A systems administrator needs to verify whether the built container has the app.go file in its root directory. Which of the following can the administrator use to verify the root directory has this file?
Which of the following commands is used to configure the default permissions for new files?
A Linux administrator reviews a set of log output files and needs to identify files that contain any occurrence of the word denied. All log files containing entries in uppercase or lowercase letters should be included in the list. Which of the following commands should the administrator use to accomplish this task?
Which of the following can be used as a secure way to access a remote termi-nal?
Which of the following technologies provides load balancing, encryption, and observability in containerized environments?
A user reported issues when trying to log in to a Linux server. The following outputs were received:
Given the outputs above. which of the following is the reason the user is una-ble to log in to the server?
While inspecting a recently compromised Linux system, the administrator identified a number of processes that should not have been running:
Which of the following commands should the administrator use to terminate all of the identified processes?
A junior administrator updated the PostgreSQL service unit file per the data-base administrator's recommendation. The service has been restarted, but changes have not been applied. Which of the following should the administrator run for the changes to take effect?
Which of the following directories is the mount point in a UEFI system?
A Linux administrator has set up a new DNS forwarder and is configuring all internal servers to use the new forwarder to look up external DNS requests. The administrator needs to modify the firewall on the server for the DNS forwarder to allow the internal servers to communicate to it and make the changes persistent between server reboots. Which of the following commands should be run on the DNS forwarder server to accomplish this task?
A systems administrator is installing various software packages using a pack-age manager. Which of the following commands would the administrator use on the Linux server to install the package?
A Linux system is failing to boot. The following error is displayed in the serial console:
[[1;33mDEPEND[Om] Dependency failed for /data.
[[1;33mDEPEND[Om] Dependency failed for Local File Systems
...
Welcome to emergency mode! After logging in, type "journalctl -xb" to viewsystem logs, "systemct1 reboot" to reboot, "systemct1 default" to try again to boot into default mode.
Give root password for maintenance
(or type Control-D to continue}
Which of the following files will need to be modified for this server to be able to boot again?
A systems administrator detected corruption in the /data filesystem. Given the following output:
Which of the following commands can the administrator use to best address this issue?
An administrator recently updated the BIND software package and would like to review the default configuration that shipped with this version. Which of the following files should the administrator review?
A Linux administrator found many containers in an exited state. Which of the following commands will allow the administrator to clean up the containers in an exited state?
Which of the following data structures is written in JSON?
A)
B)
C)
D)
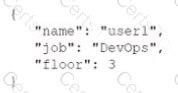
A systems administrator is encountering performance issues. The administrator runs 3 commands with the following output
The Linux server has the following system properties
CPU: 4 vCPU
Memory: 50GB
Which of the following accurately describes this situation?
A DevOps engineer wants to allow the same Kubernetes container configurations to be deployed in development, testing, and production environments. A key requirement is that the containers should be configured so that developers do not have to statically configure custom, environment-specific locations. Which of the following should the engineer use to meet this requirement?
A systems administrator is tasked with setting up key-based SSH authentication. In which of the following locations should the administrator place the public keys for the server?
Which of the following actions are considered good security practices when hardening a Linux server? (Select two).
A cloud engineer needs to launch a container named web-01 in background mode. Which of the following commands will accomplish this task''
A Linux administrator has been tasked with installing the most recent versions of packages on a RPM-based OS. Which of the following commands will accomplish this task?
A Linux administrator is installing a web server and needs to check whether web traffic has already been allowed through the firewall. Which of the following commands should the administrator use to accomplish this task?
A Linux administrator was notified that a virtual server has an I/O bottleneck. The Linux administrator analyzes the following output:
Given there is a single CPU in the sever, which of the following is causing the slowness?
A Linux administrator has physically added a new RAID adapter to a system. Which of the following commands should the Linux administrator run to confirm that the device has been recognized? (Select TWO).
A Linux administrator is providing a new Nginx image from the registry to local cache. Which of the following commands would allow this to happen?
A Linux engineer needs to download a ZIP file and wants to set the nice of value to -10 for this new process. Which of the following commands will help to accomplish the task?
