Creation of a new custom compliance standard that is based on other individual custom compliance standards needs to be automated.
Assuming the necessary data from other standards has been collected, which API order should be used for this new compliance standard?
Prisma Cloud cannot integrate which of the following secrets managers?
Which two IDE plugins are supported by Prisma Cloud as part of its DevOps Security? (Choose two.)
The InfoSec team wants to be notified via email each time a Security Group is misconfigured. Which Prisma Cloud tab should you choose to complete this request?
The security team wants to enable the “block” option under compliance checks on the host.
What effect will this option have if it violates the compliance check?
A container and image compliance rule has been configured by enabling all checks; however, upon review, the container's compliance view reveals only the entries in the image below.
What is the appropriate action to take next?
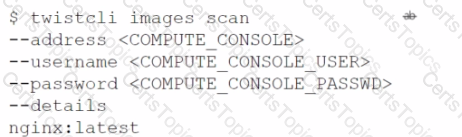
Which API calls can scan an image named myimage: latest with twistcli and then retrieve the results from Console?
Which three serverless runtimes are supported by Prisma Cloud for vulnerability and compliance scans? (Choose three.)
A security team has been asked to create a custom policy.
Which two methods can the team use to accomplish this goal? (Choose two.)
Per security requirements, an administrator needs to provide a list of people who are receiving e-mails for Prisma Cloud alerts.
Where can the administrator locate this list of e-mail recipients?
An administrator has added a Cloud account on Prisma Cloud and then deleted it.
What will happen if the deleted account is added back on Prisma Cloud within a 24-hour period?
What is the function of the external ID when onboarding a new Amazon Web Services (AWS) account in Prisma Cloud?
An administrator for Prisma Cloud needs to obtain a graphical view to monitor all connections, including connections across hosts and connections to any configured network objects.
Which setting does the administrator enable or configure to accomplish this task?
Review this admission control policy:
match[{"msg": msg}] { input.request.operation == "CREATE" input.request.kind.kind == "Pod" input.request.resource.resource == "pods"
input.request.object.spec.containers[_].securityContext.privileged msg := "Privileged"
}
Which response to this policy will be achieved when the effect is set to “block”?
Which two elements are included in the audit trail section of the asset detail view? (Choose two).
Which two statements explain differences between build and run config policies? (Choose two.)
Which method should be used to authenticate to Prisma Cloud Enterprise programmatically?
An administrator of Prisma Cloud wants to enable role-based access control for Docker engine.
Which configuration step is needed first to accomplish this task?
Which command should be used in the Prisma Cloud twistcli tool to scan the nginx:latest image for vulnerabilities and compliance issues?
A)
B)
C)
D)
What is the maximum number of access keys a user can generate in Prisma Cloud with a System Admin role?
Given the following audit event activity snippet:
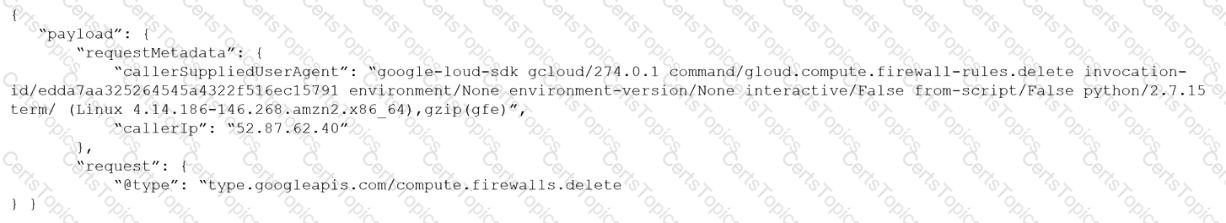
Which RQL will be triggered by the audit event?
A)
B)
C)
D)
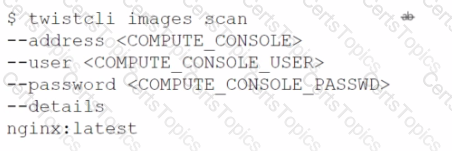
Which command correctly outputs scan results to stdout in tabular format and writes scan results to a JSON file while still sending the results to Console?
