Refer to the exhibit.
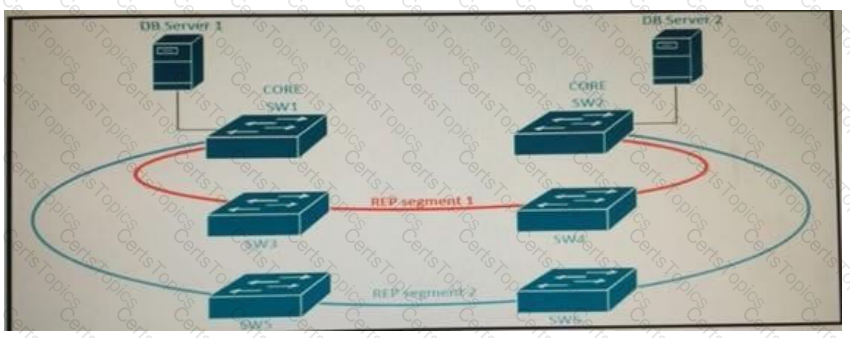
A new high availability DB sever cluster is installed in the network.
These two servers require high bandwidth and low latency Layer 2 connectivity for database replication.
Which solution supports these requirements?
Which optimal use of interface dampening on a fast convergence network design is true?
In a redundant hub and spoke "wheel" design, all spokes are connected to the hub, and spokes are connected to other spokes as well. During failure on one spoke link, the traffic from that site can be sent to a neighboring site for it to be forwarded to the hub site. But during peak hours, a link is overloaded and traffic is re-routed to a neighbor, which subsequently becomes overloaded. This overload results in network traffic oscillation as the load varies at each spoke site. This design provides more redundancy but not more resiliency because the routing protocol must process many alternate paths to determine the lowest cost path. Which two design
changes help to improve resilience in this case? (Choose two.)
Hybrid cloud computing allows organizations to like advantage of public and private cloud models Which best practice should organizations follow to ensure data security in the private cloud?
QUESTION 69 Refer to the exhibit. AJI links are P2P Layer 3. A high availability application is synchronizing data between host A and host B. To increase chance of delivery the same data is sent twice from host A on two different NICs toward the two NICs on host B.
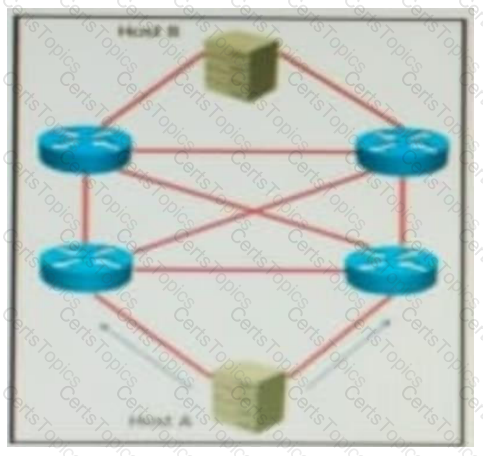
Which solution must be deployed in the network to ensure that any failure in the network does not trigger data loss on host B?
The Company XYZ network requires OSPF dead neighbor detection in a subsecond manner However the company network does not support BFD Which other feature can be used to fulfill the design requirement?
Which two design solutions ensure sub 50 msec of the convergence time after a link failure in the network?
(Choose two)
Company XYZ Is running a redundant private WAN network using OSPF as the underlay protocol The current design accommodates for redundancy In the network, but it Is taking over 30 seconds for the network to reconverge upon failure Which technique can be Implemented In the design to detect such a failure in a subsecond?
Which three items do you recommend for control plane hardening of an infrastructure device? (Choose three.)
