What command is used to add OpenSSH private keys to a running ssh-agen . instance? (Specify the command name only without any path.)
ssh-add
Given the following user's cronlab entry:
15 14 * * 1-5 /usr/local/bin/example.sh be executed?
When will the script /usr/local/bin/example.sh be executed?
At 14:15 local time. January till May.
At 15:14 local time, 1st to 5th day of month.
At 14:15 local time, February till June.
At 14:15 local time, 1st to 5th day of month.
At 14:15 local time, Monday to Friday.
Which directory holds the files that configure the xinetd service when using several configuration files instead of an integrated configuration file? (Specify the full path to the directory.)
/etc/xinetd.d/, /etc/xinetd.d
The /etc/xinetd.d/ directory holds the files that configure the xinetd service when using several configuration files instead of an integrated configuration file. Each file in this directory corresponds to a specific service that is managed by xinetd, such as telnet, ftp, ssh, etc. The name of the file matches the name of the service. The files in this directory contain service-specific options that override or supplement the global options defined in the /etc/xinetd.conf file. The files are read only when the xinetd service is started, so any changes require a restart of the service. The /etc/xinetd.d/ directory allows for a modular and flexible configuration of the xinetd service, as well as easier management and maintenance of the individual service files. References:
How to configure xinetd ? - Red Hat Customer Portal
Understanding /etc/xinetd.d directory under Linux
xinetd - Wikipedia
Which file contains a set of services and hosts that will be allowed to connect to the server by going through a TCP Wrapper program such as tcpd? (Specify the full name of the file, including
/etc/hosts.allow
The /etc/hosts.allow file contains a set of rules that specify which services and hosts are allowed to connect to the server by going through a TCP Wrapper program such as tcpd. TCP Wrappers are a security mechanism that can filter incoming requests based on the source address, destination address, and service name. TCP Wrappers can also perform logging, redirection, and execution of commands based on the rules.
The /etc/hosts.allow file has the following format:
service_list : host_list [ : option_list ]
The service_list is a comma-separated list of service names, such as sshd, telnet, or ftp. The host_list is a comma-separated list of host names, IP addresses, or network masks that are allowed to access the services. The option_list is an optional list of keywords that can modify the behavior of the rule, such as twist, spawn, deny, or allow.
For example, the following rule in /etc/hosts.allow allows ssh access from any host in the 192.168.1.0/24 network, and logs the connection attempt:
sshd : 192.168.1.0/255.255.255.0 : spawn /bin/echo %a from %h attempted to access %d >> /var/log/sshd.log
The /etc/hosts.allow file is processed before the /etc/hosts.deny file, which contains the rules for denying access to the server. If a request matches a rule in /etc/hosts.allow, it is granted access and the processing stops. If it does not match any rule in /etc/hosts.allow, it is checked against the rules in /etc/hosts.deny. If it matches a rule in /etc/hosts.deny, it is denied access and the processing stops. If it does not match any rule in either file, it is granted access by default.
References:
LPI 102-500 Exam Objectives, Topic 110.3: Implement host security
LPI 102-500 Study Guide, Chapter 10: Securing Your System, Section 10.3: TCP Wrappers
hosts.allow man page
Which configuration file contains the default options for SSH clients?
/etc/ssh/sshd_config
/etc/ssh/ssh
/etc/ssh/ssh_config
/etc/ssh/client
/etc/ssh/ssh_client
The configuration file that contains the default options for SSH clients is /etc/ssh/ssh_config. This file is read by the ssh program when it connects to a remote SSH server. It can contain global options that apply to all hosts, or host-specific options that only apply to certain hosts or patterns. The /etc/ssh/ssh_config file is the system-wide default SSH client configuration file. It can be overridden by a user-specific configuration file ~/.ssh/config, which is located in the user’s home directory. The /etc/ssh/ssh_config file is part of the topic 110.1: Perform security administration tasks, which is one of the objectives of the LPI Linux Administrator - 102 exam12. References: 1: LPI Linux Administrator - 102 (LPIC-1) 2: Exam 102 Objectives
What the echo $$ command?
The process ID of the current shell.
The process ID for the following command.
The process ID of the last command executed.
The process ID of the last command which has been placed in the background.
The process ID of the echo command.
The echo command is a built-in Linux feature that prints out arguments as the standard output1. The echo command can take various options and arguments to display different types of information. One of the arguments that can be used with the echo command is $$, which represents the process ID (PID) of the current shell2. A process ID is a unique number that identifies a running process in the system. The current shell is the shell that is executing the echo command. For example, if you are using the Bash shell and run the following command:
echo $$
The output will show the PID of the Bash shell, such as:
1234
The echo
commandcanbeusefultocheckwhichshellyouareusing,ortofindoutthePIDofthecurrentshellfordebuggingormonitoringpurposes.Theecho
command is different from the following commands:
echo $!: This command displays the PID of the last command executed in the background2. A background command is a command that runs without blocking the shell, allowing you to continue using the shell while the command executes. For example, if you run the following command:
sleep 10 &
This command will put the sleep command, which pauses the execution for 10 seconds, in the background. The output will show the PID of the sleep command, such as:
1 2345
If you then run the following command:
echo $!
The output will show the same PID of the sleep command, such as:
2345
echo $?: This command displays the exit status of the last command executed2. The exit status is a number that indicates whether the command was successful or not. A zero exit status means the command was successful, while a non-zero exit status means the command failed or encountered an error. For example, if you run the following command:
ls /home
This command will list the contents of the /home directory. If the command succeeds, the output will show the files and directories in the /home directory, such as:
alice bob charlie
If you then run the following command:
echo $?
The output will show the exit status of the ls command, which is zero, meaning the command was successful:
0
echo $0: This command displays the name of the current shell or script2. The name of the current shell is the name of the executable file that runs the shell, such as bash, zsh, ksh, etc. The name of the current script is the name of the file that contains the script, such as script.sh, script.py, etc. For example, if you are using the Bash shell and run the following command:
echo $0
The output will show the name of the current shell, such as:
bash
References:
2
Which command included in NetworkManager is a curses application which provides easy acces to the NetworkManager on the command line? (Specify only the command without any path or parameters.)
nmtui
The command nmtui is a curses application that provides easy access to the NetworkManager on the command line. It is included in the networkmanager package, along with nmcli, which is another command line interface for NetworkManager. nmtui allows the user to view, edit, activate and deactivate network connections, as well as set the system hostname. It has a simple and user-friendly interface that can be navigated with the keyboard or mouse12. References: 1: Wireless Network Manager command line ncurses GUI. 2: NetworkManager - ArchWiki.
Which of the following programs uses the hosts.allow file to perform its main task of checking for access control restrictions to system services?
tcpd
inetd
fingerd
mountd
xinetd
The tcpd program is a wrapper for network services that use the TCP protocol. It intercepts incoming connection requests and checks them against the rules specified in the /etc/hosts.allow and /etc/hosts.deny files. If the connection is allowed, tcpd executes the actual service program and passes the connection to it. If the connection is denied, tcpd logs the attempt and sends an error message to the client. The tcpd program can be used to enhance the security and control of network access to various services, such as SSH, FTP, Telnet, etc.
The other programs listed are not directly related to the hosts.allow file, although they may be affected by it if they are wrapped by tcpd. The inetd and xinetd programs are super-servers that listen for incoming connections and launch the appropriate service program. The fingerd program is a service that provides information about users on a remote system. The mountd program is a service that handles NFS mount requests from clients. References:
tcpd(8) - Linux man page
Control server access using hosts.allow and hosts.deny files
hosts.allow format and example on Linux
Which of the following connection types, as seen in unroll connection show, may exist in Network Manager? (Choose THREE correct answers.)
tcp
Ethernet
wifi
ipv6
bridge
The connection types, as seen in nmcli connection show, are the types of network configurations that Network Manager can manage. They are not the same as the network protocols or layers, such as TCP or IPv6, but rather the logical or physical ways of connecting to a network. According to the Network Manager reference manual1, some of the possible connection types are:
wifi: This connection type is for wireless network interfaces that use the IEEE 802.11 standard. It requires a wifi device and a wifi access point to establish a connection. The connection settings include the SSID, security, password, etc.
bridge: This connection type is for creating a network bridge, which is a device that connects two or more network segments and forwards packets between them. It requires a bridge device and one or more slave devices to be attached to the bridge. The connection settings include the bridge name, MAC address, STP, etc.
vpn: This connection type is for creating a virtual private network, which is a secure tunnel between two or more network endpoints. It requires a VPN plugin and a VPN service provider to establish a connection. The connection settings include the VPN type, service name, user name, password, etc.
The other options are not correct because:
tcp: This is not a connection type, but a network protocol that operates at the transport layer. It provides reliable, ordered, and error-checked delivery of data between applications. It is not a configuration option for Network Manager.
Ethernet: This is not a connection type, but a network technology that operates at the physical and data link layers. It defines the standards for wiring, signaling, and framing of data packets. It is not a configuration option for Network Manager, but rather a device type that can be used by other connection types, such as bridge or vpn.
ipv6: This is not a connection type, but a network protocol that operates at the network layer. It provides addressing and routing of data packets across networks. It is not a configuration option for Network Manager, but rather an IP configuration option that can be used by other connection types, such as wifi or vpn. References:
If neigher cron, allow nor cron, deny exist in /etc/, which of the following is true?
Without additional configuration, all users may create user specific crontabs.
Without additional configuration, only root may create user specific crontabs.
The aon daemon will refuse to start and report missing files in the system's logfile.
When a user creates a user specific crontab the system administrator must approve it explicitly.
The default settings of /etc/crond.conf define whether or not user specific crontabs are generally allowed or not.
Which of the following statements about sytemd-journald are true? (Choose three.)
It is incompatible with syslog and cannot be installed on a system using regular syslog.
It only processes messages of systemd and not messages of any other tools.
It can pass log messages to syslog for further processing.
It maintains metadata such as _UID or _PID for each message.