A developer needs to launch an Nginx image container, name it Web001, and ex-pose port 8080 externally while mapping to port 80 inside the container. Which of the following commands will accomplish this task?
A systems administrator is troubleshooting a connectivity issue pertaining to access to a system named db.example.com. The system IP address should be 192.168.20.88. The administrator issues the dig command and receives the following output:
The administrator runs grep db.example.com /etc/hosts and receives the following output:
Given this scenario, which of the following should the administrator do to address this issue?
A systems administrator has been unable to terminate a process. Which of the following should the administrator use to forcibly stop the process?
Employees in the finance department are having trouble accessing the file /opt/work/file. All IT employees can read and write the file. Systems administrator reviews the following output:
Which of the following commands would permanently fix the access issue while limiting access to IT and finance department employees?
A database administrator requested the installation of a custom database on one of the servers. Which of the following should the Linux administrator configure so the requested packages can be installed?
A Linux administrator is reviewing changes to a configuration file that includes the following section:
The Linux administrator is trying to select the appropriate syntax formatter to correct any issues with the configuration file. Which of the following should the syntax formatter support to meet this goal?
Due to performance issues on a server, a Linux administrator needs to termi-nate an unresponsive process. Which of the following commands should the
administrator use to terminate the process immediately without waiting for a graceful shutdown?
A Linux administrator copied a Git repository locally, created a feature branch, and committed some changes to the feature branch. Which of the following Git actions should the Linux administrator use to publish the changes to the main branch of the remote repository?
A Linux administrator rebooted a server. Users then reported some of their files were missing. After doing some troubleshooting, the administrator found one of the filesystems was missing. The filesystem was not listed in /etc/f stab and might have been mounted manually by someone prior to reboot. Which of the following would prevent this issue from reoccurring in the future?
Which of the following enables administrators to configure and enforce MFA on a Linux system?
The security team has identified a web service that is running with elevated privileges A Linux administrator is working to change the systemd service file to meet security compliance standards. Given the following output:
Which of the following remediation steps will prevent the web service from running as a privileged user?
A systems administrator pressed Ctrl+Z after starting a program using the command line, and the shell prompt was presented. In order to go back to the program, which of the following commands can the administrator use?
A systems administrator is enabling LUKS on a USB storage device with an ext4 filesystem format. The administrator runs dmesg and notices the following output:
Given this scenario, which of the following should the administrator perform to meet these requirements? (Select three).
A developer reported an incident involving the application configuration file /etc/httpd/conf/httpd.conf that is missing from the server. Which of the following identifies the RPM package that installed the configuration file?
A junior developer is unable to access an application server and receives the following output:
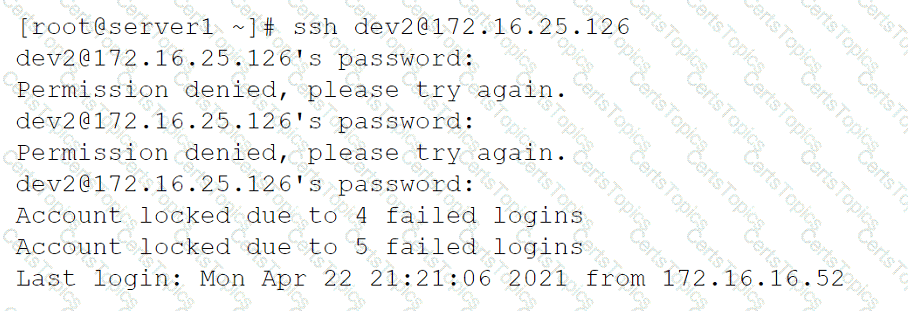
The systems administrator investigates the issue and receives the following output:
Which of the following commands will help unlock the account?
A systems administrator wants to list all local accounts in which the UID is greater than 500. Which of the following commands will give the correct
output?
A Linux administrator needs to connect securely to a remote server in order to install application software. Which of the following commands would allow this connection?
A Linux systems administrator is troubleshooting an I/O latency on a single CPU server. The administrator runs a top command and receives the following output:
%Cpu(s): 0.2 us, 33.1 sy, 0.0 ni, 0.0 id, 52.4 wa, 0.0 hi, 0.2 si, 0.0 st
Which of the following is correct based on the output received from the exe-cuted command?