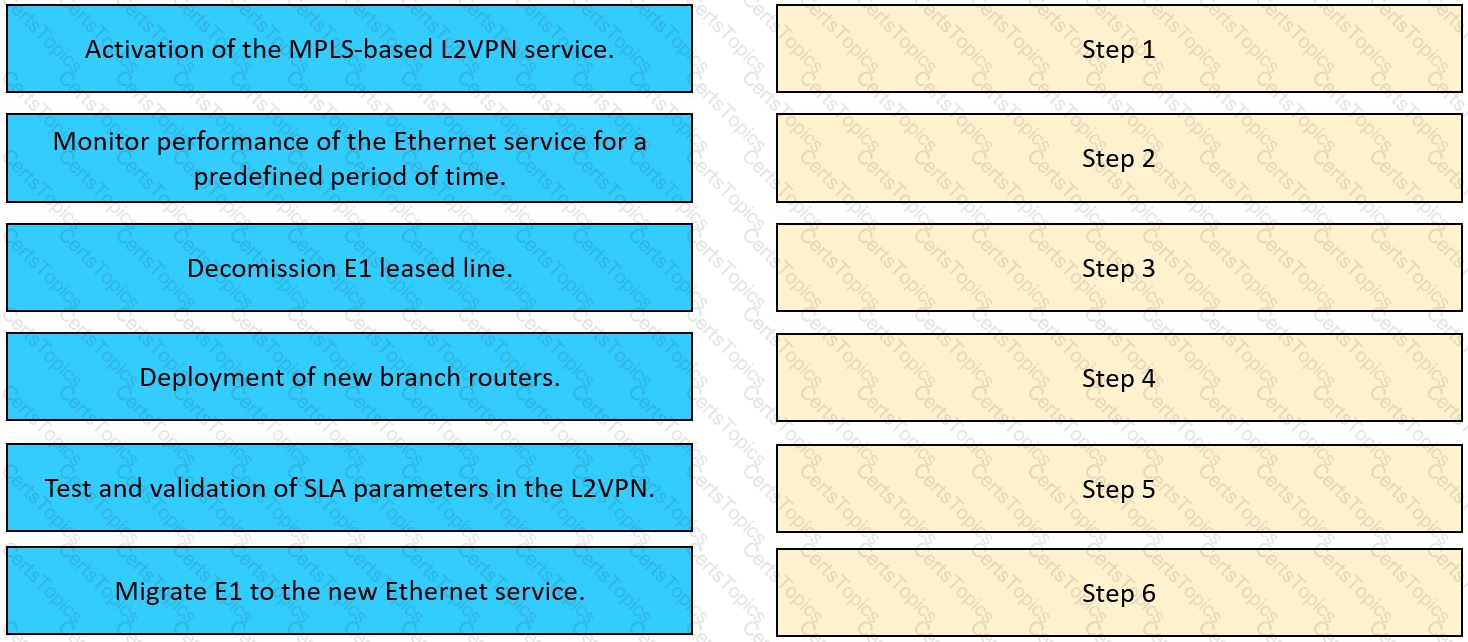
The network team in XYZ Corp wants to modernize their infrastructure and is evaluating an implementation and migration plan to allow integration MPLS-based, Layer 2 Ethernet services managed by a service provider to connect branches and remote offices. To decrease OpEx and improve
response times when network components fail, XYZ Corp decided to acquire and deploy new routers. The network currently is operated over E1 leased lines (2 Mbps) with a managed CE service provided by the telco.
Drag and drop the implementation steps from the left onto the corresponding targets on the right in the correct order.
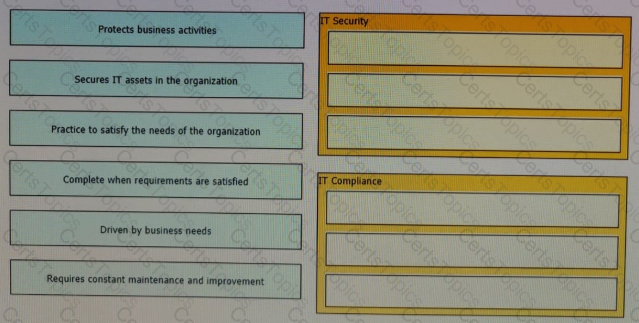
The line between security and compliance is easily blurred and is, to a large extent, a moving target Drag and drop each of the requirements on the left to the appropriate section on the right
Company XYZ wants to use the FCAPS ISO standard for network management design. The focus of the design should be to minimize network outages by employing a set of procedures and activities to detect and isolate network issues and the appropriate corrective actions to overcome current issues and prevent them from occurring again. Which layer accomplishes this design requirement?
Which option is a fate-sharing characteristic in regards to network design?
A customer migrates from a traditional Layer 2 data center network into a new SDN-based spine-and-leaf VXLAN EVPN data center within the same location The networks are joined to enable host migration at Layer 2 What is the final migration step after hosts have physically migrated to have traffic flowing through the new network without changing any host configuration?
You have been tasked with designing a data center interconnect to provide business continuity You want to encrypt the traffic over the DCI using IEEE 802 1AE MACsec to prevent the deployment of any firewall or IPS. Which two interconnect technologies support MACsec? (Choose two.)
Various teams in different organizations within an enterprise are preparing low-level design documents to capture network parameters using a Waterfall project model:
• hardware sizing and power consumption
• Layer 2 and layer 3 services parameters
• configuration of all control plane protocols
Input from relevant stakeholders was captured at the start of the project, and the project scope has been defined based on the parameters above. What impact will it have on documentation and project deliverables if the stakeholders ask to have changes carried out in the network before the information has been captured?