It supports syslog facilities such as kern, user, and auth.
systemd-journald is a system service that collects and stores logging data from various sources, such as kernel, user-mode programs, and services1. It creates and maintains structured, indexed journals that include metadata and binary data where necessary1. The journal format is secure and unfakeable1. systemd-journald is not incompatible with syslog and can coexist with it. It can forward log messages to a syslog daemon for further processing, filtering, or storage2. This can be enabled by setting the ForwardToSyslog option to yes in the /etc/systemd/journald.conf file2. systemd-journald does not only process messages of systemd, but also messages of any other tools that use the standard logging interfaces, such as syslog(3), sd_journal_print(3), or systemd-cat(1)1. systemd-journald also supports syslog facilities, such as kern, user, and auth, which are used to specify the type of program that is logging the message3. These facilities can be used to filter the journal entries by using the -p or --priority option of the journalctl command4. For example, to show only kernel messages, we can use journalctl -p kern4. References:
systemd-journald.service
Introduction to the Systemd journal
systemd/Journal
journalctl: Query the systemd Journal
Which command included in systemd supports selecting messages from the systemd journal by criteria such as time or unit name? (Specify only the command without any path or parameters.)
journalctl
The command journalctl is included in systemd and supports selecting messages from the systemd journal by criteria such as time or unit name. The systemd journal is a binary log file that stores system and service messages. The journalctl command can be used to view, filter, export, and manipulate the journal entries. For example, to show all messages from a specific unit, such as sshd.service, the command would be:
journalctl -u sshd.service
To show all messages from a specific time range, such as yesterday, the command would be:
journalctl --since=yesterday
The journalctl command has many options and arguments that can be used to customize the output and perform various operations on the journal. For more information, see the man page of journalctl or the official documentation1. References: [LPI 102-500 Exam Objectives], Topic 106.2: System logging, Weight: 3. [systemd-journald.service(8) — systemd — Debian unstable — Debian Manpages], Section NAME.
Which of the following steps prevents a user from obtaining an interactive login session?
Run the command chsh -s /bin/false with the user name.
Set the UID for the user to 0.
Remove the user from the group staff.
Add the user to /etc/noaccess.
Create a .nologin file in the user's home directory.
Running the command chsh -s /bin/false with the user name will change the user’s login shell to /bin/false, which is a program that does nothing and returns a non-zero exit code. This means that the user will not be able to execute any commands or start an interactive shell session. This is a common way to disable a user’s login without disabling the account completely, which can be useful for users who only need to access the system via scp, sftp, or other non-interactive services. However, this method does not prevent the user from authenticating with the system, and it may not work with some services that do not rely on the login shell, such as ssh with a forced command. Therefore, it is not a foolproof way to secure the system from unauthorized access. References: 1234
What is the purpose of the iconv command?
It converts bitmap images from one format to another such as PNG to JPEG.
It verifies that the root directory tree complies to all conventions from the Filesystem Hierarchy Standard (FHS).
It displays additional meta information from icon files ending in .ico.
It changes the mode of an inode in the ext4 file system.
It converts files from one character encoding to another.
The iconv command is used to convert the encoding of a file from one character set to another. A character set is a collection of characters that are assigned numerical values called code points. Different character sets may use different numbers of bytes to represent each character, and may have different mappings of code points to characters. For example, ASCII is a single-byte character set that encodes 128 characters, while UTF-8 is a variable-length character set that can encode over a million characters. The iconv command can convert between many different character sets, such as ASCII, UTF-8, ISO-8859-1, etc. The basic syntax for using the command is as follows:
iconv [options] -f from-encoding -t to-encoding input-file > output-file
The -f option specifies the encoding of the input file, and the -t option specifies the encoding of the output file. The input file is read from standard input, and the output file is written to standard output, unless specified otherwise. The iconv command can also list all the supported character sets with the -l option1234. References:
How To Use the iconv Command on Linux - How-To Geek
iconv command in Linux with Examples - GeeksforGeeks
iconv - convert file encoding from one character set to another | Linux …
Using iconv to change character encodings - FileFormat.Info
On a system using shadowed passwords, the most correct permissions for /etc/passwd are ___ and the most correct permissions for /etc/shadow are _________.
-rw-r-----, -r--------
-rw-r--r--, -r--r--r--
-rw-r--r--, -r--------
-rw-r--rw-, -r-----r--
-rw-------, -r--------
The /etc/passwd file stores local accounts of the system. It is a readable text file and uses colons (:) to separate the fields. This file helps with converting user IDs to names (and back). It is fine that all users can read this file, but they should not be able to change fields. Therefore, the most correct permissions for /etc/passwd are -rw-r–r–, which means that only the owner (root) can write to the file, and everyone can read it. The /etc/shadow file contains information about the system’s users’ passwords. It is owned by user root and group shadow, and has 640 permissions. The password is stored as a long string of characters, which is a combination of the hashing algorithm, optional salt applied, and the hashed password itself. Other users are not allowed to read the file directly, to prevent them from gathering hashed passwords of others. Therefore, the most correct permissions for /etc/shadow are -r--------, which means that only the owner (root) can read the file, and no one else can read or write to it. References:
In case neither cron.allow nor cron.deny exist in /etc/, which of the following is true?
Without additional configuration, no users may have user specific crontabs.
Without additional configuration, all users may have user specific crontabs.
The cron daemon will refuse to start and report missing files in the system's logfile.
When a user creates a user specific crontab the system administrator must approve it explicitly.
The /etc/cron.allow and /etc/cron.deny files are used to control access to the crontab command and cron jobs for individual users. If neither of these files exists, then depending on site-dependent configuration parameters, only the superuser (root user) will be allowed to use this command, or all users will be able to use this command1. The default behavior of most Linux distributions is to allow all users to use the crontab command and have user specific crontabs if neither /etc/cron.allow nor /etc/cron.deny exists23. Therefore, option B is the correct answer. The other options are not true because:
Option A is false because it contradicts the default behavior of most Linux distributions.
Option C is false because the cron daemon will not refuse to start or report missing files in the system’s logfile if neither /etc/cron.allow nor /etc/cron.deny exists. The cron daemon will start normally and use the default configuration parameters1.
Option D is false because the system administrator does not need to approve user specific crontabs explicitly. The user can create, edit, display, or remove their own crontab files without any intervention from the system administrator1. References:
How cron.allow and cron.deny can be used to limit access to crontab for a particular user | The Geek Search
crontab(1) — cron — Debian bullseye — Debian Manpages
Controlling Access to crontab (System Administration Guide: Basic Administration) - Oracle
/etc/cron.allow - Linux Bash Shell Scripting Tutorial Wiki - nixCraft
Which of the following files assigns a user to its primary group?
/etc/pgroup
/etc/shadow
/etc/group
/etc/passwd
/etc/gshadow
The /etc/passwd file assigns a user to its primary group by specifying the group ID (GID) of the primary group in the fourth field of each line. The /etc/passwd file contains the basic information for each user account on a Linux system, such as the user name, user ID (UID), group ID (GID), home directory, login shell, etc. The format of each line is:
username:password:UID:GID:comment:home:shell
For example, the following line assigns the user bob to the primary group bob, which has the GID of 1001:
bob:x:1001:1001::/home/bob:/bin/sh
The /etc/passwd file can be viewed and modified by the root user or by using the useradd, usermod, or userdel commands123. The other files listed in the options do not assign a user to its primary group. The /etc/pgroup file does not exist by default on most Linux systems, and it is not related to the primary group. The /etc/shadow file contains the encrypted passwords and other information for each user account, but not the primary group4. The /etc/group file contains the information for each group on the system, such as the group name, group password, group ID, and group members, but not the primary group of each user5. The /etc/gshadow file contains the encrypted passwords for group accounts. References: 12345
Which environment variable should be set in order to change the time zone for the commands run from within the environment variable's scope? (Specify the variable name only.)
TZ
The TZ environment variable is used to change the time zone for the commands run from within the environment variable’s scope. It specifies the name of a time zone as defined in the /usr/share/zoneinfo directory or a custom time zone in the POSIX format12. The TZ variable can be set either globally in a shell profile file or locally in a shell session. For example, to set the time zone to America/New_York for the current shell session, one can use the following command:
export TZ=America/New_York
To verify the change, one can use the date command to display the current date and time according to the TZ variable. The TZ variable can also be used to run a single command with a different time zone without affecting the system’s time zone. For example, to run the date command with the Asia/Tokyo time zone, one can use the following syntax:
TZ=Asia/Tokyo date
The TZ variable is useful for testing how applications behave in different time zones or for displaying the time in different locations34. References:
How to Set or Change the Time Zone in Linux | Linuxize
Linux / UNIX: TZ Environment Variable - nixCraft
Get Current System Time Zone in Linux | Baeldung on Linux
Setting the TZ Environment Variable on Linux | InterSystems Developer
How is the file format of /etc/crontab different from a normal crontab file? (Select TWO correct answers)
The /etc/crontab file can specify a year field.
A normal crontab file must be installed with the crontab command.
A normal crontab file allows for environment variable substitution.
The /etc/crontab file has a user field for commands.
The /etc/crontab file is the system-wide crontab file that can be edited only by root. It has a different format from the normal crontab files that can be edited by individual users using the crontab command. The differences are:
The /etc/crontab file can specify a year field as the sixth field in a cron entry. This allows for scheduling jobs that run only in specific years. The normal crontab files do not have a year field and assume the current year for all entries.
The /etc/crontab file has a user field as the seventh field in a cron entry. This allows for running commands as different users from the crontab owner (root). The normal crontab files do not have a user field and run commands as the crontab owner.
The /etc/crontab file does not need to be installed with the crontab command. It is read by the cron daemon automatically. The normal crontab files need to be installed with the crontab command to be recognized by the cron daemon.
The /etc/crontab file and the normal crontab files both allow for environment variable substitution. However, the /etc/crontab file sets some default environment variables such as SHELL, PATH, MAILTO, and HOME, which can be overridden by entries in the file. The normal crontab files inherit the environment variables from the cron daemon, which are usually minimal.