What is the main objective when using Application Control?
A senior Linux administrator has created several scripts that will be used to install common system applications. These scripts are published to a reposito-ry to share with the systems team. A junior Linux administrator needs to re-trieve the scripts and make them available on a local workstation. Which of the following Git commands should the junior Linux administrator use to accom-plish this task?
A Linux administrator is adding a new configuration file to a Git repository. Which of the following describes the correct order of Git commands to accomplish the task successfully?
A Linux engineer receives reports that files created within a certain group are being modified by users who are not group members. The engineer wants to reconfigure the server so that only file owners and group members can modify new files by default. Which of the following commands would accomplish this task?
A technician wants to temporarily use a Linux virtual machine as a router for the network segment 10.10.204.0/24. Which of the following commands should the technician issue? (Select three).
A Linux administrator encounters the following error in the Apache log files:
css
SQLSTATE[HY000] [2002] Permission denied
Which of the following commands should the administrator run to safely fix this issue?
The applications team is reporting issues when trying to access the web service hosted in a Linux system. The Linux systems administrator is reviewing the following outputs:
Output 1:
* httpd.service = The Apache HTTPD Server
Loaded: loaded (/usr/lib/systemd/system/httpd.service; disabled; vendor preset: disabled)
Active: inactive (dead)
Docs: man:httpd(8) man:apachectl(8)
Output 2:
16:51:16 up 28 min, 1 user, load average: 0.00, 0.00, 0.07
Which of the following statements best describe the root cause? (Select two).
An engineer needs to insert a character at the end of the current line in the vi text editor. Which of the following will allow the engineer to complete this task?
A systems administrator needs to integrate a new storage array into the company's existing storage pool. The administrator wants to ensure that the server is able to detect the new storage array. Which of the following commands should the administrator use to ensure that the new storage array is presented to the systems?
A Linux administrator needs to create a symlink for /usr/local/bin/app-a, which was installed in /usr/local/share/app-a. Which of the following commands should the administrator use?
Users are reporting that a Linux server is responding slowly. A systems administrator troubleshooting the server issue sees the following:
# iostat -m 2
Linux 3.10.0-1160.66.1.el7.x86_64 (myhost) 10/19/2022 x86_64 (4 CPU)
avg-cpu: %user %nice %system %iowait %steal %idle
24.30 0.01 0.29 50.38 4.00 19.01
Device: tps MB_read/s MB_wrtn/s MB_read MB_wrtn
sdd 15.65 0.48 0.83 4936250 8513501
# df -h
Filesystem Size Used Avail Use% Mounted on
devtmpfs 16G 0 16G 0% /dev
tmpfs 16G 64K 16G 1% /dev/shm
/dev/mapper/root 35G 8.8G 26G 26% /
/dev/sda2 497M 144M 354M 29% /boot
/dev/mapper/tmp 10G 38M 10G 1% /tmp
/dev/mapper/var 15G 13G 2.2G 86% /var
/dev/mapper/varlib 650G 397G 254G 62% /var/lib
/dev/mapper/varlog 15G 9.5G 5.5G 64% /var/log
/dev/mapper/varaudit 15G 72M 15G 1% /var/log/audit
Which of the following is most likely the issue?
A Linux administrator needs to run a web application on a server that requires the use of a desktop web browser to enter the final configuration information. The administrator determines the server is running in multi-user mode. The administrator verifies that a web browser is installed on the server and that it has a display manager installed. Which of the following commands will best allow the administrator to temporarily use the web browser on the server?
After trying to install an RPM package unsuccessfully, a systems administrator verifies the integrity of the package's database. The administrator discovers that the database is corrupted and needs to be recreated. Which of the following commands will help accomplish this task?
Which of the following commands is used to tune kernel parameters?
A Linux administrator is troubleshooting an issue in which users are not able to access from a specific workstation. The
administrator runs a few commands and receives the following output:
Which of the following tasks should the administrator perform to resolve this issue?
A technician just fixed a few issues in some code and is ready to deploy the code into production. Which of the following steps should the technician take next?
