malware. Which of the following should the responder use to find the IP address of the infected machine?
An incident responder is asked to work with the IT department to address patch management issues with the company servers. Which of the following is the BEST source for the incident responder to obtain the CVEs for the latest industry-recognized patches?
A forensics investigator has been assigned the task of investigating a system user for suspicion of using a company-owned workstation to view unauthorized content. Which of the following would be a proper course of action for the investigator to take?
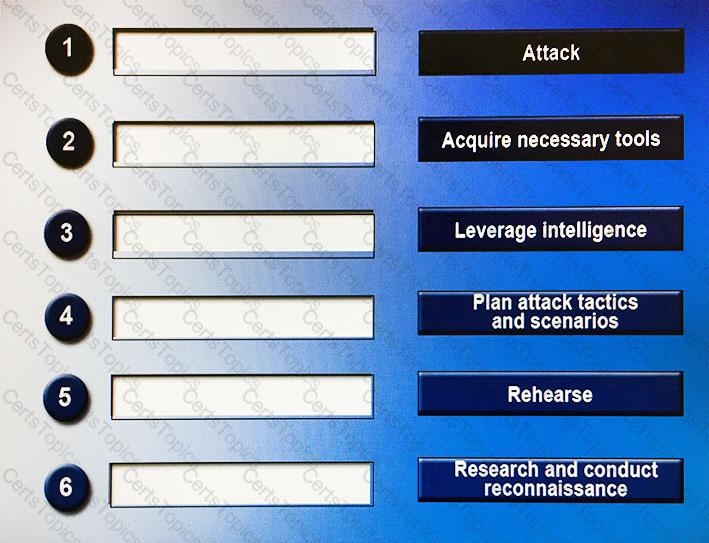
Drag and drop the following steps to perform a successful social engineering attack in the correct order, from first (1) to last (6).