References:
crontab(5) - Linux manual page
Linux Crontab Format
How to schedule a task using Linux crontab (/etc/crontab) file
/etc/crontab - Linux Bash Shell Scripting Tutorial Wiki
Which commands can you use to change a user's account aging information? (Choose THREE correct answers.)
usermod
passwd
chattr
chage
chsh
The commands that can be used to change a user’s account aging information are:
usermod: this command can modify various user account properties, including the password expiration date, the account expiration date, the minimum and maximum password age, the password warning period, and the password inactivity period. To use this command, you need to specify the option and the value for the property you want to change, followed by the username. For example, to set the password expiration date for the user test to February 11, 2022, you can run:
usermod -e 2022-02-11 test
To view the current account aging information for a user, you can use the -l option with the usermod command. For example, to view the information for the user test, you can run:
usermod -l test
passwd: this command can change the password of a user account, as well as some password aging options. To use this command, you need to specify the username and the option for the property you want to change. For example, to change the password of the user test, you can run:
passwd test
To set the maximum password age for the user test to 90 days, you can run:
passwd -x 90 test
To view the current password aging information for a user, you can use the -S option with the passwd command. For example, to view the information for the user test, you can run:
passwd -S test
chage: this command can change the user password expiry and aging information, such as the password expiration date, the account expiration date, the minimum and maximum password age, the password warning period, and the password inactivity period. To use this command, you need to specify the option and the value for the property you want to change, followed by the username. For example, to set the account expiration date for the user test to February 11, 2022, you can run:
chage -E 2022-02-11 test
To view the current account aging information for a user, you can use the -l option with the chage command. For example, to view the information for the user test, you can run:
chage -l test
The other options are incorrect because:
chattr: this command can change the file attributes on a Linux file system, such as making a file immutable, append-only, or undeletable. It has nothing to do with user account aging information.
chsh: this command can change the login shell of a user account, such as bash, zsh, or ksh. It has nothing to do with user account aging information.
References:
How to Manage User Password Expiration and Aging in Linux - Tecmint
Use the Chage Command in Linux
How to set user password expirations on Linux | Enable Sysadmin
How to change password and account expiry options on Linux using chage - Linux Tutorials - Learn Linux Configuration
3 ways to change user password expiration date in Linux - howtouselinux
In which file, if present, must all users be listed that are allowed to use the cron scheduling system? (Specify the full name of the file, including path.)
/etc/cron.allow
The /etc/cron.allow file is a file that contains a list of users who are allowed to use the cron scheduling system. The cron scheduling system is a way of running commands or scripts at specified times or intervals. Users can create their own cron jobs by using the crontab command, which edits a file called crontab that stores the user’s scheduled tasks. However, not all users may have access to the crontab command or the cron system. The access is controlled by two files: /etc/cron.allow and /etc/cron.deny. If the /etc/cron.allow file exists, then only the users listed in this file can use the crontab command and the cron system. The file should have one user name per line. If the /etc/cron.allow file does not exist, then the /etc/cron.deny file is checked. If this file exists, then the users listed in this file are denied access to the crontab command and the cron system. If neither file exists, then the access depends on the configuration of the cron daemon, which is the program that runs the cron jobs. By default, only the root user can use the cron system if no files exist. The root user can always use the cron system regardless of the existence or content of these files. To create or edit the /etc/cron.allow file, the root user needs to use a text editor such as vi, nano, or emacs. For example, to allow the users alice and bob to use the cron system, the root user can use the following command:
sudo vi /etc/cron.allow
And then add the following lines to the file:
alice bob
And then save and exit the file. References:
How cron.allow and cron.deny can be used to limit access to crontab for …
/etc/cron.allow - Linux Bash Shell Scripting Tutorial Wiki
Linux / UNIX Restrict at / cron Usage To Authorized Users
What is true about the file /etc/localtime?
It is a plain text file containing a string such as Europe/Berlin
It is created and maintained by the NTP service based on the location of the system’s IP address.
It is a symlink to /sys/device/clock/ltime and always contains the current local time.
After changing this file, newtzconfig has to be run to make the changes effective.
It is either a symlink to or a copy of a timezone information file such as /usr/share/zoneinfo/Europe/Berlin.
The /etc/localtime file is used to configure the system-wide timezone of the local system that is used by applications for presentation to the user. It should be either a symlink to or a copy of a timezone information file that contains the binary data for the configured timezone. The timezone information files are located under /usr/share/zoneinfo/ and are named after the geographic regions and cities, such as Europe/Berlin or Etc/UTC. The timezone identifier is extracted from the symlink target name of /etc/localtime, so it is recommended to use a symlink rather than a copy. The timezone can be changed by using the timedatectl command or by creating a new symlink to the desired timezone file123. References:
How to Set or Change the Time Zone in Linux | Linuxize
localtime(5) - Linux manual page - man7.org
localtime(5) — Arch manual pages
Which command will set the local machine's timezone to UTC?
cat UTC > /etc/timezone
ln -s /usr/share/zoneinfo/UTC /etc/localtime
date --timezone=UTC
mv /usr/timezone/UTC /etc
The command ln -s /usr/share/zoneinfo/UTC /etc/localtime will create a symbolic link from the file /etc/localtime to the file /usr/share/zoneinfo/UTC, which contains the binary time zone data for the UTC timezone. This will set the system’s timezone to UTC, which is the Coordinated Universal Time, the primary time standard by which the world regulates clocks and time1. The /etc/localtime file is used by various system programs and libraries to determine the local time according to the configured timezone2. The /usr/share/zoneinfo directory contains the time zone information files for different regions and cities around the world3. The other commands are either invalid or will not change the system’s timezone permanently. The command cat UTC > /etc/timezone will overwrite the /etc/timezone file with the string “UTC”, which is not a valid timezone identifier. The /etc/timezone file is a plain text file that contains the name of the timezone, such as “America/New_York” or "Europe/Paris"4. The command date --timezone=UTC will display the current date and time in UTC, but will not change the system’s timezone setting. The command mv /usr/timezone/UTC /etc will move the file /usr/timezone/UTC to the /etc directory, but this file does not exist by default and has no effect on the system’s timezone configuration. References: 1: Coordinated Universal Time - Wikipedia 2: localtime(5) - Linux manual page 3: tz database - Wikipedia 4: How to Change or Set System Locales in Linux - Tecmint : date(1) - Linux manual page : How do I change my timezone to UTC/GMT? - Ask Ubuntu
What is the conventional purpose of Linux UIDs that are lower than 100?
They are reserved for super user accounts.
They are reserved for the system admin accounts.
They are reserved for system accounts.
They are unused, aside from 0, because they are targets of exploits.
They are used to match with GIDs in grouping users.
Linux UIDs (user identifiers) are numbers that are used to identify users and groups on a Linux system. Each user and group has a unique UID and GID (group identifier) respectively. The UID 0 is always reserved for the root or superuser account, which has full privileges to access and modify the system. The UIDs lower than 100 (or 1000 on some modern systems) are typically reserved for system accounts, which are used by various services and daemons that run on the system. These accounts are not meant for human users, but for specific purposes such as managing files, processes, network, security, etc. For example, some common system accounts are bin, daemon, mail, sshd, etc. The UIDs higher than 100 (or 1000) are usually allocated for regular user accounts, which have limited privileges and can be created and deleted by the system administrator. The system accounts are defined in the /etc/passwd file, which contains the username, UID, GID, home directory, shell, and other information for each account12345. References: 1: Linux User Management - Tecmint 2: What are the well-known UIDs? - Stack Overflow 3: user ID less than 1000 on CentOS 7 - Unix & Linux Stack Exchange 4: Recommended GID for users group in Linux (100 or 1000)? - Unix & Linux Stack Exchange 5: What is the conventional purpose of Linux UIDs that are lower than 100? - VCE Guide
Your senior administrator asked you to change the default background of his machine, which uses XDM. Which file would you edit to achieve this?
/etc/X11/xdm/Xsetup
/etc/X11/xdm.conf
/etc/X11/xdm/Defaults
/etc/X11/defaults.conf
The file /etc/X11/xdm/Xsetup contains commands that are executed by XDM before displaying the login screen. This file can be used to set the background image, color, or run other programs on the X display. The other files are either not related to XDM or do not exist by default. References:
XDM - ArchWiki
Customizing the XDM Login Screen | Linux Journal
What is the default name of the configuration file for the Xorg X11 server? (Specify the file name only without any path.)
xorg.conf
The default name of the configuration file for the Xorg X11 server is xorg.conf. This file is used to store initial setup for X, such as settings for video cards, monitors, input devices, and other options. The Xorg X11 server is a display server that uses a configuration file called xorg.conf and files ending in the suffix .conf for its initial setup1. The xorg.conf file is typically located in /etc/X11/xorg.conf, but its location may vary across operating system distributions2. The xorg.conf file is not mandatory, as the Xorg X11 server can automatically configure most hardware and settings. However, it can be created and edited manually if needed3. References:
Xorg - ArchWiki
xorg.conf - Wikipedia
How to Configure X11 in Linux: 10 Steps (with Pictures) - wikiHow
How is a display manager started?
It is started by a user using the command startx.
It is started like any other system service by the init system.
It is started by inetd when a remote hosts connects to the X11 port.
It is started automatically when a X11 user logs in to the system console.
A display manager is a program that provides a graphical login screen for users to access a graphical desktop environment. A display manager is usually started by the init system, which is the first process that runs when the system boots up. The init system is responsible for starting and stopping various system services, including the display manager. The init system can be configured to start a specific display manager by setting the default runlevel or target, or by editing the /etc/X11/default-display-manager file123.
The other options are not correct because:
A. It is started by a user using the command startx. This option is false because the startx command is used to start an X session without a display manager. The startx command launches an X server and runs the user’s .xinitrc or .xsession file, which contains the commands to start the desired desktop environment or window manager. The startx command does not invoke a display manager or a graphical login screen .
C. It is started by inetd when a remote hosts connects to the X11 port. This option is false because inetd is a daemon that listens for incoming network connections and launches the appropriate service for each connection. Inetd does not start a display manager, but it can be used to enable remote access to an X session using the XDMCP protocol. XDMCP stands for X Display Manager Control Protocol, and it allows a remote host to request a graphical login screen from a display manager running on another host. However, this is not the same as starting a display manager, and it requires the display manager to be already running on the host that provides the XDMCP service .
D. It is started automatically when a X11 user logs in to the system console. This option is false because a display manager is not started by a user login, but by the init system. A user login can trigger the start of an X session, but not a display manager. A display manager is independent of the user login, and it can run on multiple virtual consoles or display devices. A display manager can also allow multiple users to log in to different X sessions simultaneously123.
References: 1: LPI Linux Certification/Setup A Display Manager - Wikibooks 2: Working with Display Managers - LPIC-1 102 Linux certification - Linux … 3: How to Change the Default Display Manager in Ubuntu 20.04 : startx - ArchWiki : How to start GUI from command line? - Ask Ubuntu : inetd - Wikipedia : XDMCP - ArchWiki
For accessibility assistance, which of the following programs is an on-screen keyboard?
xkb
atkb
GOK
xOSK
GOK stands for GNOME On-screen Keyboard, and it is a program that provides a virtual keyboard for users who have difficulty using a physical keyboard. GOK is designed to be accessible and customizable, and it supports different keyboard layouts, input methods, and modes. GOK can also generate mouse and gesture events, and it can be controlled by various input devices, such as switches, joysticks, or head trackers. GOK is part of the GNOME desktop environment, and it can be enabled from the Universal Access settings panel123.
