Cisco Related Exams
400-007 Exam







The Cisco 400-007 exam focuses on your expertise in translating business and technical needs into network designs. Key areas include:
CertsTopics offers a variety of high-quality study materials for the CCDE v3.0 Certification Exam, including 400-007 PDFs and testing engine tools. Our 400-007 study materials are designed to mirror the exam’s format, giving you a real exam experience.
What is the most important operational driver in building a resilient and secure modular network design?
Which component of the SDN architecture automatically ensures that application traffic is routed according to policies established by network administrators?
Refer to the exhibit.
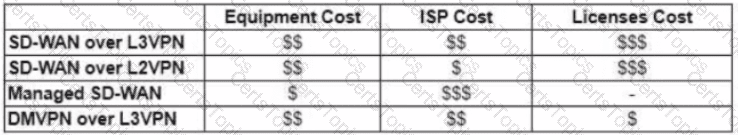
The WAN network of the General Bank of Greece has experienced several outages. It takes too long to activate a new branch site. The networking department of the bank plans to upgrade the legacy end-of-life WAN network with a new flexible, manageable, and scalable in-house solution. The number of branches will increase exponentially in the next fiscal year. The CTO states that the bank’s main goal is OPEX reduction. The network engineering team prepares a table to evaluate the available options. Which WAN technology can be used for the solution?