A systems administrator needs to check the size of the filesystem on the current application servers and ensure that the following filesystems are mounted:
/var
/var/log/audit
/tmp
/home/application
Which of the following commands should the administrator use for these tasks?
Users connecting to a MySQL database on a Linux system report frequent errors. An administrator reviews the following partial output of the /proc/meminfo and free commands:
total used free
Mem: 1011966 151930 860036
Swap: 1191972 1181716 10256
MemTotal: 1011966 kB
MemFree:
SwapTotal: 1191972 kB
SwapFree: 10256 kB
Which of the following should the administrator do to ensure that the MySQL service will continue to run even if the system runs out of swap space? (Select two.)
A developer wants to ensure that all files and folders created inside a shared folder named /GroupOODEV inherit the group name of the parent folder. Which of the following commands will help achieve this goal?
A systems administrator wants to ensure all the latest patches and updates are automatically synced to the local repository every two hours on Sundays through Tuesdays in the month of May. Which of the following cron entries can the administrator use to achieve this goal? (Select two.)
A systems administrator is reconfiguring existing user accounts in a Linux system. Which of the following commands should the administrator use to include "myuser" in the finance group?
A Linux administrator is creating a new sudo profile for the accounting user. Which of the following should be added by the administrator to the sudo
configuration file so that the accounting user can run / opt/ acc/ report as root?
A network administrator issues the dig command and receives an NXDOMAIN response. Which of the following files should the administrator check first?
A systems administrator receives the following message after running an ip link command to verify the status of a network interface named enp0s3:
state DOWN
Which of the following commands should the administrator use to resolve this issue?
A Linux administrator is testing a web application on a laboratory service and needs to temporarily allow DNS and HTTP/HTTPS traffic from the internal network. Which of the following commands will accomplish this task?
An administrator is running a web server in a container named web, but none of the error output is not showing. Which of the following should the administrator use to generate the errors on the container?
Which of the following is the main purpose of SSO?
An administrator is unable to sync servers to the new NTP server IP address given by the service provider despite several attempts. Looking at the below output

Which of the following commands will help resolve the issue?
A new user is experiencing issues creating files in the folder /home/testuser/testdir/. The directory needs to be accessible for reading by other users in the system. The administrator gathers the following information:
Copy
drwxr-xr-x. 2 root testuser 6 Oct 19 11:22 testdir
Which of the following commands should the administrator use to solve the issue? (Select TWO).
NO: 41:
A systems administrator needs to install the file installer_0.17-41.2_amd64.deb. Which of the following commands should the administrator use?
A systems administrator needs to disable root login for SSH. Which of the following commands should the administrator use?
NO: 60:
A Linux administrator is creating a directory called CompTIA_doc, and it needs to switch to another location to perform some system-related tasks. Which of the following commands should the administrator use for this task?
A Linux administrator would like to measure possible packet loss between a workstation and a remote web application that is running on port 443. Which of the following would be the best command for the administrator to use to display this information?
A systems administrator needs to install the file installer_0.17-41.2_amd64.deb. Which of the following commands should the administrator use?
A systems administrator is working on an SFTP server configuration. Which of the following commands will best enable the connectivity to that service from the 10.10.0.0/24 network?
A Linux administrator needs to restart a server and wants to see if any users are currently connected to it. Which of the following commands should the administrator run to find this information?
A Linux administrator is troubleshooting an SSHD issue on a server. Users are receiving error messages stating the connection is refused. Which of the following commands should be used to verify whether the service is listening?
A Linux administrator is changing the default system umask. The newly created files should have the -rw-r----- permission, and the newly created directories should have the drwxr----- permission. Which of the following commands should the administrator use?
A Linux administrator is working with a CPU-intensive program called data-analysis1. The administrator needs to prevent the program from monopolizing CPU resources and ensure that other critical processes are not impacted when the program starts. Which of the following commands would start the program with a reduced level of impact to the system?
Which of the following directories contains binaries that only a root user should run?