The other options are not correct because:
A. xkb is not a program, but a component of the X Window System that handles keyboard configuration and mapping. XKB stands for X Keyboard Extension, and it allows users to define the behavior and appearance of their keyboards, such as the layout, the modifiers, the symbols, and the actions. XKB does not provide an on-screen keyboard, but it can be used by other programs that do45.
B. atkb is not a valid name for any known program or component related to on-screen keyboards. There is no such program or component in the LPI Linux certification program or in the common Linux distributions. The closest match is ATK, which stands for Accessibility Toolkit, and it is a library that provides a set of interfaces for accessibility support in GNOME applications. ATK does not provide an on-screen keyboard, but it can be used by GOK and other programs that do6 .
D. xOSK is a program that provides an on-screen keyboard, but it is not the one that is mentioned in the LPI Linux certification program or in the common Linux distributions. xOSK stands for X On-Screen Keyboard, and it is a simple and lightweight virtual keyboard that can be used with any X11 application. xOSK is not part of any desktop environment, and it has to be installed and launched manually. xOSK is not as accessible and customizable as GOK, and it does not support different input methods or modes .
References: 1: GOK - GNOME Wiki! 2: How to Set Up a Virtual On-Screen Keyboard in Linux 3: Working With On-Screen Keyboards - Oracle Help Center 4: X keyboard extension - Wikipedia 5: XKB Configuration Guide 6: Accessibility Toolkit - GNOME Developer : Accessibility - ArchWiki : xosk - X On-Screen Keyboard : How to use on-screen virtual keyboard on Linux - Xmodulo
What is the purpose of the Sticky Keys feature in X?
To assist users who have difficulty holding down multiple keys at once
To prevent repeated input of a single character if the key is held down
To ignore brief keystrokes according to a specified time limit
To repeat the input of a single character
The Sticky Keys feature in X is an accessibility option that allows users to press modifier keys (such as Ctrl, Alt, Shift, or the Windows key) one at a time, instead of holding them down simultaneously, to perform keyboard shortcuts. For example, to copy something, a user can press Ctrl, release it, and then press C, instead of pressing Ctrl+C together. This can be helpful for users who have difficulty pressing multiple keys at once, or who prefer not to do so. References:
Which of the following are tasks handled by a display manager like XDM or KDM? (Choose TWO correct answers.)
Start and prepare the desktop environment for the user.
Configure additional devices like new monitors or projectors when they are attached.
Handle the login of a user.
Lock the screen when the user was inactive for a configurable amount of time.
Create an X11 configuration file for the current graphic devices and monitors.
The tasks that are handled by a display manager like XDM or KDM are to start and prepare the desktop environment for the user and to handle the login of a user. A display manager is a software component that manages the graphical user interface of an operating system. It provides a login screen where the user can enter their credentials and choose their preferred desktop environment or window manager. After the user is authenticated, the display manager launches the selected desktop environment or window manager and sets up the graphical session. The display manager also handles the logout, shutdown, and reboot of the system.
The other options are incorrect because they are not tasks handled by a display manager:
B. Configure additional devices like new monitors or projectors when they are attached. This task is handled by the X server, which is the core component of the X Window System. The X server is responsible for communicating with the hardware devices, such as the keyboard, mouse, monitor, and graphics card. The X server can detect and configure new devices dynamically using tools like xrandr or xorg.conf.
D. Lock the screen when the user was inactive for a configurable amount of time. This task is handled by the screensaver program, which is a utility that runs in the background and activates when the user is idle for a certain period of time. The screensaver can display various animations or images on the screen, or it can blank the screen entirely. The screensaver can also lock the screen and require the user to enter their password to resume the session. The screensaver can be configured by the user using tools like xscreensaver or gnome-screensaver.
E. Create an X11 configuration file for the current graphic devices and monitors. This task is handled by the X server, which is the core component of the X Window System. The X server can create an X11 configuration file, which is a text file that contains the settings for the X server and the devices it communicates with. The X11 configuration file is usually located at /etc/X11/xorg.conf or /etc/X11/xorg.conf.d/. The X server can generate a default configuration file using the command Xorg -configure, or it can be edited manually by the user or the system administrator. References https://www.baeldung.com/linux/display-managers-explained
On a system running the KDE Display Manager, when is the /etc/kde4/kdm/Xreset script automatically executed?
When KDM starts
When a user's X session exits
When KDM crashes
When X is restarted
When X crashes
The /etc/kde4/kdm/Xreset script is a script that runs as root after a user’s X session exits. It can be used to perform some cleanup tasks or other actions that need to be done when the user logs out of the graphical environment. For example, it can reassign the ownership of the console to root, or shut down the system if desired. The /etc/kde4/kdm/Xreset script is part of the KDE Display Manager (kdm), which is a graphical login manager for X. KDM can be configured to run this script by setting the Reset key in the [X-*-Core] section of the /etc/kde4/kdm/kdmrc configuration file. References:
kdm.options - configuration options for X display manager
kdm(1) — kdm — Debian jessie — Debian Manpages
debian - How to get system to shutdown when Xorg is quit? - Unix …
Why is the xhost program considered dangerous to use?
It makes it difficult to uniquely identify a computer on the network.
It allows easy access to your X server by other users.
It logs sensitive information to syslog.
It makes your computer share network resources without any authentication.
It is a graphical DNS tool with known exploits.
The xhost program is used to add and delete host names or user names to the list allowed to make connections to the X server1. In the case of hosts, this provides a rudimentary form of privacy control and security. It is only sufficient for a workstation (single user) environment, although it does limit the worst abuses1. However, if xhost is used to grant access to everyone, even if they aren’t on the list (i.e., access control is turned off), then any user on the network can connect to your X server and monitor your keystrokes, capture your screen, or run malicious programs2. This is why xhost is considered dangerous to use and should be avoided in favor of more secure methods, such as xauth or ssh23. References:
xhost linux command man page - commandlinux.com
Linux Xhost Command Help and Examples - Computer Hope
xhost(1) — Arch manual pages
What is the purpose of a screen reader?
It reads text displayed on the screen to blind or visually impaired people.
It reads the parameters of the attached monitors and creates an appropriate X11 configuration.
It displays lines and markers to help people use speed reading techniques.
It manages and displays files that contain e-books.
A screen reader is a form of assistive technology that renders text and image content as speech or braille output. Screen readers are essential to people who are blind, and are useful to people who are visually impaired, illiterate, or have a learning disability. Linux has several screen readers available, such as Orca, Speakup, and Emacspeak. These screen readers can help users interact with the graphical or console interface, read documents and web pages, and perform various tasks on the system. References:
Screen reader - Wikipedia
Orca Screen Reader - GNOME
Accessibility in Linux is good (but could be much better)
The X11 configuration file xorg.conf is grouped into sections. How is the content of the section SectionName associated with that section?
It is placed in curly brackets as in Section SectionName { ... }.
It is placed between a line containing Section "SectionName" and a line containing EndSection.
It is placed between the tags
It is placed after the row [SectionName].
It is placed after an initial unindented Section "SectionName" and must be indented by exactly one tab character.
The X11 configuration file xorg.conf is grouped into sections, and the content of the section SectionName is associated with that section by placing it between a line containing Section “SectionName” and a line containing EndSection. For example, the following is a section named ServerLayout that defines the layout of the X server:
Section “ServerLayout” Identifier “X.org Configured” Screen 0 “Screen0” 0 0 InputDevice “Mouse0” “CorePointer” InputDevice “Keyboard0” “CoreKeyboard” EndSection
The other options are incorrect for the following reasons:
A: Curly brackets are not used to delimit sections in xorg.conf. They are used to enclose values that are lists, such as Option “XkbLayout” “{us,fr}”.
C: Tags are not used to delimit sections in xorg.conf. They are used in XML files, which have a different syntax and structure than xorg.conf.
D: Rows are not used to delimit sections in xorg.conf. They are used to define key-value pairs within a section, such as Identifier “Screen0”.
E: Indentation is not required to delimit sections in xorg.conf. It is used to improve readability and clarity, but it does not affect the functionality of the file.
References:
xorg.conf - X Window System
Editing basics for the xorg.conf file - Linux.com
106.1 Lesson 1 - Linux Professional Institute Certification Programs
Which of the following commands shows the current color depth of the X Server?
xcd
xcdepth
xwininfo
xcolordepth
cat /etc/X11
The command that can be used to show the current color depth of the X Server is xwininfo. xwininfo is a command-line tool that provides information about X windows. When executed, it opens a small window and waits for the user to select a window by clicking on it. Then, it displays various characteristics about the window in question, such as its geometry, position, size, depth, class, name, id, and more. The depth value indicates the number of bits per pixel used to represent the colors of the window. xwininfo is part of the X Window System, which is a graphical user interface system for Unix-like operating systems. xwininfo can be useful for debugging, testing, or scripting purposes.
The other options are incorrect because they are either invalid commands or do not show the color depth of the X Server:
xcd is not a valid command in Linux. It may be confused with cd, which is used to change the current working directory.
xcdepth is not a valid command in Linux. It may be confused with xrandr, which is used to change the screen resolution and orientation.
xcolordepth is not a valid command in Linux. It may be confused with xcalib, which is used to load, alter, and query the color profile of the X display.
cat /etc/X11 is not a command, but a directory. cat is used to concatenate files and print them to the standard output. /etc/X11 is a directory that contains configuration files for the X Window System. However, these files do not necessarily show the current color depth of the X Server, as it may be overridden by other settings or options. References:
Which command can be used to investigate the properties for a particular window in X by clicking that window? (Specify ONLY the command without any path or parameters.)
