GIAC Related Exams
GCCC Exam







To effectively implement the Data Protection CIS Control, which task needs to be implemented first?
What is the relationship between a service and its associated port?
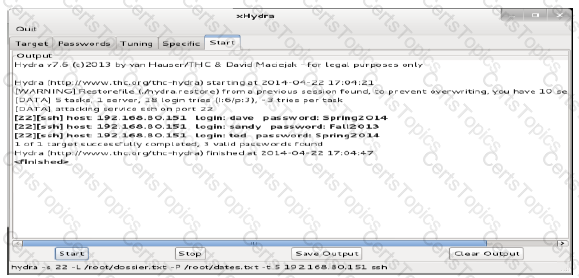
Review the below results of an audit on a server. Based on these results, which document would you recommend be reviewed for training or updates?