A Linux administrator provisioned a new web server with custom administrative permissions for certain users. The administrator receives a report that user1 is unable to restart the Apache web service on this server. The administrator reviews the following output:
[ root@server ] # id user1
UID=1011 (user1) gid=1011 (USER1) groups=1011 (user1), 101 (www-data), 1120 (webadmin)
[ root@server ] # cat /etc/sudoers.d/custom.conf
user1 ALL=/usr/sbin/systemctl start httpd, /usr/sbin/systemctl stop httpd
webadmin ALL=NOPASSWD: /etc/init.d.httpd restart, /sbin/service httpd restart, /usr/sbin/apache2ctl restart
#%wheel ALL=(ALL) NOPASSWD: ALL
Which of the following would most likely resolve the issue while maintaining a least privilege security model?
An administrator needs to install an Apache web server on an Ubuntu server. Which of the following commands should the administrator use?
An administrator started a long-running process in the foreground that needs to continue without interruption. Which of the following keystrokes should the administrator use to continue running the process in the background?
A Linux administrator is creating a directory called CompTIA_doc and needs to switch to another location to perform some system-related tasks. Which of the following commands should the administrator use for this task?
A Linux administrator receives a ticket stating that end users are unable to access the company’s internal cloud server. The administrator executes the following command:
bash
ping usl.com
Result:
ping: cannot resolve usl.com: Unknown Host
Which of the following files needs to be modified to allow end users to access usl.com?
A Linux administrator is troubleshooting connectivity issues and receives the following outputs:
python
Copy
$ ping comptia.org
ping: comptia.org: Temporary failure in name resolution
$ ping 104.18.17.29
64 bytes from 104.18.17.29: icmp_seq=1 ttl=63 time=31.4 ms
...
Which of the following describes the issue?
The group owner of the / home/ test directory would like to preserve all group permissions on files created in the directory. Which of the following
commands should the group owner execute?
Which of the following is a way to enable a production web server's communications with strong encryption and identity verification?
A security team discovers that a web server has been running with elevated privileges and identifies it as a security violation. Which of the following items needs to be added to the webserver.service file to remediate the issue?
NO: 22:
An organization’s business office needs to collaborate on quarterly reports and asks the systems administrator to create a finance group. The administrator creates the following directory:
drwxrwxr-x Business Business 4096 Oct 15 16:40 Q1
Which of the following commands will allow all members of the finance group to have group ownership of all files created in the Q1 directory while ensuring that members of the business group preserve access? (Select two).
A Linux administrator is creating a user that can run the FTP service but cannot log in to the system. The administrator sets /bin/false as a login shell for the user. When the user tries to run the FTP service, it is rejected with an "invalid shell: /bin/false" message. Which of the following is the best way to resolve the issue?
An administrator thinks that the user Joe may be running an unauthorized process on a Linux server. Which of the following commands should the administrator run to confirm this idea?
A Linux administrator generated a list of users who have root-level command-line access to the Linux server to meet an audit requirement. The administrator analyzes the following /etc/passwd and /etc/sudoers files:
$ cat /etc/passwd
root:x: 0:0: :/home/root: /bin/bash
lee: x: 500: 500: :/home/lee:/bin/tcsh
mallory:x: 501:501: :/root:/bin/bash
eve:x: 502: 502: /home/eve:/bin/nologin
carl:x:0:503: :/home/carl:/bin/sh
bob:x: 504: 504: : /home/bob:/bin/ksh
alice:x: 505:505: :/home/alice:/bin/rsh
$ cat /etc/sudoers
Cmnd_Alias SHELLS = /bin/tcsh, /bin/sh, /bin/bash
Cmnd_Alias SYSADMIN = /usr/sbin/tcpdump
ALL = (ALL) ALL
ALL = NOPASSWD: SYSADMIN
Which of the following users, in addition to the root user, should be listed in the audit report as having root-level command-line access? (Select two).
A systems administrator is tasked with creating a cloud-based server with a public IP address.
