A systems administrator detected corruption in the /data filesystem. Given the following output:
Which of the following commands can the administrator use to best address this issue?
An administrator recently updated the BIND software package and would like to review the default configuration that shipped with this version. Which of the following files should the administrator review?
A Linux administrator found many containers in an exited state. Which of the following commands will allow the administrator to clean up the containers in an exited state?
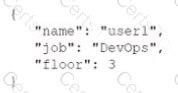
Which of the following data structures is written in JSON?
A)
B)
C)
D)