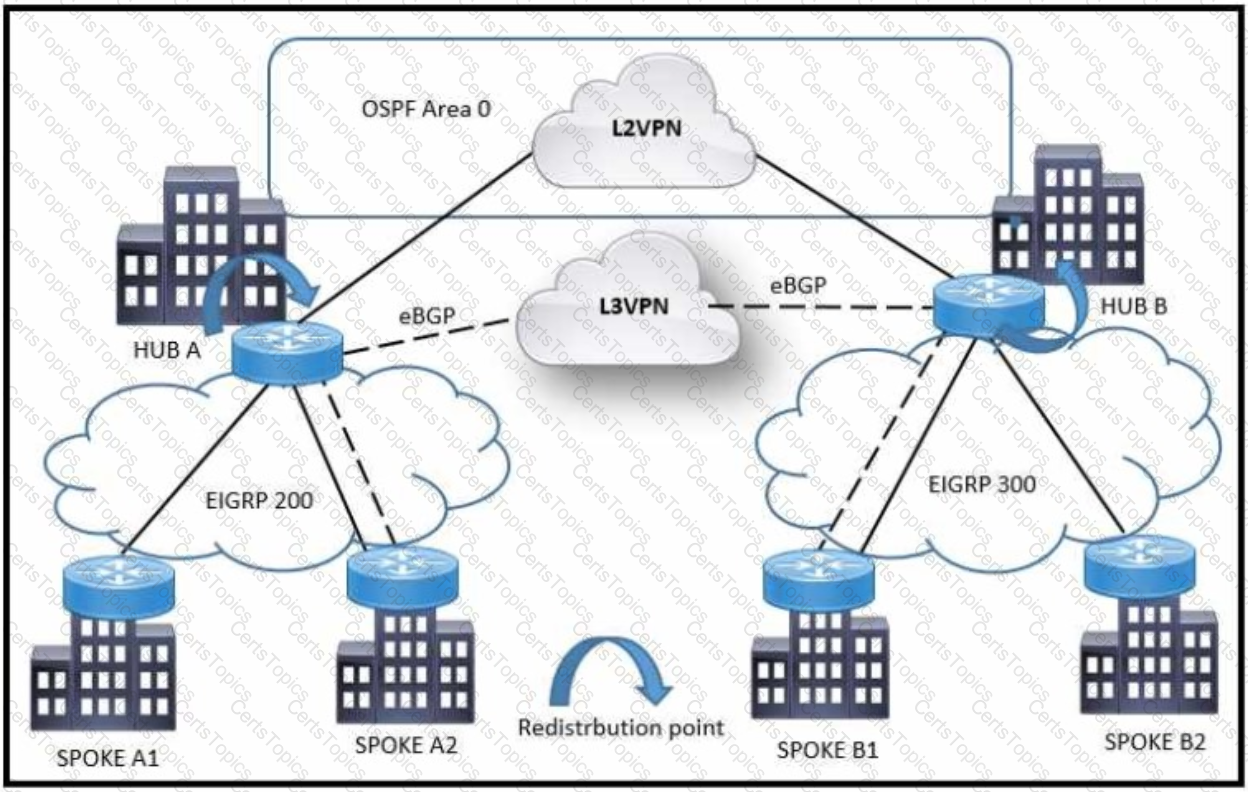
Refer to the exhibit A customer network design team is planning a migration from a legacy TDM-based L2VPN to an MPLS-based L3VPN Migration is planned in a phased approach:
•OSPF backbone Link between HUB A and HUB B sites to be migrated to eBGP
•Spoke A2 and Spoke B1 will be migrated to the L3VPN
Which solution design can be considered to avoid routing loops during backbone link migration?
Which two statements describe the hierarchical LAN design model? (Choose two)
The administrator of a small branch office wants to implement the Layer 2 network without running STP The office has some redundant paths Which mechanism can the administrator use to allow redundancy without creating Layer 2 loops?
A business customer deploys workloads in the public cloud. Now the customer network faces governance issues with the flow of IT traffic and must ensure the security of data and intellectual property. Which action helps to identify the issue for further resolution?
What is the most important operational driver when building a resilient and secure modular network design?
What are two descriptions of network optimization? (Choose two.)
A network architect in an enterprise is designing a network policy for certain database applications. The goal of the policy is to allow these applications to access the internet directly, whereas other user and network applications that communicate with systems or users outside their own network must be routed through the data center. The focus is on achieving higher availability and a better user experience for the database applications, but switching between different network paths based on performance characteristics must be supported.
Which solution meets these requirements?
Company XYZ wants to redesign the Layer 2 part of their network and wants to use all available uplinks for increased performance. They also want to have end host reachability supporting conversational learning. However, due to design constraints, they cannot implement port-channel on the uplinks. Which other technique can be used to make sure the uplinks are in active/active state?
How can EIGRP topologies be designed to converge as fast as possible in the event of a point-to-point link failure?
Refer to the exhibit.
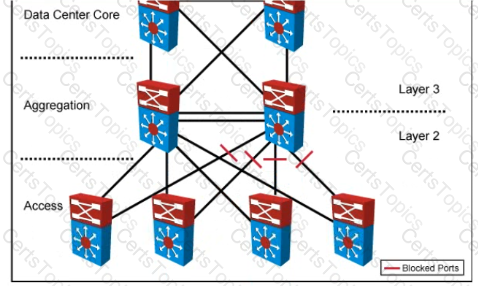
Your company designed a network to allow server VLANs to span all access switches in a data center In the design, Layer 3 VLAN interfaces and HSRP are configured on the aggregation switches Which two features improve STP stability within the network design? (Choose two.)