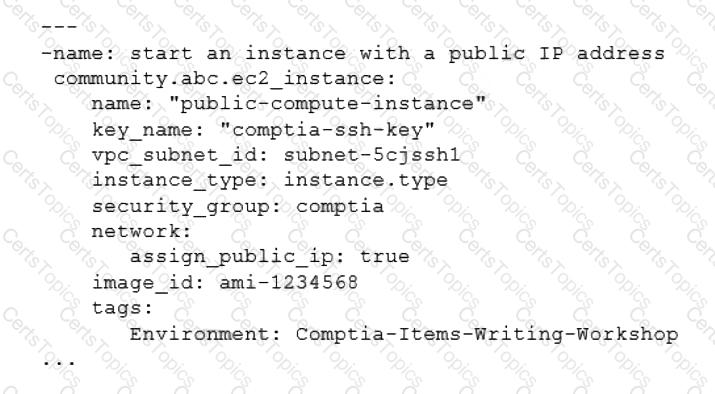
Which of the following technologies did the systems administrator use to complete this task?
A junior Linux administrator is tasked with installing an application. The installation guide states the application should only be installed in a run level 5 environment.
Which of the following commands would ensure the server is set to runlevel 5?
A junior administrator is setting up a new Linux server that is intended to be used as a router at a remote site. Which of the following parameters will accomplish this goal?
A Linux administrator was asked to run a container with the httpd server inside. This container should be exposed at port 443 of a Linux host machine while it internally listens on port 8443. Which of the following commands will accomplish this task?
A Linux administrator created the directory /project/access2all. By creating this directory, the administrator is trying to avoid the deletion or modification of files from non-owners. Which of the following will accomplish this goal?
A cloud engineer is installing packages during VM provisioning. Which of the following should the engineer use to accomplish this task?
A cloud engineer needs to change the secure remote login port from 22 to 49000. Which of the following files should the engineer modify to change the port number to the desired value?
A new file was added to a main Git repository. An administrator wants to synchronize a local copy with the contents of the main repository. Which of the following commands should the administrator use for this task?
After installing some RPM packages, a systems administrator discovers the last package that was installed was not needed. Which of the following commands can be used to remove the package?
A systems administrator is tasked with installing GRUB on the legacy MBR of the SATA hard drive. Which of the following commands will help the administrator accomplish this task?
A Linux administrator needs to redirect all HTTP traffic temporarily to the new proxy server 192.0.2.25 on port 3128. Which of the following commands will accomplish this task?
A Linux administrator booted up the server and was presented with a non-GUI terminal. The administrator ran the command systemct1 isolate graphical.target and rebooted the system by running systemct1 reboot, which fixed the issue. However, the next day the administrator was presented again with a non-GUI terminal. Which of the following is the issue?
A cloud engineer is asked to copy the file deployment.yaml from a container to the host where the container is running. Which of the following commands can accomplish this task?
An administrator needs to make some changes in the IaC declaration templates. Which of the following commands would maintain version control?
A systems administrator configured firewall rules using firewalld. However, after the system is rebooted, the firewall rules are not present:
The systems administrator makes additional checks:
Which of the following is the reason the firewall rules are not active?
A Linux administrator needs to resolve a service that has failed to start. The administrator runs the following command:
The following output is returned
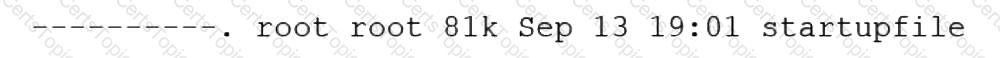
Which of the following is MOST likely the issue?
A Linux administrator needs to ensure that Java 7 and Java 8 are both locally available for developers to use when deploying containers. Currently only Java 8 is available. Which of the following commands should the administrator run to ensure both versions are available?
A junior systems administrator has just generated public and private authentication keys for passwordless login. Which of the following files will be moved to the remote servers?
A Linux administrator is tasked with adding users to the system. However, the administrator wants to ensure the users’ access will be disabled once the project is over. The expiration date should be 2021-09-30. Which of the following commands will accomplish this task?
A newly created container has been unable to start properly, and a Linux administrator is analyzing the cause of the failure. Which of the following will allow the administrator to determine the FIRST command that is executed inside the container right after it starts?
An administrator deployed a Linux server that is running a web application on port 6379/tcp.
SELinux is in enforcing mode based on organization policies.
The port is open on the firewall.
Users who are trying to connect to a local instance of the web application receive Error 13, Permission denied.
