Which two offerings will scan container images in Jenkins pipelines? (Choose two.)
An administrator sees that a runtime audit has been generated for a Container. The audit message is “DNS resolution of suspicious name wikipedia.com. type A”.
Why would this message appear as an audit?
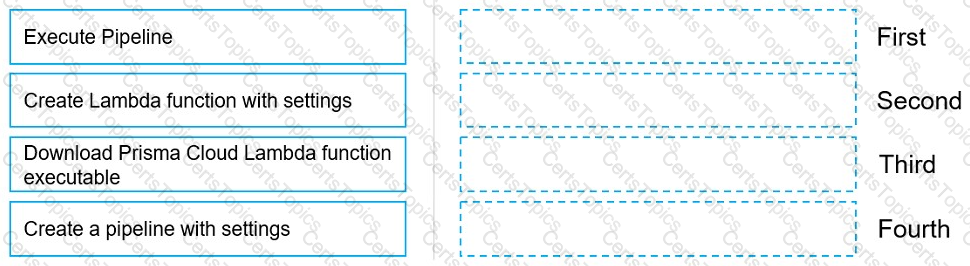
Move the steps to the correct order to set up and execute a serverless scan using AWS DevOps.
What is an automatically correlated set of individual events generated by the firewall and runtime sensors to identify unfolding attacks?