Which two points must network designers consider when designing a new network design or when evaluating an existing network design to help them understand the high-level design direction with regards to the security aspects? (Choose two)
Which two aspects are considered when designing a dual hub dual DMVPN cloud topology? (Choose two )
Which layer of the SDN architecture orchestrates how the applications are given the resources available in the network?
A large enterprise cloud design team is evaluating different cloud consumption models. What is an example of typical PaaS limitations or concerns that should be considered during service design?
A company plans to use BFD between its routers to detect a connectivity problem inside the switched network. An IPS is transparently installed between the switches. Which packets shold the IPS forward for BFD to work under all circumstances?
A software-defined networking (SDN) controller teams network topology information by using BGP link-state sessions with the route reflectors of an MPLS-enabled network. The controller then uses the topology information to apply on-demand traffic policies to the network through a protocol that is supported from all Layer 3 routers Each policy is represented as a RIB entry in the control plane of the router Which SDN model has been implemented?
What are two key design principles when using a hierarchical core-distribution-access network model? (Choose two )
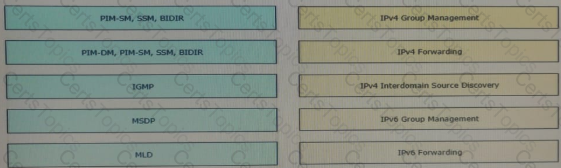
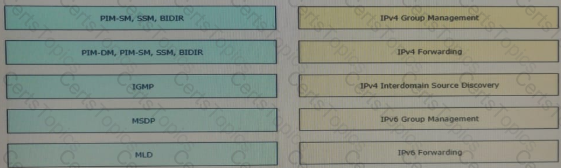
Drag and drop the multicast protocols from the left onto the current design situation on the right.
A business wants to centralize services via VDI technology and to replace remote WAN desktop PCs with thin client-type machines to reduce operating costs Which consideration supports the new business requirement?
What are two advantages of controller-based networks versus traditional networks? (Choose two.)
What is the most important operational driver in building a resilient and secure modular network design?
As part of a new network design documentation, you are required to explain the reason for choosing cisco FabricPath for Layer 2 loop avoidance.
Which two elements help Cisco FabricPath mitigate Layer 2 loops if they happen in the Layer 2 MP network?
(Choose two)
Which two statements describe network automation and network orchestration? (Choose two.)
A senior network designer suggests that you should improve network convergence times by reducing BGP timers between your CE router and the PE router of the service provider. Which two factors should you consider to adjust the timer values? (Choose two.)
Which two benefits can software defined networks provide to businesses? (Choose two.)
Which issue poses a challenge for security architects who want end-to-end visibility of their networks?
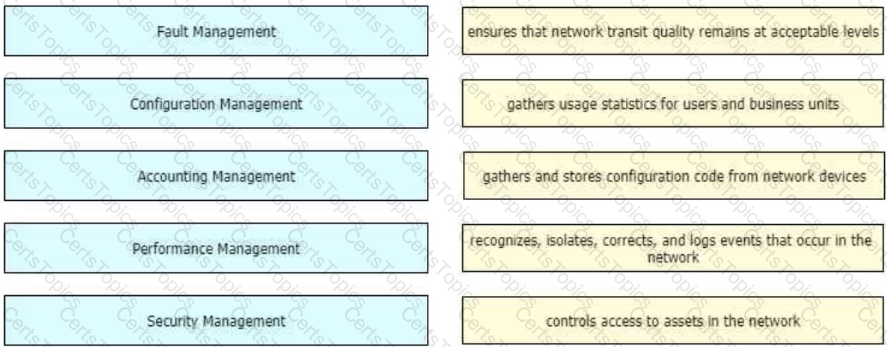
Drag and drop the FCAPS network management reference models from the left onto the correct definitions on the right.
Network changes because of mergers, acquisitions, and divestment can be very disruptive to the network if not carried out carefully. When an organization sells parts of its business, it must detach the affected parts of the network from the rest of the network. Which network design approach is appropriate to minimize the impact and risks as the divested parts of the network are detached?
Refer to the exhibit.