/usr/bin/xwininfo, xwininfo
The command that can be used to investigate the properties for a particular window in X by clicking that window is xwininfo. xwininfo is a command-line tool that provides information about X windows. When executed, it opens a small window and waits for the user to select a window by clicking on it. Then, it displays various characteristics about the window in question, such as its geometry, position, size, depth, class, name, id, and more. xwininfo is part of the X Window System, which is a graphical user interface system for Unix-like operating systems. xwininfo can be useful for debugging, testing, or scripting purposes. References:
You need to pause the CUPS printer HPLaserjet4, and you want to cancel all print jobs with a message, "hello". Which command will do this?
cupsreject -c -r hello HPLaserjet4
cupsreject -p -m hello HPLaserjet4
cupsdisable -c -r hello HPLaserjet4
cupsdisable -p -m hello HPLaserjet4
The command cupsdisable -c -r hello HPLaserjet4 will pause the CUPS printer HPLaserjet4 and cancel all print jobs with a message, “hello”. The cupsdisable command is used to stop printers and classes, while the cupsenable command is used to start them. The -c option cancels all jobs on the named destination, and the -r option sets the message associated with the stopped state. The message will be displayed to the users who try to print to the paused printer. For example, the output of lpstat -p HPLaserjet4 after running the command will show:
printer HPLaserjet4 disabled since Wed 23 Jun 2023 11:54:03 AM UTC -
hello
The other options are not correct. The cupsreject command is used to reject or accept jobs for a printer or class, not to pause or resume them. The -p and -m options are not valid for either cupsdisable or cupsreject. The correct syntax for cupsreject is:
cupsreject [ -E ] [ -U username ] [ -h server [:port] ] [ -r reason ] destination (s)
The -E option forces encryption of the connection to the server, the -U option uses the specified username when connecting to the server, the -h option uses the specified server and port, and the -r option sets the message associated with the rejecting state123. References: 1: cupsdisable(8) - Linux manual page 2: cupsreject(8) - Linux manual page 3: CUPS Administration - Page: 1.4 - Seite 3 » Raspberry Pi Geek
After configuring printing on a Linux server, the administrator sends a test file to one of the printers and it fails to print. What command can be used to display the status of the printer's queue? (Specify ONLY the command without any path or parameters.)
lpq, /usr/bin/lpq, lpstat, /usr/bin/lpstat
The command lpq can be used to display the status of the printer’s queue on a Linux server. The lpq command is part of the cups-bsd package, which provides the Berkeley commands for CUPS (Common UNIX Printing System), the standard printing system for Linux. The lpq command shows the status of a specified printer or the default printer if none is specified. It also lists the jobs that are queued for printing, along with their job IDs, owners, sizes, and names12. For example, to display the status of the printer lp1, we can use the following command:
$ lpq -P lp1
lp1 is ready
Rank Owner Job File(s) Total Size
active user1 123 test.txt 1024 bytes
1st user2 124 report.pdf 2048 bytes
The output shows that the printer lp1 is ready, and that there are two jobs in the queue, one of which is active and the other is waiting. The output also shows the owners, job IDs, file names, and sizes of the jobs. To display the status of all printers, we can use the -a option:
$ lpq -a
lp1 is ready
Rank Owner Job File(s) Total Size
active user1 123 test.txt 1024 bytes
1st user2 124 report.pdf 2048 bytes
lp2 is ready
no entries
The output shows that there are two printers, lp1 and lp2, and that lp2 has no entries in the queue. To display more information about the jobs, such as the priority, submission time, and status, we can use the -l option:
$ lpq -l -P lp1
lp1 is ready
Rank Owner Job File(s) Total Size
active user1 123 test.txt 1024 bytes
priority 50 Apr 27 10:00 processing since Apr 27 10:01
1st user2 124 report.pdf 2048 bytes
priority 50 Apr 27 10:05 waiting for lp1
The output shows that the jobs have the same priority, and that the first job is processing while the second job is waiting. The lpq command can be useful for troubleshooting printing problems, such as checking if the printer is ready, if there are any stuck or failed jobs, or if there are any conflicts or delays in the queue34. References: 1: lpq(1) - Linux manual page 2: How to Use the lp Command in Linux to Print Files From Terminal - Make Tech Easier 3: Linux sysadmin printing reference guide - PenguinTutor 4: How to manage print jobs on Linux - Network World
Which of the following is observed and corrected by a NTP client?
The skew in time between the system clock and the hardware clock.
The skew in time between the system clock and the reference clock.
Changes in the time zone of the current computer's location.
Adjustments needed to support Daylight Saving Time.
The Network Time Protocol (NTP) is a protocol that enables the accurate synchronization of time and date information across networked computer systems. NTP uses a hierarchical system of time servers, where each server has a stratum level that indicates its distance from the primary reference source. The primary reference source is usually an atomic clock or a GPS receiver, which provides the Coordinated Universal Time (UTC). The NTP clients are the computer systems that want to synchronize their system clocks with the UTC. The system clock is a software clock that runs in the kernel and keeps track of the current time and date. The system clock can be influenced by various factors, such as the hardware clock, the CPU frequency, the temperature, the load, and the network latency. These factors can cause the system clock to drift or skew from the UTC, resulting in inaccurate timekeeping. A NTP client observes and corrects the skew in time between the system clock and the reference clock, which is the clock of the NTP server that the client is connected to. The NTP client periodically sends requests to the NTP server and receives the server’s time stamps. The NTP client then calculates the offset and the round-trip delay between its system clock and the reference clock, and adjusts its system clock accordingly. The NTP client can also use multiple NTP servers and apply algorithms to select the best one and filter out outliers. The NTP client can also discipline the system clock by using a feedback loop that controls the clock frequency and reduces the clock drift. By using NTP, the system clock can achieve a high accuracy and precision, usually within a few milliseconds or microseconds of the UTC123.
The other options are not correct. The skew in time between the system clock and the hardware clock is not observed and corrected by a NTP client, but by a separate utility called hwclock, which can read and set the hardware clock. The hardware clock is a battery-powered device that keeps time even when the system is powered off. The hardware clock is usually less accurate than the system clock, and can be synchronized with the system clock at boot or shutdown time. The changes in the time zone of the current computer’s location are not observed and corrected by a NTP client, but by a configuration tool called timedatectl, which can set the system time zone and other parameters. The time zone is a geographical region that has a uniform standard time and date. The time zone does not affect the system clock, which always keeps the UTC, but only the display of the local time and date for the user. The adjustments needed to support Daylight Saving Time (DST) are not observed and corrected by a NTP client, but by the system’s time zone database, which contains the rules and transitions for DST. DST is a practice of advancing the clocks by one hour during summer months to make better use of daylight. DST is not observed in all regions and countries, and can vary in start and end dates. The system’s time zone database is updated regularly to reflect the changes in DST rules, and can be applied to the system clock to calculate the correct local time and date. References: 1: Network Time Protocol - Wikipedia 2: How NTP Works - NTP Pool Project 3: How To Set Up Time Synchronization on Ubuntu 20.042 : hwclock(8) - Linux manual page : timedatectl(1) - Linux manual page : Daylight saving time - Wikipedia
Please specify the top directory containing the configuration files for the CUPS printing system. (Specify the full path to the directory.)
/etc/cups, /etc/cups/
The top directory containing the configuration files for the CUPS printing system is /etc/cups. This directory stores various files that control the behavior and functionality of the CUPS scheduler, cupsd (8), such as cups-files.conf (5), cupsd.conf (5), mime.convs (5), mime.types (5), printers.conf (5), and subscriptions.conf (5). The /etc/cups directory also contains subdirectories for classes, interfaces, ppd, and ssl, which store information about printer classes, device interfaces, printer drivers, and encryption certificates, respectively12. The /etc/cups directory is part of the LPI’s multi-level Linux professional certification program, and it is covered in the topic 105.5 Print service of the exam 102 objectives3. References: 1: cups-files (5) - Linux Manuals 2: cupsd.conf - server configuration file for cups 3: Exam 102 Objectives
Which command is used to sync the hardware clock to the system clock? (Specify ONLY the command without any path or parameters.)
hwclock, /sbin/hwclock, /usr/sbin/hwclock
The command that is used to sync the hardware clock to the system clock is:
hwclock --systohc
This command copies the current system time to the hardware clock, which runs even when the system is shut down. It is equivalent to the command hwclock -w12. The hardware clock is also called the BIOS clock or the RTC (Real Time Clock)3.
Why is the correct configuration of a system's time zone important?
Because the conversion of Unix timestamps to local time relies on the time zone configuration.
Because the time zone is saved as part of the modification times of files and cannot be changed after a file is created.
Because the environment variables LANG and LC_MESSAGES are, by default, set according to the time zone.
Because NTP chooses servers nearby based on the configured time zone.
The correct configuration of a system’s time zone is important because it affects how the system displays and interprets the local time from the Unix timestamps. A Unix timestamp is a number that represents the number of seconds that have elapsed since January 1, 1970 (UTC)1. Unix timestamps are independent of time zones and are the same for all systems1. However, when a system needs to display or interpret the local time from a Unix timestamp, it needs to know the offset from UTC, which is determined by the time zone configuration23. If the time zone configuration is incorrect, the system may display or interpret the local time incorrectly, which can cause problems with scheduling tasks, logs, and other applications45.
For example, suppose a system has a Unix timestamp of 1638374400, which corresponds to December 1, 2021, 12:00:00 UTC6. If the system’s time zone is configured correctly as UTC, it will display the local time as December 1, 2021, 12:00:00. However, if the system’s time zone is configured incorrectly as EST (Eastern Standard Time), which is 5 hours behind UTC, it will display the local time as December 1, 2021, 07:00:00, which is 5 hours earlier than the actual local time6. This can lead to confusion and errors for the system and the user.
Therefore, the correct answer is A. Because the conversion of Unix timestamps to local time relies on the time zone configuration.
References: 1: Unix time - Wikipedia 2: How to Set or Change the Time Zone in Linux – TecAdmin 3: Set the date, time, and timezone on a Linux server 4: Configure the time zone (TZ) on Linux systems - Linux Audit 5: Setting the timezone under Linux - Learn Linux Configuration 6: Epoch Converter - Unix Timestamp Converter
Which file, when using Sendmail or a similar MTA system, will allow a user to redirect all their mail to another address and is configurable by the user themselves?
/etc/alias
~/.alias
/etc/mail/forwarders
~/.forward
~/.vacation
The ~/.forward file is a file that users can create in their home directories to redirect mail or send mail using sendmail or a similar MTA system. The file contains a list of recipient addresses, which can be email addresses, file names, program names, or :include: files. The file must be owned by the user and have the read permission bit set for the owner. The file cannot be a symbolic link or have more than one hard link. The file is processed by sendmail when a recipient address selects a delivery agent with the F=w flag set. If the file contains a backslash, further processing is disabled and the message is delivered to the user’s mail-spooling directory. If the file does not exist or cannot be read, it is silently ignored. The ~/.forward file is different from the /etc/aliases file, which is a system-wide file that maps aliases to one or more recipient addresses. The /etc/aliases file is maintained by the system administrator and requires running the newaliases command after any changes. The ~/.alias file is not a valid file for sendmail or similar MTA systems. The /etc/mail/forwarders file is not a standard file for sendmail or similar MTA systems. The ~/.vacation file is a file that contains a vacation message that is sent to the sender when the user is away. The ~/.vacation file is used in conjunction with the vacation program, which can be invoked from the ~/.forward file. References:
What is the purpose of the command mailq?