Which Prisma Cloud policy type can protect against malware?
A customer has a requirement to terminate any Container from image topSecret:latest when a process named ransomWare is executed.
How should the administrator configure Prisma Cloud Compute to satisfy this requirement?
Which Defender type performs registry scanning?
Which step should a SecOps engineer implement in order to create a network exposure policy that identifies instances accessible from any untrusted internet sources?
Prisma Cloud Compute has been installed on Onebox. After Prisma Cloud Console has been accessed. Defender is disconnected and keeps returning the error "No console connectivity" in the logs.
What could be causing the disconnection between Console and Defender in this scenario?
Which two integrated development environment (IDE) plugins are supported by Prisma Cloud as part of its Code Security? (Choose two.)
Which three incident types will be reflected in the Incident Explorer section of Runtime Defense? (Choose three.)
What are two ways to scan container images in Jenkins pipelines? (Choose two.)
Taking which action will automatically enable all severity levels?
A security team has a requirement to ensure the environment is scanned for vulnerabilities. What are three options for configuring vulnerability policies? (Choose three.)
Match the service on the right that evaluates each exposure type on the left.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
Which type of RQL query should be run to determine if AWS Elastic Compute Cloud (EC2) instances without encryption was enabled?
On which cloud service providers can you receive new API release information for Prisma Cloud?
In Prisma Cloud for Azure Net Effective Permissions Calculation, the following Azure permission levels are supported by which three permissions? (Choose three).
An S3 bucket within AWS has generated an alert by violating the Prisma Cloud Default policy “AWS S3 buckets are accessible to public”. The policy definition follows:
config where cloud.type = 'aws' AND api.name='aws-s3api-get-bucket-acl' AND json.rule="((((acl.grants[? (@.grantee=='AllUsers')] size > 0) or policyStatus.isPublic is true) and publicAccessBlockConfiguration does not exist) or ((acl.grants[?(@.grantee=='AllUsers')] size > 0) and publicAccessBlockConfiguration.ignorePublicAcis is false) or (policyStatus.isPublic is true and publicAccessBlockConfiguration.restrictPublicBuckets is false)) and websiteConfiguration does not exist"
Why did this alert get generated?
What is the frequency to create a compliance report? (Choose two.)
A customer has a requirement to scan serverless functions for vulnerabilities.
What is the correct option to configure scanning?
Which intensity setting for anomaly alerts is used for the measurement of 100 events over 30 days?
A customer wants to harden its environment from misconfiguration.
Prisma Cloud Compute Compliance enforcement for hosts covers which three options? (Choose three.)
Which options show the steps required after upgrade of Console?
Which three options for hardening a customer environment against misconfiguration are included in Prisma Cloud Compute compliance enforcement for hosts? (Choose three.)
Which action would be applicable after enabling anomalous compute provisioning?
The security team wants to target a CNAF policy for specific running Containers. How should the administrator scope the policy to target the Containers?
A customer has a large environment that needs to upgrade Console without upgrading all Defenders at one time.
What are two prerequisites prior to performing a rolling upgrade of Defenders? (Choose two.)
Prisma Cloud supports sending audit event records to which three targets? (Choose three.)
What will happen when a Prisma Cloud Administrator has configured agentless scanning in an environment that also has Host and Container Defenders deployed?
Which type of compliance check is available for rules under Defend > Compliance > Containers and Images > CI?
While writing a custom RQL with array objects in the investigate page, which type of auto-suggestion a user can leverage?
The attempted bytes count displays?
Given the following information, which twistcli command should be run if an administrator were to exec into a running container and scan it from within using an access token for authentication?
• Console is located at
• Token is: TOKEN_VALUE
• Report ID is: REPORTJD
• Container image running is: myimage:latest
The compliance team needs to associate Prisma Cloud policies with compliance frameworks. Which option should the team select to perform this task?
An administrator sees that a runtime audit has been generated for a host. The audit message is:
“Service postfix attempted to obtain capability SHELL by executing /bin/sh /usr/libexec/postfix/postfix- script.stop. Low severity audit, event is automatically added to the runtime model”
Which runtime host policy rule is the root cause for this runtime audit?