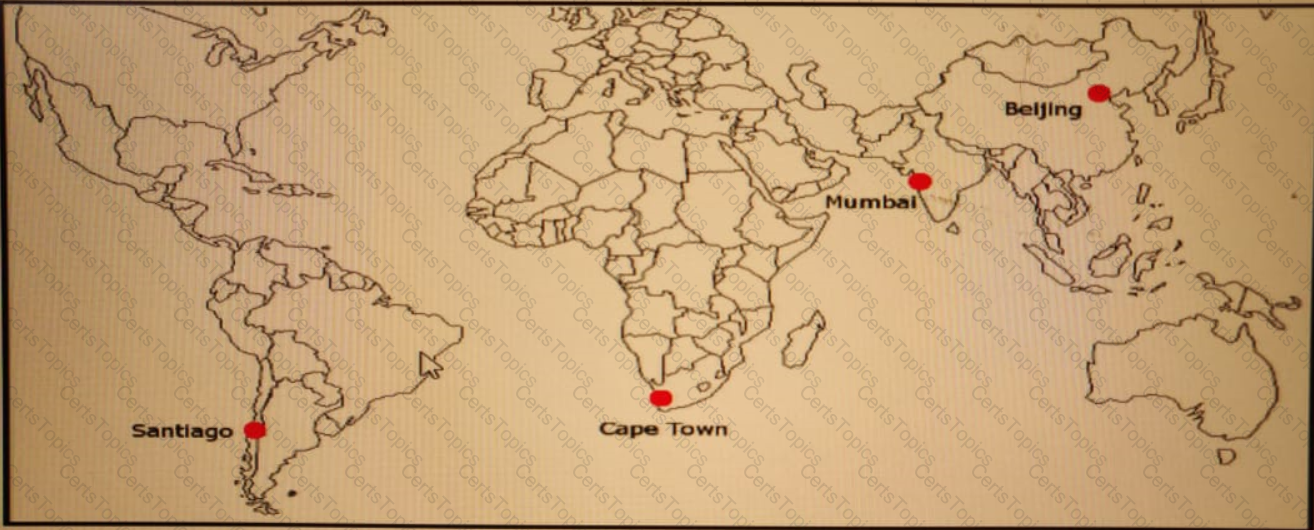
ACME Mining has four data centers in Santiago. Cape Town. Mumbai, and Beijing, full-mesh connected via a 400 Mb/s EVP-LAN They want to deploy a new mission-critical application with these
requirements:
cluster heartbeat 2 Mb/s continuous (250 KB/s)
cluster heartbeat one-way maximum latency 100 ms
These are the current ping tests results between the four data centers:
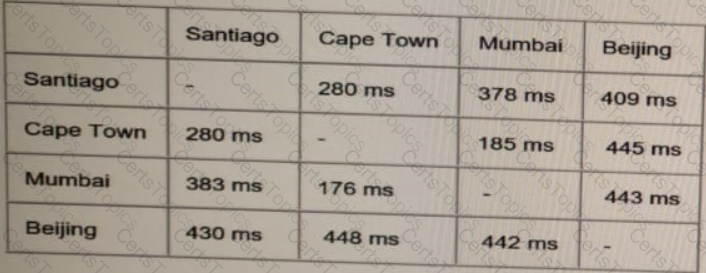
Which hosting data center pair can host the new application?
According to the CIA triad principles for network security design, which principle should be priority for a Zero Trust network?
Network designers often segment networks by creating modules for various reasons Sometimes however a network can be unintentionally segmented For instance, if the only way to connect a remote site to a headquarters or regional site is to connect them both to the public Internet the corporate network is now unintentionally segmented Which of the following option can be used to desegment the network in this situation?
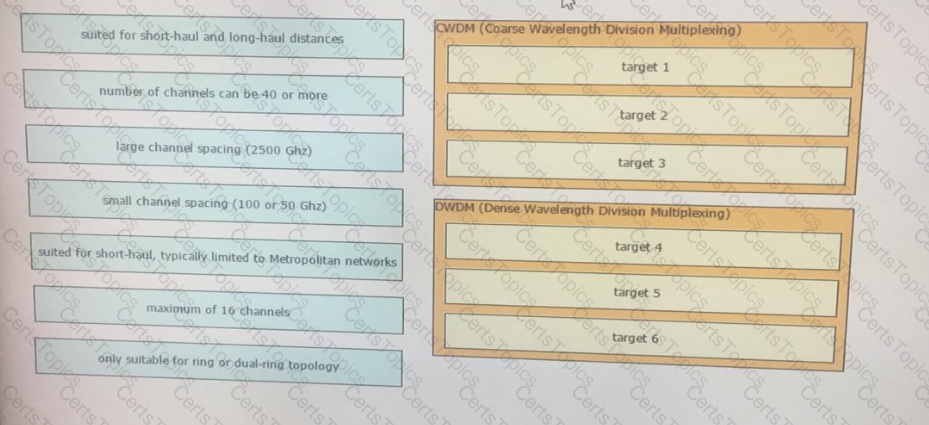
Drag and drop the optical technology design characteristics on the left to the correct optical technologies on the right. Not all options are used
A network attacker exploits application flaws to compromise critical systems in the organization with these objectives:
• Obtain sensitive data and export the data out of the network.
• Compromise developer and administrator credentials to potentially
What is the next step after application discovery is completed in Zero Trust networkings
Creating a network that functions as a strategic part of the business rather than simply being a cost center, starts with a good understanding of business requirements and processes What specific type of knowledge helps to create high-level LAN WAN. and data center designs that support and enable the business?
What are two examples of business goals to be considered when a network design is built? (Choose two.)
