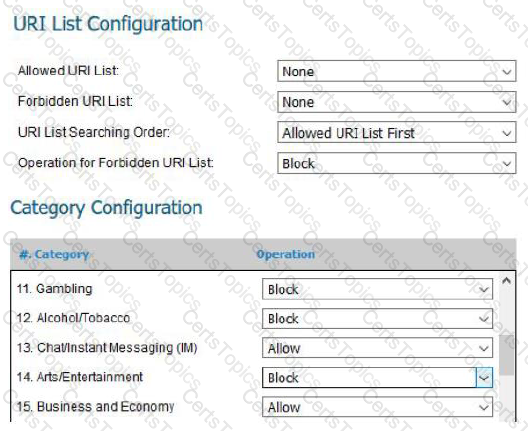
Below is a screenshot from a deployed next-generation firewall. These configuration settings would be a defensive measure for which CIS Control?
What type of Unified Modelling Language (UML) diagram is used to show dependencies between logical groupings in a system?
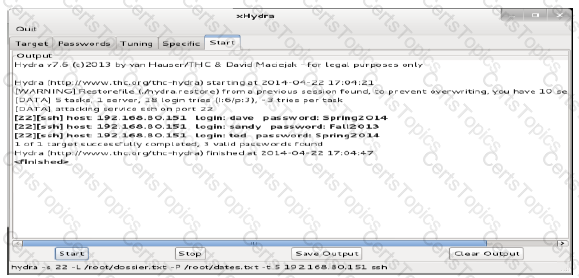
Review the below results of an audit on a server. Based on these results, which document would you recommend be reviewed for training or updates?
An organization has implemented a control for Controlled Use of Administrative Privilege. The control requires users to enter a password from their own user account before being allowed elevated privileges, and that no client applications (e.g. web browsers, e-mail clients) can be run with elevated privileges. Which of the following actions will validate this control is implemented properly?
What is a recommended defense for the CIS Control for Application Software Security?
A security incident investigation identified the following modified version of a legitimate system file on a compromised client:
C:\Windows\System32\winxml.dll Addition Jan. 16, 2014 4:53:11 PM
The infection vector was determined to be a vulnerable browser plug-in installed by the user. Which of the organization’s CIS Controls failed?
Which of the following is necessary to automate a control for Inventory and Control of Hardware Assets?
Allied services have recently purchased NAC devices to detect and prevent non-company owned devices from attaching to their internal wired and wireless network. Corporate devices will be automatically added to the approved device list by querying Active Directory for domain devices. Non-approved devices will be placed on a protected VLAN with no network access. The NAC also offers a web portal that can be integrated with Active Directory to allow for employee device registration which will not be utilized in this deployment. Which of the following recommendations would make NAC installation more secure?
What is the relationship between a service and its associated port?
According to attack lifecycle models, what is the attacker’s first step in compromising an organization?
A need has been identified to organize and control access to different classifications of information stored on a fileserver. Which of the following approaches will meet this need?
To effectively implement the Data Protection CIS Control, which task needs to be implemented first?
What is the first step suggested before implementing any single CIS Control?