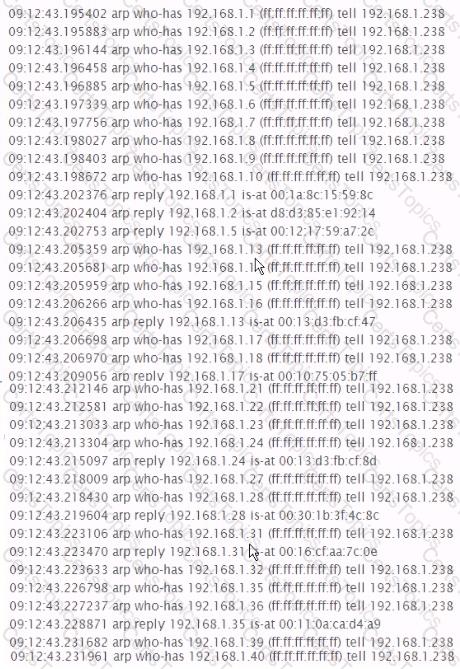
Identify the network activity shown below;
Which of the following is a method of gathering user names from a Linux system?
When sniffing wireless frames, the interface mode plays a key role in successfully collecting traffic. Which of the mode or modes are best used for sniffing wireless traffic?
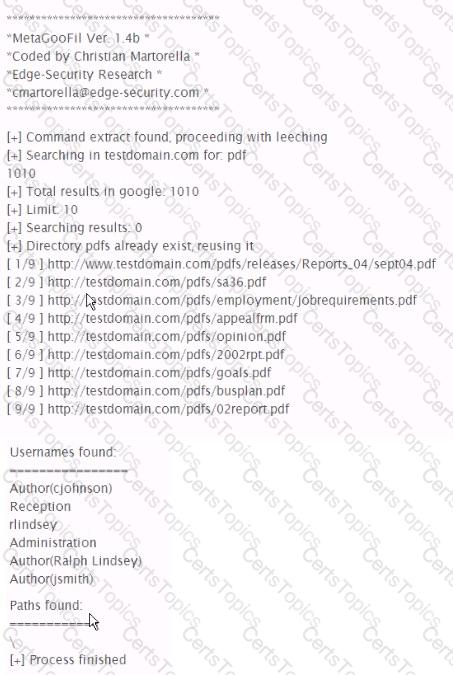
Analyze the command output below. What information can the tester infer directly from the Information shown?