IPFIX data collection via standalone IPFIX probes is an alternative to flow collection from routers and switches. Which use case is suitable for using IPFIX probes?\
Which best practice ensures data security in the private cloud?
Which relationship between IBGP and the underlying physical topology is true?
A healthcare customer requested that SNMP traps must be sent over the MPLS Layer 3 VPN service. Which protocol must be enabled?
A large enterprise customer is planning a new WAN connection to its headquarters. The current architecture is
dual homed with static routing, but users complain when a specific link fails. Failure of the other link does not
affect any services or applications. The new WAN connection must provide the headquarters with a resilient
network design and increase the return on investment.
Which solution should be recommended to the customer?
Refer to the exhibit.
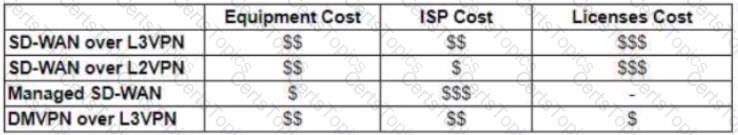
The WAN network of the General Bank of Greece has experienced several outages It takes too long to activate a new branch site The networking department of the bank plans to upgrade the legacy end-of-life WAN network with a new flexible manageable, and scalable in-house solution The number of branches will increase exponentially in the next fiscal year The CTO states that the bank’s mam goal is OPEX reduction The network engineering team prepares a table to evaluate the available options Which WAN technology can be used for the solution?
A network hacker is trying to interrupt the transport packet on IPSEC. A packet with duplicate sequence numbers is introduced. The customer sends high-priority traffic during this window. Which design parameter should be considered to mitigate this issue?
Which BGP feature provides fast convergence?
Company XYZ, a global content provider, owns data centers on different continents Their data center design involves a standard three-layer design with a Layer 3-only core VRRP is used as the FHRP They require VLAN extension across access switches in all data centers, and they plan to purchase a Layer 2 interconnection between two of their data centers in Europe in the absence of other business or technical constraints which termination point is optimal for the Layer 2 interconnection?
As part of workspace digitization, a large enterprise has migrated all their users to Desktop as a Sen/ice (DaaS), by hosting the backend system in their on-premises data center. Some of the branches have started to experience disconnections to the DaaS at periodic intervals, however, local users in the data center and head office do not experience this behavior. Which technology can be used to mitigate this issue?
Drag and drop the design use cases from the left onto the correct uRPF techniques used to prevent spoofing attacks Not all options are used.

Cost is often one of the motivators for a business to migrate from a traditional network to a software- defined network. Which design decision is directly influenced by CAPEX drivers?
An enterprise requires MPLS connected branches to access cloud-based Microsoft 365 services over an SD-WAN solution. Internet access Is available only at dual regional hub sites that are connected to the MPLS network. Which connectivity method provides an optimum access method to the cloud-based services If one ISP suffers loss or latency?
What is a description of a control plane action?
Which two foundational aspects of loT are still evolving and being worked on by the industry at large? (Choose two)
A network security team uses a purpose-built tool to actively monitor the campus network, applications, and user activity. The team also analyzes enterprise telemetry data from IPFIX data records that are received from devices in the campus network. Which action can be taken based on the augmented data?
As network designer, which option is your main concern with regards to virtualizing multiple network zones into a single hardware device?
Which three characteristics of the Single Tier and the Dual Tier Headend Architectures for DMVPN designs are true? (Choose three.)
An enterprise service provider is designing the network for a customer who runs a video application in both a centralized and distributed fashion The team has looked at the following parameters
•The available bandwidth for branches and the associated cost
•Video resource cost
•Usage patterns at hub-and-spoke sites.
•Call agent bridge selection algorithm
Which key piece of information is missing and needs to be taken into consideration in order to determine the correct resource allocation model?
A multicast network is sing Bidirectional PIM. Which two combined actions achieve high availability so that two RPs within the same network can act in a redundant manner? (Choose two)
Which component of the SDN architecture automatically ensures that application traffic is routed according to policies established by network administrators?
Company XYZ is designing their network using the three-layer hierarchical model. At which layer must the QoS design classify or mark the traffic?
You have been asked to design a remote access VPN solution to support up to 2000 devices. You must ensure that only corporate assets are allowed to connect to the VPN, and users must authenticate to gain access of their based on their user role. Users must use a password that they are already using to access existing applications . A user may not always use the same device to access the VPN. Which two options combined meet the requirements? (Choose two)
During evaluation of migrating current on premises infrastructure to add cloud-based infrastructure, a network planning team must meet three core requirements as they make recommendations on which cloud strategy to adopt going forward
• Technology is changing rapidly, therefore the enterprise must be open to adopting new ways of doing things, and be ready to invest CapEx-funds in the next three years
• Network bandwidth capacity requirements are dynamic and are expected to change over the next year
• If new technologies are to be introduced, operational expenses must be kept at a minimum. Which cloud strategy meets these requirements?
