You run the following PHP script:
$password = mysql_real_escape_string($_POST["password"]);?>
What is the use of the mysql_real_escape_string() function in the above script.
Each correct answer represents a complete solution. Choose all that apply
Which of the following Web authentication techniques uses a single sign-on scheme?
Which of the following tools is used to verify the network structure packets and confirm that the packets are constructed according to specification?
Which of the following can be used as a countermeasure against the SQL injection attack?
Each correct answer represents a complete solution. Choose two.
Ryan wants to create an ad hoc wireless network so that he can share some important files with another employee of his company. Which of the following wireless security protocols should he choose for setting up an ad hoc wireless network?
Each correct answer represents a part of the solution. Choose two.
You work as a Network Administrator in the Secure Inc. You often need to send PDF documents that contain secret information, such as, client password, their credit card details, email passwords, etc. through email to your customers. However, you are making PDFs password protected you are getting complaints from customers that their secret information is being misused. When you analyze this complaint you get that however you are applying the passwords on PDFs, they are not providing the maximum protection. What may be the cause of this security hole?
Which of the following attacks allows an attacker to sniff data frames on a local area network (LAN) or stop the traffic altogether?
John works as an Ethical Hacker for uCertify Inc. He wants to find out the ports that are open in uCertify's server using a port scanner. However, he does not want to establish a full TCP connection. Which of the following scanning techniques will he use to accomplish this task?
You work as a Penetration Tester for the Infosec Inc. Your company takes the projects of security auditing. Recently, your company has assigned you a project to test the security of the we-aresecure. com Website. The we-are-secure.com Web server is using Linux operating system. When you port scanned the we-are-secure.com Web server, you got that TCP port 23, 25, and 53 are open. When you tried to telnet to port 23, you got a blank screen in response. When you tried to type the dir, copy, date, del, etc. commands you got only blank spaces or underscores symbols on the screen. What may be the reason of such unwanted situation?
John works as a Professional Penetration Tester. He has been assigned a project to test the Website security of Inc. On the We-are-secure Website login page, he enters= 'or''=' as a username and successfully logs on to the user page of the Web site. Now, John asks the we-are-secure Inc. to improve the login page PHP script. Which of the following suggestions can John give to improve the security of the we-are-secure Website login page from the SQL injection attack?
You work as a Penetration Tester for the Infosec Inc. Your company takes the projects of security auditing. Recently, your company has assigned you a project to test the security of the we-aresecure. com Web site. For this, you want to perform the idle scan so that you can get the ports open in the we-are-secure.com server. You are using Hping tool to perform the idle scan by using a zombie computer. While scanning, you notice that every IPID is being incremented on every query, regardless whether the ports are open or close. Sometimes, IPID is being incremented by more than one value. What may be the reason?
Which of the following standards is used in wireless local area networks (WLANs)?
Which of the following tools connects to and executes files on remote systems?
You want to search the Apache Web server having version 2.0 using google hacking. Which of the following search queries will you use?
You are concerned about war driving bringing hackers attention to your wireless network. What is the most basic step you can take to mitigate this risk?
Which of the following best describes a server side exploit?
You are pen testing a Windows system remotely via a raw netcat shell. You want to quickly change directories to where the Windows operating system resides, what command could you use?
While scanning a remote system that is running a web server with a UDP scan and monitoring the scan with a sniffer, you notice that the target is responding with ICMP Port Unreachable only once a second What operating system is the target likely running?
Which of the following best describes a client side exploit?
What command will correctly reformat the Unix passwordcopy and shadowcopy Tiles for input to John The Ripper?
Raw netcat shells and telnet terminals share which characteristic?
In the screen shot below, which selections would you need click in order to intercept and alter all http traffic passing through OWASP ZAP?
Which of the following best explains why you would warn to clear browser slate (history. cache, and cookies) between examinations of web servers when you've been trapping and altering values with a non-transparent proxy?
A client has asked for a vulnerability scan on an internal network that does not have internet access. The rules of engagement prohibits any outside connection for the Nessus scanning machine. The customer has asked you to scan for a new critical vulnerability, which was released after the testing started, winch of the following methods of updating the Nessus plugins does not violate the rules of engagement?
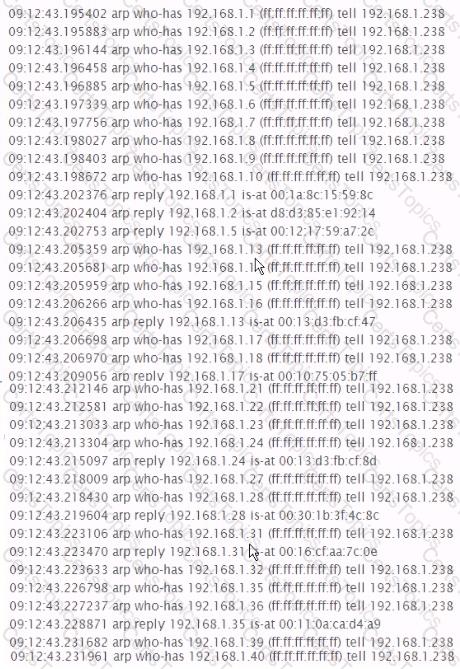
Identify the network activity shown below;
Which of the following is a method of gathering user names from a Linux system?
