A SOC analyst reviews vendor security bulletins and security blog articles against the company’s deployed system and software base. Based on current attack patterns, three vulnerabilities, including a zero-day vulnerability, have been upgraded to high priority. Which of the following should the SOC analyst recommend? (Choose two.)
An outside organization has reported to the Chief Information Officer (CIO) of a company that it has received attack from a Linux system in the company’s DMZ. Which of the following commands should an incident responder use to review a list of currently running programs on the potentially compromised system?
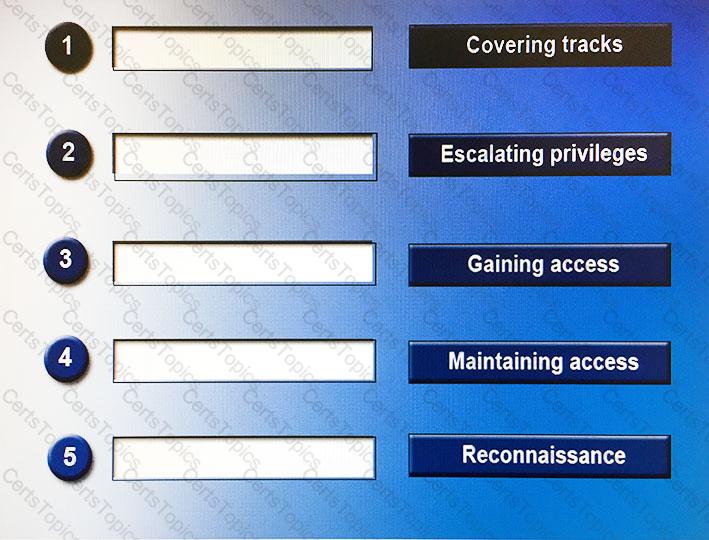
When perpetrating an attack, there are often a number of phases attackers will undertake, sometimes taking place over a long period of time. Place the following phases in the correct chronological order from first (1) to last (5).
Which of the following protocols can be used for data extension?
An incident responder suspects that a host behind a firewall is infected with malware. Which of the following should the responder use to find the IP address of the infected machine?
An incident responder is asked to work with the IT department to address patch management issues with the company servers. Which of the following is the BEST source for the incident responder to obtain the CVEs for the latest industry-recognized patches?
A forensics investigator has been assigned the task of investigating a system user for suspicion of using a company-owned workstation to view unauthorized content. Which of the following would be a proper course of action for the investigator to take?
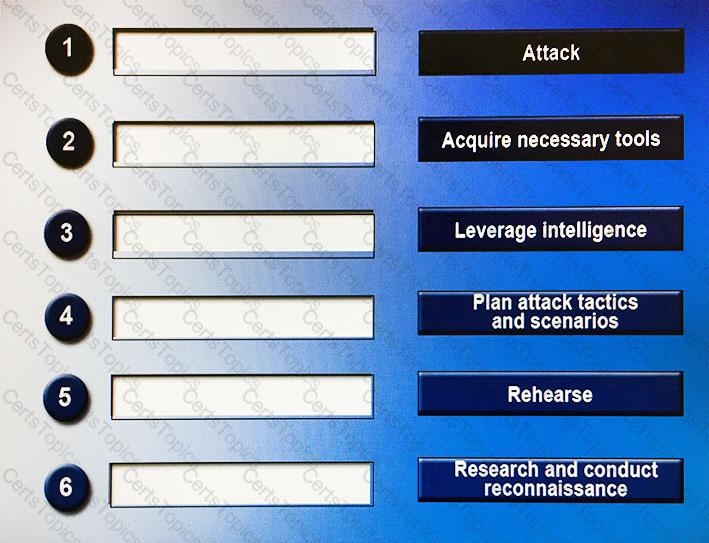
Drag and drop the following steps to perform a successful social engineering attack in the correct order, from first (1) to last (6).
A DMZ web server has been compromised. During the log review, the incident responder wants to parse all common internal Class A addresses from the log. Which of the following commands should the responder use to accomplish this?
Network engineering has reported low bandwidth during working hours. The incident response team is currently investigating several anomalous activities that may be related. Which of the following is the MOST appropriate method to further investigate this problem?
An organization’s firewall has recently been bombarded with an excessive amount of failed requests. A security analyst has been tasked with providing metrics on any failed attempts to ports above 1000. Which of the following regular expressions will work BEST to identify an IP address with the desired port range?
Which of the following technologies is used as mitigation to XSS attacks?
A security analyst would like to parse through several SQL logs for indicators of compromise. The analyst is aware that none of the fields should contain a string of text longer than 30 characters; however, the analyst is unaware if there are any implemented controls to prevent such an overflow. Which of the following BEST describes the regular expression the analyst should use to find any alphanumeric character string?
An organization performs regular updates to its network devices to alert and prevent access to streaming media sites by the employees. Each device will send logs and alerts to a centralized server for storage, archive, and analysis. Which of the following BEST describes the system that is correlating the data found in all alerts and logs?
A security analyst discovers a zero-day vulnerability affecting Windows, which has not been publicly identified. The security analyst assumes this vulnerability is present on millions of computer system and feels an obligation to share this information with other security professionals. Which of the following would be the MOST adverse consequences of the analyst sharing this information?