What is a benefit of the Cloud Discovery feature?
An administrator wants to install the Defenders to a Kubernetes cluster. This cluster is running the console on the default service endpoint and will be exporting to YAML.
Console Address: $CONSOLE_ADDRESS Websocket Address: $WEBSOCKET_ADDRESS User: $ADMIN_USER
Which command generates the YAML file for Defender install?
What is required for Prisma Cloud to successfully execute auto-remediation commands?
A customer has a requirement to automatically protect all Lambda functions with runtime protection. What is the process to automatically protect all the Lambda functions?
Console is running in a Kubernetes cluster, and you need to deploy Defenders on nodes within this cluster.
Which option shows the steps to deploy the Defenders in Kubernetes using the default Console service name?
The administrator wants to review the Console audit logs from within the Console.
Which page in the Console should the administrator use to review this data, if it can be reviewed at all?
Which two frequency options are available to create a compliance report within the console? (Choose two.)
Which option identifies the Prisma Cloud Compute Edition?
A security team notices a number of anomalies under Monitor > Events. The incident response team works with the developers to determine that these anomalies are false positives.
What will be the effect if the security team chooses to Relearn on this image?
Which two offerings will scan container images in Jenkins pipelines? (Choose two.)
An administrator sees that a runtime audit has been generated for a Container. The audit message is “DNS resolution of suspicious name wikipedia.com. type A”.
Why would this message appear as an audit?
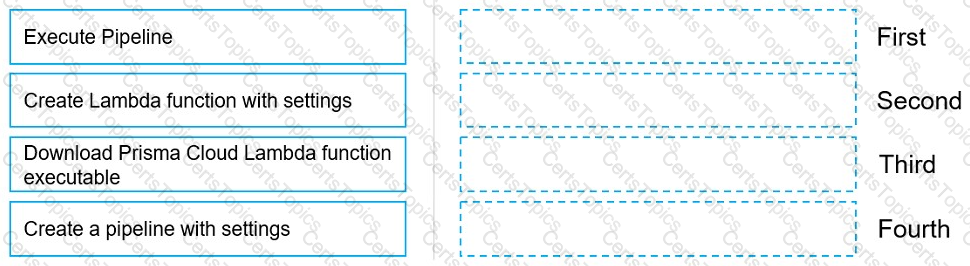
Move the steps to the correct order to set up and execute a serverless scan using AWS DevOps.
What is an automatically correlated set of individual events generated by the firewall and runtime sensors to identify unfolding attacks?
Which two statements apply to the Defender type Container Defender - Linux?
A customer has Prisma Cloud Enterprise and host Defenders deployed.
What are two options that allow an administrator to upgrade Defenders? (Choose two.)
Which serverless cloud provider is covered by the "overly permissive service access" compliance check?
Which report includes an executive summary and a list of policy violations, including a page with details for each policy?
In Azure, what permissions need to be added to Management Groups to allow Prisma Cloud to calculate net effective permissions?
Which policy type should be used to detect and alert on cryptominer network activity?
When an alert notification from the alarm center is deleted, how many hours will a similar alarm be suppressed by default?
What are two built-in RBAC permission groups for Prisma Cloud? (Choose two.)
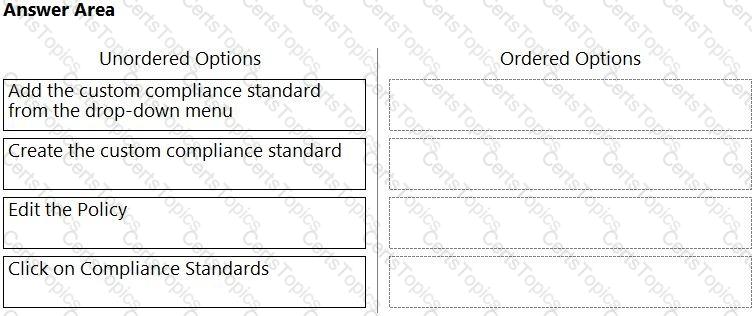
Which order of steps map a policy to a custom compliance standard?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
How many CLI remediation commands can be added in a custom policy sequence?