It fetches new emails from a remote server using POP3 or IMAP.
It is a multi-user mailing list manager.
It is a proprietary tool contained only in the qmail MTA.
It queries the mail queue of the local MTA.
It is a command-line based tool for reading and writing emails.
The mailq command is a widely used tool for checking the email queue in Linux. It provides a summary of all the messages in the queue, including information such as message IDs, sender addresses, recipient addresses, and delivery status1. The mail queue is a collection of messages that are waiting to be delivered by the local Mail Transfer Agent (MTA), such as sendmail, postfix, or exim1. The mailq command is the same as the sendmail -bp command that also prints the mail queue2. The mailq command can also accept various options to filter or modify the output, such as -v for verbose mode, -Ac for mail submission queue, or -q for processing the queue3. The mailq command is part of the LPI’s multi-level Linux professional certification program, and it is covered in the topic 108.3 Mail Transfer Agent (MTA) basics of the exam 102 objectives4. References: 4: 3: 2: 1:
Which of the following are syslog facilities? (Choose TWO correct answers.)
local5
advanced
postmaster
remote
The syslog facilities are predefined categories of messages that can be used to classify the source and type of the log events12. The syslog facilities are defined by the syslog protocol and are standardized across different implementations of syslog12. The syslog facilities are:
auth: Security and authorization messages, such as login failures or sudo usage12.
authpriv: Same as auth, but used for private security messages that should not be available to all users12.
cron: Messages from the cron daemon, such as scheduled jobs or errors12.
daemon: Messages from system daemons, such as sshd or ntpd12.
kern: Messages from the kernel, such as boot messages or hardware errors12.
lpr: Messages from the line printer subsystem, such as print jobs or errors12.
mail: Messages from the mail subsystem, such as sendmail or postfix12.
news: Messages from the network news subsystem, such as news servers or clients12.
syslog: Messages generated internally by the syslog daemon, such as configuration errors or restarts12.
user: Messages from user-level processes, such as applications or scripts12.
uucp: Messages from the Unix-to-Unix copy subsystem, such as file transfers or errors12.
local0 to local7: Custom facilities that are not used by any system processes and can be assigned to user applications or scripts123.
Therefore, the correct answers are A. local7 and B. mail, as they are both valid syslog facilities. The other options are not syslog facilities and are either made up (C. advanced and E. remote) or refer to a specific process rather than a category of messages (D. postmaster).
References: 1: Prepare for LPIC-1 exam 2 - topic 108.2: System logging - IBM Developer Tutorial 2: 108.2 System logging - Linux Professional Institute Certification Programs 3: What is the local6 (and all other local#) facilities in syslog?
To exclude all log messages of a given logging facility, you should use a logging priority of _____ .
none
To exclude all log messages of a given logging facility, you should use a logging priority of none. This means that no messages from that facility will be logged, regardless of their severity level. For example, if you want to exclude all messages from the local0 facility, you can use local0.none in your syslog configuration file. This will prevent any messages from local0 from being written to any log file or destination that matches that selector12. The logging priority of none is part of the LPI’s multi-level Linux professional certification program, and it is covered in the topic 106.1 System logging of the exam 102 objectives3. References: 1: logging - exclude syslog facility from all others - Server Fault 2: rsyslog.conf(5) - Linux manual page - man7.org 3: Exam 102 Objectives
Which command, available with all MTAs, is used to list the contents of the MTA's mail queue? (Specify ONLY the command without any path or parameters.)
mailq, /usr/bin/mailq, sendmail -bp, /usr/sbin/sendmail -bp, /usr/lib/sendmail -bp, sendmail, /usr/sbin/sendmail, /usr/lib/sendmail
The command that is used to list the contents of the MTA’s mail queue is mailq12. This command is available with all MTAs, such as sendmail, postfix, exim, etc12. The mailq command prints the mail queue, which is the list of messages that are waiting to be sent12. The output of the mailq command shows the queue ID, size, time, sender, and recipient of each message12. The mailq command can also take various options to modify the output, such as -v for verbose mode, -Ac for mail submission queue, -qL for lost items, and -qQ for quarantined items3.
References: 1: mailq Command in Linux with Examples - GeeksforGeeks 2: mailq Command Examples in Linux – The Geek Diary 3: linux - How to see entire sendmail queue? - Server Fault
Which of the following commands is used to rotate, compress, and mail system logs?
rotatelog
striplog
syslogd --rotate
logrotate
logger
The logrotate command is a tool for rotating, compressing, and mailing system logs. It is designed to ease the administration of systems that generate large numbers of log files. It allows automatic rotation, compression, removal, and mailing of log files. Each log file may be handled daily, weekly, monthly, or when it grows too large. Normally, logrotate is run as a daily cron job1. The logrotate command reads the configuration files specified on the command line or in the /etc/logrotate.conf and /etc/logrotate.d directories. These configuration files can set global options and specify log files to rotate and how to handle them. For example, the compress option enables compression of old log files, the mail option sends the log files to a specified email address before being rotated, and the rotate option sets the number of log files to keep12. The logrotate command is part of the LPI’s multi-level Linux professional certification program, and it is covered in the topic 106.1 System logging of the exam 102 objectives3. References: 1: logrotate(8) - Linux man page 2: logrotate command in Linux with examples - Linux command line tutorial 3: Exam 102 Objectives
What is the difference between the commands test -e path and test -f path?
They are equivalent options with the same behaviour.
The -f option tests for a regular file. The -e option tests for an empty file.
Both options check the existence of the path. The -f option also confirms that it is a regular file.
The -f option tests for a regular file. The -e option tests for an executable file.
The test command is used to perform checks and comparisons on files and values. The -e option tests if a given path exists, regardless of its type (file, directory, link, etc.). The -f option tests if a given path exists and is a regular file, not a directory or a special file. For example, if we have a directory named dir and a file named file, we can use the test command as follows:
test -e dir && echo “dir exists” dir exists test -f dir && echo “dir is a regular file” (no output) test -e file && echo “file exists” file exists test -f file && echo “file is a regular file” file is a regular file
References:
Which command allows you to make a shell variable visible to subshells?
export $VARIABLE
export VARIABLE
set $VARIABLE
set VARIABLE
env VARIABLE
The command that allows you to make a shell variable visible to subshells is export VARIABLE. This command turns the variable into a global or environment variable, which means it can be accessed by any child process or subshell that inherits the environment of the parent shell. The syntax of the export command does not require a dollar sign ($) before the variable name, unlike when referencing the value of the variable. The other commands are either invalid or do not affect the visibility of the variable to subshells. The set command can be used to assign values to variables, but it does not export them. The env command can be used to run a command in a modified environment, but it does not change the environment of the current shell. References:
[LPI Linux Essentials - Topic 105: Shells, Scripting and Data Management]
[LPI Linux Professional - Exam 102 Objectives - Topic 105: Shells and Shell Scripting]
What is a Subshell? - Linux Bash Shell Scripting Tutorial Wiki - nixCraft
What is Subshell in Linux? [Explained]
What output will the following command produce?
seq 1 5 20
1
6
1
1
1
6
1
5
10
15
1
2
3
4
2
3
4
5
5
10
15
20
The seq command in Linux is used to generate a sequence of numbers from FIRST to LAST in steps of INCREMENT1. The syntax for the seq command is:
seq [OPTION]… LAST or seq [OPTION]… FIRST LAST or seq [OPTION]… FIRST INCREMENT LAST
In this case, the command seq 1 5 20 has three arguments: FIRST = 1, INCREMENT = 5, and LAST = 20. This means that the command will produce numbers from 1 to 20 in steps of 5. The output will be:
1 5 10 15
The output will not include 20 because it is not a multiple of 5. The output will be printed on separate lines by default, unless a different separator is specified with the -s option2. References:
Seq Command in Linux [Explained With Examples]
seq Man Page - Linux - SS64.com - SS64 Command line reference
What command displays all aliases defined in the current shell? (Specify the command without any path information)
alias, alias -p
The alias command is used to create, list, or remove aliases in the current shell. An alias is a short name that refers to another command, usually with some options or arguments. Aliases are useful for saving typing time, avoiding spelling errors, or customizing the behavior of commands. To list all the aliases defined in the current shell, we can use the alias command without any arguments. This will print the aliases in the format of alias name='command'123. For example:
$ alias alias cp=‘cp -i’ alias l=‘ls -CF’ alias la=‘ls -A’ alias ll=‘ls -alF’ alias mv=‘mv -i’ alias rm=‘rm -i’
The output shows that some common commands, such as cp, mv, and rm, have aliases that add the -i option, which prompts the user before overwriting or deleting files. The l, la, and ll aliases are shortcuts for different variations of the ls command, which lists files and directories123.
References: 1: List All Available Commands and Aliases in Linux - Baeldung 2: get all aliases in linux shell - Stack Overflow 3: How to list all aliases on Linux - Linux Tutorials - Learn Linux Configuration
Which of the following commands puts the output of the command date into the shell variable mydate?
mydate="$(date)"
mydate="exec date"
mydate="$((date))"
mydate="date"
mydate="${date}"
(date)"∗∗ComprehensiveExplanation:∗∗Thecorrectwaytoputtheoutputofthecommanddateintotheshellvariablemydateistousecommandsubstitutionwiththesyntax(command). This will execute the command in a subshell and replace the expression with its standard output. The double quotes around the expression will prevent word splitting and globbing of the output. The other options are incorrect because they will either assign a literal string to the variable, use an invalid syntax, or try to execute the command as an arithmetic expression. References:
[LPI Linux Essentials - Topic 105: Shells, Scripting and Data Management]
[LPI Linux Administrator - Exam 102 Objectives - Topic 105: Shells and Shell Scripting]
Which of the following files, when existing, affect the behavior of the Bash shell? (Choose TWO correct answers.)