A network security team observes phishing attacks on a user machine from a remote location. The organization has a policy of saving confidential data on two different systems using different types of authentication. What is the next step to control such events after the security team verifies all users in Zero Trust modeling?
Which statement about hot-potato routing architecture design is true?
Drag and drop the multicast protocols from the left onto the current design situation on the right.
A BGP route reflector in the network is taking longer than expected to coverage during large network changes. Troubleshooting shows that the router cannot handle all the TCP acknowledgements during route updates. Which action can be performed to tune the device performance?
Company XYZ connects its sites over a private WAN. Their overlay network is running a DMVPN setup where the headquarters site is the hub. The company is planning on implementing multicast routing on the network. What should be used in the multicast routing design?
Agile and Waterfall are two popular methods for organizing projects. What describes any Agile network design development process?
It is often seen that companies pick a cloud vendor solely based on technical preferences without putting enough weight on the business strategies that are driving the cloud initiatives Which strategic requirement may come into play where it is more likely that the decision makers will look to leverage laaS over SaaS or PaaS?
You are designing the routing design for two merging companies that have overlapping IP address space. Which of these must you consider when developing the routing and NAT design?
Which two control plane policer designs must be considered to achieve high availability? (Choose two.)
Which two statements about MLD snooping are true? (Choose two)
A green data center is being deployed and a design requirement is to be able to readily scale server virtualization Which IETF standard technology can provide this requirement?
An engineer is designing the QoS strategy for Company XYZ. Based on initial analysis, a lot of scavenger type of traffic is traversing the network's 20Mb Internet link toward the service provider. The new design must use a QoS technique that limits scavenger traffic to 2 Mbps, which helps avoid oversubscription of the link during times of congestion. Which QoS technique can be used to facilitate this requirement?
The General Bank of Greece plans to upgrade its legacy end-of-life WAN network with a new flexible, manageable, and scalable solution. The mam requirements are ZTP support, end-to-end encryption application awareness and segmentation. The CTO states that the main goal of the bank is CAPEX reduction. Which WAN technology should be used for the solution?
Which two technologies enable multilayer segmentation? (Choose two.)
As a service provider is implementing Strong Access Control Measures, which two of the following PCI Data Security Standard requirements must be met’ (Choose two.)
What is a disadvantage of the traditional three-tier architecture model when east west traffic between different pods must go through the distribution and core layers?
You are designing a network running both IPv4 and IPv6 to deploy QoS Which consideration is correct about the QoS for IPv4 and IPv6?
In the wake of a security compromise incident where the internal networks were breached by an outside attacker at the perimeter of the infrastructure, an enterprise is now evaluating potential measures that can help protect against the same type of incident in the future. What are two design options that can be employed? (Choose two)
An architect receives a functional requirement for a NAC system from a customer security policy stating that if a corporate Wi-Fi device does not meet current AV definitions, then it cannot access the corporate network until the definitions are updated. Which component should be built into the NAC design?
The cloud like the Internet is a massive network of independent resources that are designed to be fault tolerant Software components that run in the cloud have no dependencies on the underlying infrastructure which may fail at any time Which two constraints of REST are important when building cloud-based solutions'? (Choose two )
Which two pain points are the most common for container technology adoption? (Choose two)
While reviewing an existing network design, you are discussing the characteristics of different STP versions. Which protocol minimizes unicast flooding during a Topology Change Notification in a Layer 2 switched network with many VLANs?
A healthcare provider discovers that protected health information of patients was altered without patient consent. The healthcare provider is subject to HIPAA compliance and is required to protect PHI data. Which type of security safeguard should be implemented to resolve this issue?
An existing wireless network was designed to support data traffic only. You must now install context Aware services for location tracking changes must be applied to the existing wireless network to increase the location accuracy? (Chose two)
Which solution component helps to achieve comprehensive threat protection and compliance for migration to multicloud SDX architectures?