When sniffing wireless frames, the interface mode plays a key role in successfully collecting traffic. Which of the mode or modes are best used for sniffing wireless traffic?
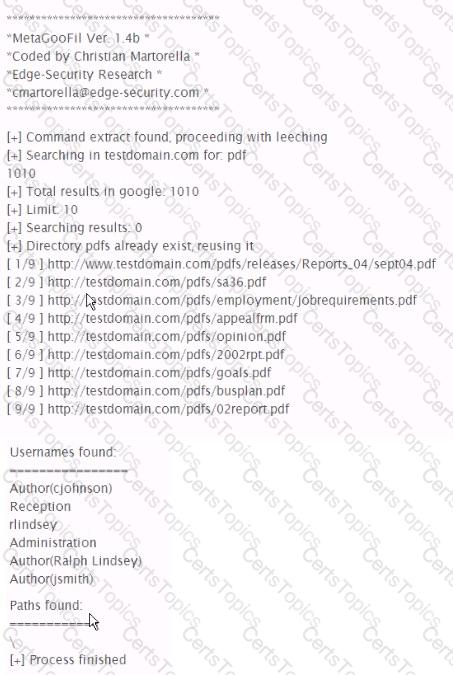
Analyze the command output below. What information can the tester infer directly from the Information shown?
Why is OSSTMM beneficial to the pen tester?
You are pen testing a network and have shell access to a machine via Netcat. You try to use ssh to access another machine from the first machine. What is the expected result?
Which of the following are considered Bluetooth security violations?
Each correct answer represents a complete solution. Choose two.
You are a Web Administrator of Millennium Inc. The company has hosted its Web site within its network. The management wants the company's vendors to be able to connect to the corporate site from their locations through the Internet. As a public network is involved in this process, you are concerned about the security of data transmitted between the vendors and the corporate site.
Which of the following can help you?
The employees of EWS Inc. require remote access to the company's Web servers. In order to provide solid wireless security, the company uses EAP-TLS as the authentication protocol. Which of the following statements are true about EAP-TLS?
Each correct answer represents a complete solution. Choose all that apply.
You want to retrieve password files (stored in the Web server's index directory) from various Web sites. Which of the following tools can you use to accomplish the task?
Which of the following commands can be used for port scanning?
You work as a Network Administrator for Tech Perfect Inc. The company requires a secure wireless network. To provide security, you are configuring ISA Server 2006 as a firewall. While configuring ISA Server 2006, which of the following is NOT necessary?
Which of the following techniques are NOT used to perform active OS fingerprinting?
Each correct answer represents a complete solution. Choose all that apply.
Adam, a malicious hacker, hides a hacking tool from a system administrator of his company by using Alternate Data Streams (ADS) feature. Which of the following statements is true in context with the above scenario?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of He wants to perform a stealth scan to discover open ports and applications running on the We-are-secure server. For this purpose, he wants to initiate scanning with the IP address of any third party. Which of the following scanning techniques will John use to accomplish his task?
Which of the following tools can be used to automate the MITM attack?
John works as a Professional Ethical Hacker for we-are-secure Inc. The company is using a Wireless network. John has been assigned the work to check the security of WLAN of we-aresecure.
For this, he tries to capture the traffic, however, he does not find a good traffic to analyze data. He has already discovered the network using the ettercap tool. Which of the following tools can he use to generate traffic so that he can crack the Wep keys and enter into the network?
Fill in the blank with the appropriate word.
____is a port scanner that can also be used for the OS detection.
John, a novice web user, makes a new E-mail account and keeps his password as "apple", his favorite fruit. John's password is vulnerable to which of the following password cracking attacks?
Each correct answer represents a complete solution. Choose all that apply.
Victor wants to use Wireless Zero Configuration (WZC) to establish a wireless network connection using his computer running on Windows XP operating system. Which of the following are the most likely threats to his computer?
Each correct answer represents a complete solution. Choose two.
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of In order to do so, he performs the following steps of the preattack phase successfully:
Information gathering
Determination of network range
Identification of active systems
Location of open ports and applications
Now, which of the following tasks should he perform next?
In which of the following attacks does an attacker use packet sniffing to read network traffic between two parties to steal the session cookie?
Which of the following statements about SSID is NOT true?
What does APNIC stand for?
In which of the following attacks is a malicious packet rejected by an IDS, but accepted by the host system?
Which of the following is the correct syntax to create a null session?
Which of the following tools is used for SNMP enumeration?
Which of the following penetration testing phases involves gathering data from whois, DNS, and network scanning, which helps in mapping a target network and provides valuable information regarding the operating system and applications running on the systems?
If a password is seven characters or less, the second half of the LM hash is always
___________________.
Which of the following is the correct sequence of packets to perform the 3-way handshake method?
Which of the following Web authentication techniques uses a single sign-on scheme?
Which of the following syntaxes is the correct syntax for the master.dbo.sp_makewebtask procedure?
Which of the following is the most common method for an attacker to spoof email?