~/.bashconf
~/.bashrc
~/.bashdefaults
~/.bash_etc
~/.bash_profile
The Bash shell can be configured by various files that affect its behavior, such as setting environment variables, aliases, functions, options, and prompts. Some of these files are global, meaning they apply to all users of the system, and some are local, meaning they apply to individual users. The global files are usually located in the /etc directory, while the local files are usually located in the user’s home directory, which is denoted by the tilde (~) symbol1.
The local files that affect the Bash shell are:
~/.bash_profile: This file is executed when a user logs in to the system. It is used to set up the user’s environment, such as the PATH, the default editor, the umask, and other variables. It can also run commands that are needed only once per login session, such as ssh-agent or fortune. This file can also source other files, such as ~/.bashrc, to inherit their settings12.
~/.bashrc: This file is executed when a user starts a new interactive shell, such as opening a terminal window or running a script with the shebang #!/bin/bash. It is used to set up the user’s shell preferences, such as aliases, functions, options, and prompts. It can also source other files, such as /etc/bashrc, to inherit their settings12.
~/.bash_logout: This file is executed when a user logs out of the system. It is used to perform any cleanup tasks, such as clearing the screen, deleting temporary files, or printing a farewell message1.
The other files listed in the question are not valid Bash configuration files and do not affect the behavior of the shell. Therefore, the correct answer is B. ~/.bashrc and E. ~/.bash_profile.
References: 1: Bash Shell Configuration Files - Land of Linux 2: Bash Startup Files - GNU Project
Which of the following SQL queries counts the number of occurrences for each value of the field order_type in the table orders?
SELECT order_type,COUNT(*) FROM orders WHERE order_type=order_type;
SELECT order_type,COUNT(*) FROM orders GROUP BY order_type;
COUNT(SELECT order_type FROM orders);
SELECT COUNT(*) FROM orders ORDER BY order_type;
SELECT AUTO_COUNT FROM orders COUNT order_type;
The correct SQL query to count the number of occurrences for each value of the field order_type in the table orders is:
SELECT order_type,COUNT(*) FROM orders GROUP BY order_type;
This query uses the SELECT statement to retrieve the values of the order_type field and the COUNT(*) function to count the number of rows for each order_type. The GROUP BY clause groups the rows by the order_type field, so that the count is calculated for each distinct value of order_type. The result of this query is a table with two columns: order_type and count, where each row shows the number of orders for a specific order_type.
The other options are incorrect for the following reasons:
A: This query uses a WHERE clause that is always true, since order_type=order_type for every row. Therefore, this query returns the same result as SELECT order_type,COUNT(*) FROM orders;, which is a table with one row that shows the total number of orders, regardless of the order_type.
C: This query is syntactically invalid, since the COUNT function cannot take a subquery as an argument. The correct way to use a subquery with COUNT is COUNT((SELECT order_type FROM orders));, which returns the total number of orders, regardless of the order_type.
D: This query uses the ORDER BY clause to sort the rows by the order_type field, but it does not group them by order_type. Therefore, this query returns the same result as SELECT COUNT(*) FROM orders;, which is a table with one row that shows the total number of orders, regardless of the order_type.
E: This query is syntactically invalid, since there is no such function as AUTO_COUNT in SQL, and the COUNT function cannot take a field name as an argument. The correct way to use COUNT with a field name is COUNT(order_type);, which returns the number of non-null values in the order_type field.
References:
[SQL COUNT Function]
[SQL GROUP BY Statement]
[SQL SELECT Statement]
Which of the following is the best way to list all defined shell variables?
env
set
env -a
echo $ENV
The set command is used to display or modify the shell variables and functions in the current shell. When used without any arguments, it prints the names and values of all shell variables, including environment variables and user-defined variables, in alphabetical order. The output also includes the shell options and the positional parameters. The set command can be used in any POSIX-compliant shell, such as bash, zsh, ksh, etc123.
The other options are not correct because:
env is used to print or modify the environment variables, not the shell variables. It does not show the user-defined variables or the shell options. It can also be used to run a command in a modified environment45.
env -a is an invalid option for the env command. The -a option is not supported by the env command in any standard or common implementation45.
echo $ENV is used to print the value of the environment variable ENV, not the list of all shell variables. The ENV variable is usually set to the name of a file that contains commands or aliases to be executed by the shell. It is mainly used by the ksh and some versions of bash .
References: 1: How can I list all shell variables? - Unix & Linux Stack Exchange 2: 2.1 Command Line Basics - Linux Professional Institute Certification … 3: set - The Open Group Base Specifications Issue 7, 2018 edition 4: How to set and list environment variables on Linux 5: env - The Open Group Base Specifications Issue 7, 2018 edition : What is the difference between .bash_profile and .bashrc? - Unix & Linux Stack Exchange : ENV - The Open Group Base Specifications Issue 7, 2018 edition
What is the purpose of the file /etc/profile?
It contains the welcome message that is displayed after login.
It contains security profiles defining which users are allowed to log in.
It contains environment variables that are set when a user logs in.
It contains default application profiles for users that run an application for the first time.
The file /etc/profile is a configuration file that is read by the Bash shell when a user logs in. It contains commands and settings that apply to all users of the system, such as environment variables, PATH information, terminal settings, and security commands. Environment variables are variables that affect the behavior of programs and processes. For example, the PATH variable defines the directories where the shell looks for executable files, and the JAVA_HOME variable defines the location of the Java installation. The /etc/profile file can also source other files from the /etc/profile.d/ directory, which can contain additional scripts for setting environment variables or other system-wide settings. The /etc/profile file is not the only file that can set environment variables for a user. There are also user-specific files, such as ~/.profile, ~/.bash_profile, and ~/.bashrc, that are read by the shell after /etc/profile. These files can override or append to the settings in /etc/profile, or define new variables for the user. The order and precedence of these files depend on the type of shell (login or interactive) and the options used to start the shell. You can learn more about the difference between these files here1 and here2. References: https://www.thegeekdiary.com/understanding-etc-profile-configuration-file-in-linux/
What output will the command seq 10 produce?
A continuous stream of numbers increasing in increments of 10 until stopped.
The numbers 1 through 10 with one number per line.
The numbers 0 through 9 with one number per line.
The number 10 to standard output.
The seq command in Linux is used to print a sequence of numbers, which can be piped to other commands or used in for loops and bash scripts1. The command can generate a list of integers or real numbers, with options to control the start, end, and increment of the sequence. The general syntax of the command is seq [options] specification1.
If you launch seq with a single number as a command-line parameter, it counts from one to that number. It then prints the numbers in the terminal window, one number per line2. For example, seq 10 will produce the following output:
1
2
3
4
5
6
7
8
9
10
Therefore, the correct answer is B. The numbers 1 through 10 with one number per line.
References: 1: 10+ Seq Commands with Examples in Linux – LinuxWizardry 2: How to Use the seq Command on Linux - How-To Geek
Which of the following words is used to restrict the records that are returned from a SELECT SQL query based on a supplied criteria for the values in the records?
CASE
FROM
WHERE
IF
The SQL WHERE clause is used to restrict the records that are returned from a SELECT SQL query based on a supplied criteria for the values in the records12. The WHERE clause follows the SELECT and FROM clauses and contains one or more conditions that must be true for a record to be included in the result set. The general syntax of the WHERE clause is:
SELECT column1, column2, ...
FROM table_name
WHERE condition;
The condition can be a comparison, a logical operation, a pattern matching, a subquery, or a combination of these using various operators12. For example, the following query selects all the records from the customers table where the country is ‘USA’:
SELECT * FROM customers
WHERE country = 'USA';
The other words listed in the question are not used to filter records based on values. They have different meanings and purposes in SQL:
CASE: This is a conditional expression that returns a value based on a set of conditions3. It can be used in SELECT, UPDATE, DELETE, or WHERE statements. For example, the following query uses a CASE expression to assign a rating to each customer based on their credit limit:
SELECT customer_name, credit_limit, CASE WHEN credit_limit > 10000 THEN ‘High’ WHEN credit_limit > 5000 THEN ‘Medium’ ELSE ‘Low’ END AS rating FROM customers;
FROM: This is a clause that specifies the table (s) or view (s) from which the data is retrieved. It follows the SELECT clause and precedes the WHERE clause. For example, the following query selects the customer name and order date from the customers and orders tables:
SELECT customer_name, order_date FROM customers JOIN orders ON customers.customer_id = orders.customer_id;
IF: This is a control flow statement that executes a block of code based on a condition. It can be used in stored procedures, functions, triggers, or batch files. For example, the following code snippet uses an IF statement to check if a variable is positive or negative:
DECLARE @num INT; SET @num = -10; IF @num > 0 BEGIN PRINT ‘Positive’; END ELSE BEGIN PRINT ‘Negative’; END
References: 1: SQL WHERE Clause - W3Schools 2: How to Write a WHERE Clause in SQL | LearnSQL.com 3: [SQL CASE Statement - W3Schools] : [SQL FROM Clause - W3Schools] : [SQL IF…ELSE Statement - W3Schools]
When the command echo $ outputs 1, which of the following statements is true?
It is the process ID of the echo command.
It is the process ID of the current shell.
It is the exit value of the command executed immediately before echo.
It is the exit value of the echo command.
The $? variable in bash is a special parameter that holds the exit status of the last command executed in the current shell. The exit status is a numerical value that indicates whether the command was successful (zero) or failed (non-zero). The echo command simply prints its arguments to the standard output. Therefore, when the command echo $? outputs 1, it means that the previous command failed with an exit status of 1. References:
[LPI Linux Essentials - Topic 103: Command Line Basics]
[Bash Special Parameters]
[Exit status - Wikipedia]
Which of the following IPv4 networks are reserved by IANA for private address assignment and private routing? (Choose THREE correct answers.)
127.0.0.0/8
10.0.0.0/8
169.255.0.0/16
172.16.0.0/12
192.168.0.0/16
According to the RFC 19181, the Internet Assigned Numbers Authority (IANA) has reserved the following three blocks of the IPv4 address space for private internets:
10.0.0.0 - 10.255.255.255 (10/8 prefix)
172.16.0.0 - 172.31.255.255 (172.16/12 prefix)
192.168.0.0 - 192.168.255.255 (192.168/16 prefix)
These address blocks are not globally routable and are intended for use within private networks, such as home, office, or campus networks. They can be assigned to any device that does not need to communicate directly with the public internet, or that can use network address translation (NAT) to do so. Private addresses allow for more efficient use of the limited IPv4 address space and reduce the need for public addresses.