The administrator ran some commands that resulted in the following output:

Which of the following commands should be used to resolve the issue?
A Linux administrator is trying to remove the ACL from the file /home/user/data. txt but receives the following error message:
Given the following analysis:
Which of the following is causing the error message?
A cloud engineer needs to remove all dangling images and delete all the images that do not have an associated container. Which of the following commands will help to accomplish this task?
A Linux administrator needs to remove software from the server. Which of the following RPM options should be used?
Junior system administrator had trouble installing and running an Apache web server on a Linux server. You have been tasked with installing the Apache web server on the Linux server and resolving the issue that prevented the junior administrator from running Apache.
INSTRUCTIONS
Install Apache and start the service. Verify that the Apache service is running with the defaults.
Typing “help” in the terminal will show a list of relevant event commands.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A developer is trying to install an application remotely that requires a graphical interface for installation. The developer requested assistance to set up the necessary environment variables along with X11 forwarding in SSH. Which of the following environment variables must be set in remote shell in order to launch the graphical interface?
When trying to log in remotely to a server, a user receives the following message:

The server administrator is investigating the issue on the server and receives the following outputs:

Which of the following is causing the issue?
A DevOps engineer needs to download a Git repository from Which of the following commands will achieve this goal?
Developers have requested implementation of a persistent, static route on the application server. Packets sent over the interface eth0 to 10.0.213.5/32 should be routed via 10.0.5.1. Which of the following commands should the administrator run to achieve this goal?
A Linux systems administrator needs to persistently enable IPv4 forwarding in one of the Linux systems. Which of the following commands can be used together to accomplish this task? (Choose two.)
A systems administrator requires that all files that are created by the user named web have read-only permissions by the owner. Which of the following commands will satisfy this requirement?
A Linux system is failing to boot with the following error:
Which of the following actions will resolve this issue? (Choose two.)
A Linux administrator needs to correct the permissions of a log file on the server. Which of the following commands should be used to set filename.log permissions to -rwxr—r--. ?
Which of the following files holds the system configuration for journal when running systemd?
A systems administrator has been tasked with disabling the nginx service from the environment to prevent it from being automatically and manually started. Which of the following commands will accomplish this task?
A systems administrator is troubleshooting connectivity issues and trying to find out why a Linux server is not able to reach other servers on the same subnet it is connected to. When listing link parameters, the following is presented:

Based on the output above, which of following is the MOST probable cause of the issue?
A Linux administrator is troubleshooting a memory-related issue. Based on the output of the commands:
Which of the following commands would address the issue?
Based on an organization’s new cybersecurity policies, an administrator has been instructed to ensure that, by default, all new users and groups that are created fall within the specified values below.
To which of the following configuration files will the required changes need to be made?
A Linux administrator wants to find out whether files from the wget package have been altered since they were installed. Which of the following commands will provide the correct information?
A Linux administrator needs to create a new cloud.cpio archive containing all the files from the current directory. Which of the following commands can help to accomplish this task?
Users report that connections to a MariaDB service are being closed unexpectedly. A systems administrator troubleshoots the issue and finds the following message in /var/log/messages:
Which of the following is causing the connection issue?
A Linux engineer is setting the sticky bit on a directory called devops with 755 file permission. Which of the following commands will accomplish this task?
A systems administrator made some changes in the ~/.bashrc file and added an alias command. When the administrator tried to use the alias command, it did not work. Which of the following should be executed FIRST?
A DevOps engineer needs to allow incoming traffic to ports in the range of 4000 to 5000 on a Linux server. Which of the following commands will enforce this rule?
A systems administrator needs to check if the service systemd-resolved.service is running without any errors. Which of the following commands will show this information?
A Linux administrator is troubleshooting an issue in which an application service failed to start on a Linux server. The administrator runs a few commands and gets the following outputs:
Based on the above outputs, which of the following is the MOST likely action the administrator should take to resolve this issue?
A Linux system is failing to start due to issues with several critical system processes. Which of the following options can be used to boot the system into the single user mode? (Choose two.)
A Linux administrator was tasked with deleting all files and directories with names that are contained in the sobelete.txt file. Which of the following commands will accomplish this task?