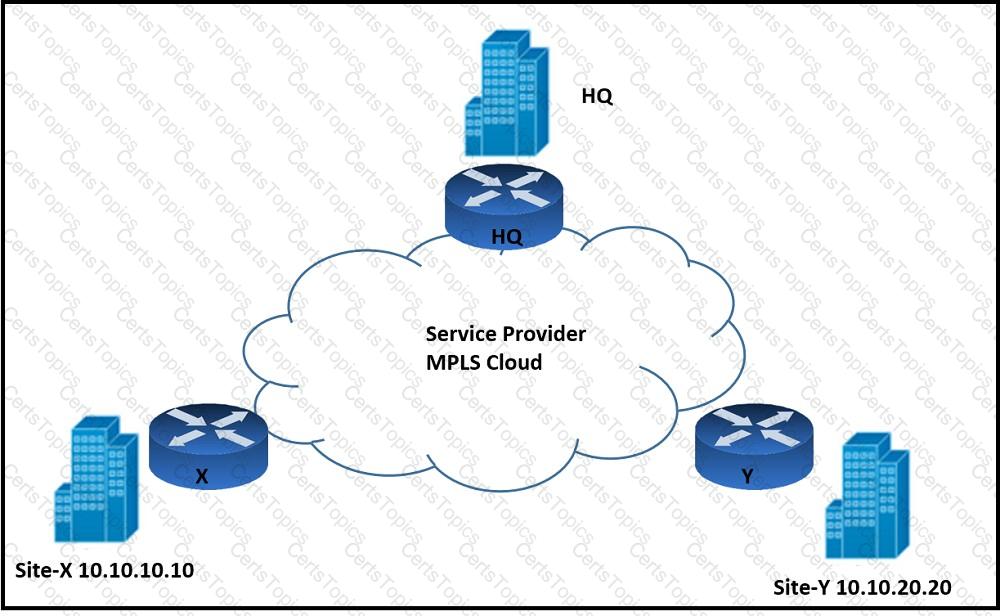
Refer to the exhibit. An architect must design an enterprise WAN that connects the headquarters with 22 branch offices. The number of remote sites is expected to triple in the next three years. The final solution must comply with these requirements:
Only the loopback address of each of the enterprise CE X and Y routers must be advertised to the interconnecting service provider cloud network.
The transport layer must carry the VPNv4 label and VPN payload over the MP-BGP control plane.
The transport layer must not be under service provider control.
Which enterprise WAN transport virtualization technique meets the requirements?
Company XYZ was not satisfied with the reconvergence time OSPF is taking. BFD was implemented to try to reduce the reconvergence time, but the network is still experiencing delays when having to reconverge. Which technology will improve the design?
Company ABC uses IPv4-only. Recently they started deploying new endpoint devices. For operational reasons, IPv6 cannot be disabled on these new endpoint devices. Which security measure prevents the new endpoint from learning an IPv6 prefix from an attacker?
Company XYZ wants design recommendations for Layer 2 redundancy (using Layer 2 technologies) The company wants to prioritize flexibility and scalability elements in the new design Which two technologies help meet these requirements'? (Choose two)
Which action must be taken before new VoIP systems are implemented on a network to ensure that the network is ready to handle the traffic?
Which two descriptions of CWDM are true? (Choose two)
If the desire is to connect virtual network functions together to accommodate different types of network service connectivity what must be deployed?
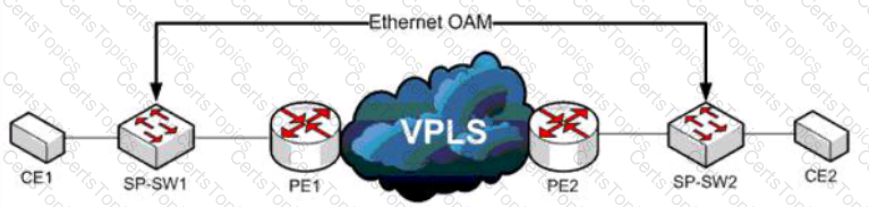
Refer to the exhibit A service provider has a requirement to use Ethernet OAM to detect end-to-end connectivity failures between SP-SW1 and SP- SW2 Which two ways to design this solution are true? (Choose two)
A customer asks you to perform a high level review of their upcoming WAN refresh for remote sites The review is specially focused on their retail store operations consisting of 500+ locations connected via mutlipoint IPsec VPN solution. Which routing protocol would be valid but would also be the most restrictive for the expansion of this deployment model?
The SD-WAN architecture is composed of separate orchestration management, control, and data planes Which activity happens at the orchestration plane?
Refer to the diagram.
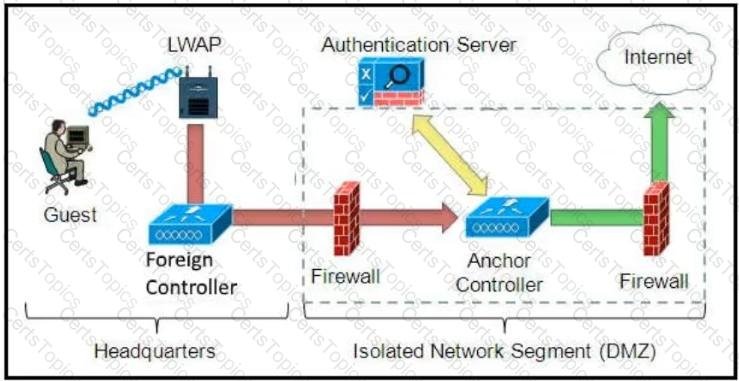
Which solution must be used to send traffic from the foreign wireless LAN controller to the anchor wireless LAN controller?
Which two features control multicast traffic in a VLAN environment? (Choose two)
Which purpose of a dynamically created tunnel interface on the design of IPv6 multicast services Is true?
Scrum is a subset of Agile and is a lightweight process framework for Agile development Which role becomes the interface between the business the customers and their product-related needs on one side and the Team on the other?