The other options are not reserved for private use by IANA. Option A, 127.0.0.0/8, is reserved for loopback addresses, which are used to refer to the local host. Option C, 169.255.0.0/16, is a typo and should be 169.254.0.0/16, which is reserved for link-local addresses, which are used for automatic address configuration on a local network segment. Option F, 224.0.0.0/4, is reserved for multicast addresses, which are used for one-to-many communication.
References:
RFC 1918: Address Allocation for Private Internets - RFC Editor
IANA IPv4 Special-Purpose Address Registry
Private network - Wikipedia
Which of the following is true about IPv6?
With IPv6, the TCP port numbers of most services have changed.
IPv6 no longer supports broadcast addresses.
IPv4 addresses can be used without any change with IPv6.
IPv6 no longer supports multicast addresses.
For IPv6, UDP and TCP have been replaced by the Rapid Transmission Protocol RTP.
Broadcast addresses are used to send a message to all devices on a network segment. IPv4 supports broadcast addresses, but IPv6 does not. Instead, IPv6 uses multicast addresses, which are used to send a message to a group of devices that have joined a multicast group. Multicast addresses are more efficient and flexible than broadcast addresses, as they allow the sender to specify the recipients more precisely and avoid unnecessary network traffic. IPv6 also supports anycast addresses, which are used to send a message to the nearest device that provides a specific service. Anycast addresses are useful for load balancing and redundancy. References:
[LPI Linux Administrator - Exam 102 Objectives - Topic 109: Networking Fundamentals]
IPv6 - Features - Online Tutorials Library
IPv6 - Wikipedia
Which command, depending on its options, can display the open network connections, the routing tables, as well as network interface statistics. (Specify ONLY the command without any path or parameters.)
netstat, /bin/netstat, ss, /usr/bin/ss
The netstat command, meaning network statistics, is a command-line utility in the Linux system to display network configuration and activity, including network connections, routing tables, interface statistics, masquerade connections, and multicast memberships1. The netstat command can display different types of network data depending on the command line option selected. Some of the common options are:
-a: This option displays active TCP connections, TCP connections with the listening state, as well as UDP ports that are being listened to.
-r: This option displays the routing table information, which is a list of rules that determine where the packets are sent.
-i: This option displays the network interface information, such as the name, MTU, RX-OK, TX-OK, etc.
-s: This option displays the network statistics by protocol, such as TCP, UDP, ICMP, IP, etc.
For example, to display the open network connections, one can run:
netstat -a
To display the routing table, one can run:
netstat -r
To display the network interface statistics, one can run:
netstat -i
To display the network statistics by protocol, one can run:
netstat -s
For more details and examples, please refer to the web search results1 or the question answering results2. References:
What is true regarding a default route?
The default route is always used first. When the default route is not available more specific routes are tried.
When a default route is set, all other routes are disabled until the default route is deleted.
The default route is only used if there is not a more specific route to a destination host or network.
Without a default route, no network communication even in directly attached networks is possible.
A default route is a special type of route that specifies where to send packets when there is no explicit route for the destination in the routing table. A default route is usually configured on a router or a gateway that connects to another network, such as the internet. A default route is often represented by the destination 0.0.0.0/0, which means any IP address.
A default route is not always used first. It is only used as a last resort, when there is no more specific route for the destination. For example, if a host wants to send a packet to 192.168.1.10, and the routing table contains the following entries:
Destination Gateway Genmask Flags Metric Ref Use Iface 192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0 0.0.0.0 192.168.1.1 0.0.0.0 UG 0 0 0 eth0
The host will use the first entry, which is more specific, and send the packet directly to 192.168.1.10 via eth0 interface. The second entry, which is the default route, will not be used in this case. However, if the host wants to send a packet to 8.8.8.8, which is not in the same network, the host will use the default route and send the packet to 192.168.1.1, which is the gateway to the internet.
Setting a default route does not disable other routes. It only adds an entry to the routing table that can be used when no other route matches the destination. Other routes are still valid and can be used if they are more specific.
Without a default route, network communication in directly attached networks is still possible, as long as there are routes for those networks in the routing table. However, network communication to other networks that are not directly connected will not be possible, unless there are specific routes for those networks in the routing table.
References:
How to Set the Default Gateway in Linux - How-To Geek
Linux setup default gateway with route command - nixCraft
How to set a default route permanently in Linux - Xmodulo
Which parameter must be passed to ifconfig to activate a previously inactive network interface? (Specify the parameter only without any command, path or additional options)
up
The parameter that must be passed to ifconfig to activate a previously inactive network interface is up. The up parameter tells the kernel to activate the network interface and allow it to send and receive packets. The opposite of up is down, which deactivates the network interface. The up parameter is part of the topic 109.2: Basic network configuration, which is one of the objectives of the LPI Linux Administrator - 102 exam12. References: 1: 2:
Given the following routing table:
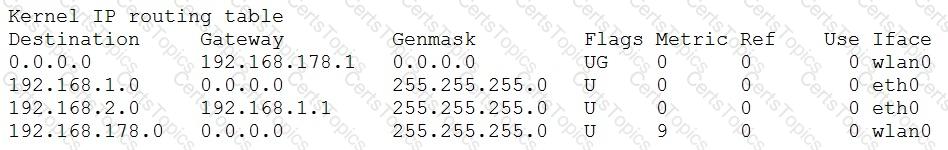
How would an outgoing packet to the destination 192.168.2.150 be handled?
It would be passed to the default router 192.168.178.1 on wlan0.
It would be directly transmitted on the device eth0.
It would be passed to the default router 255.255.255.0 on eth0.
It would be directly transmitted on the device wlan0.
It would be passed to the router 192.168.1.1 on eth0.
The routing table shows how the kernel will route packets to different destinations based on the destination IP address, the gateway, the netmask, the flags, the metric, and the interface. The kernel will try to find the most specific route that matches the destination IP address, which means the route with the longest netmask. If there are multiple routes with the same netmask, the kernel will use the route with the lowest metric. If there is no matching route, the kernel will use the default route, which is the route with the destination 0.0.0.0.
In this case, the destination IP address is 192.168.2.150, which belongs to the network 192.168.2.0/24. The routing table has a specific route for this network, which is the second entry. The gateway for this route is 0.0.0.0, which means that the packet will be directly transmitted on the interface eth0, without passing through any router. The netmask for this route is 255.255.255.0, which means that the network has 256 possible hosts. The flags for this route are U, which means that the route is up, and G, which means that the route is to a gateway. The metric for this route is 0, which means that it has the highest priority. Therefore, the kernel will use this route to handle the outgoing packet to the destination 192.168.2.150.
References:
How To Display Routing Table In Linux - RootUsers
route command in Linux with Examples - GeeksforGeeks
Understand the basics of Linux routing | TechRepublic
Which keyword must be listed in the hosts option of the Name Service Switch configuration file in order to make host lookups consult the /etc/hosts file?
files
The keyword files must be listed in the hosts option of the Name Service Switch configuration file in order to make host lookups consult the /etc/hosts file. The files service specifies that the local files, such as /etc/hosts, should be used as a source of information. The order of the services on the line determines the order in which those services will be queried, in turn, until a result is found. For example, if the hosts option is set to:
hosts: files dns
then the /etc/hosts file will be searched first, and if no match is found, the DNS server will be queried next. If the hosts option is set to:
hosts: dns files
then the DNS server will be queried first, and if no match is found, the /etc/hosts file will be searched next. References:
LPI 102-500 Exam Objectives, Topic 110: Network Fundamentals, Weight: 4, 110.3 Basic network troubleshooting
LPI 102-500 Study Guide, Chapter 10: Network Fundamentals, Section 10.3: Basic Network Troubleshooting, Page 125-126
nsswitch.conf: Name Service Switch configuration file
How many IP-addresses can be used for unique hosts inside the IPv4 subnet 192.168.2.128/28? (Specify the number only without any additional information.)
14
To find the number of IP-addresses that can be used for unique hosts inside an IPv4 subnet, we need to calculate the number of bits that are used for the host part of the IP address. The host part is the part that is not used for the network prefix, which is indicated by the slash notation (/) followed by a number. The number after the slash represents the number of bits that are used for the network prefix, out of the total 32 bits of an IPv4 address. The remaining bits are used for the host part. For example, in the subnet 192.168.2.128/28, the number 28 means that the first 28 bits are used for the network prefix, and the last 4 bits are used for the host part.
The number of IP-addresses that can be used for unique hosts is equal to 2^n - 2, where n is the number of bits in the host part. The -2 is because the first and the last IP addresses in a subnet are reserved for the network address and the broadcast address, respectively, and cannot be assigned to hosts. Therefore, in the subnet 192.168.2.128/28, the number of IP-addresses that can be used for unique hosts is 2^4 - 2, which is 14.
References:
IPv4 - Subnetting - Online Tutorials Library
IP Subnet Calculator
Which of the following programs can be used to determine the routing path to a given destination?
dig
netstat
ping
route
traceroute
The traceroute program can be used to determine the routing path to a given destination by sending packets with incrementing TTL values and recording the source of the ICMP time exceeded messages. This way, it can show the intermediate hops and the round-trip times for each packet. The other programs have different purposes: dig is used to query DNS servers, netstat is used to display network connections and statistics, ping is used to test the reachability of a host by sending ICMP echo requests and measuring the response time, and route is used to manipulate the routing table. References:
LPI 102-500 Exam Objectives, Topic 110: Network Fundamentals, Weight: 4, 110.3 Basic network troubleshooting
LPI 102-500 Study Guide, Chapter 10: Network Fundamentals, Section 10.3: Basic Network Troubleshooting, Page 125-126
Which port is the default server port for the HTTPS protocol? (Specify the port number using digits.)
443
The port number 443 is the default server port for the HTTPS protocol, which is a secure version of HTTP that uses SSL/TLS certificates to encrypt the data transmission between web servers and browsers. The port number 443 is recognized by the Internet Engineering Task Force (IETF) as the standard port for HTTPS connections1. The port number 443 is part of the topic 109.1: Fundamentals of internet protocols, which is one of the objectives of the LPI Linux Administrator - 102 exam23. References: 1: HTTPS Port: What It Is, How to Use It, and More (2023) - Hostinger 2: LPI Linux Administrator - 102 (LPIC-1) 3: Exam 102 Objectives
Copyright © 2021-2026 CertsTopics. All Rights Reserved

