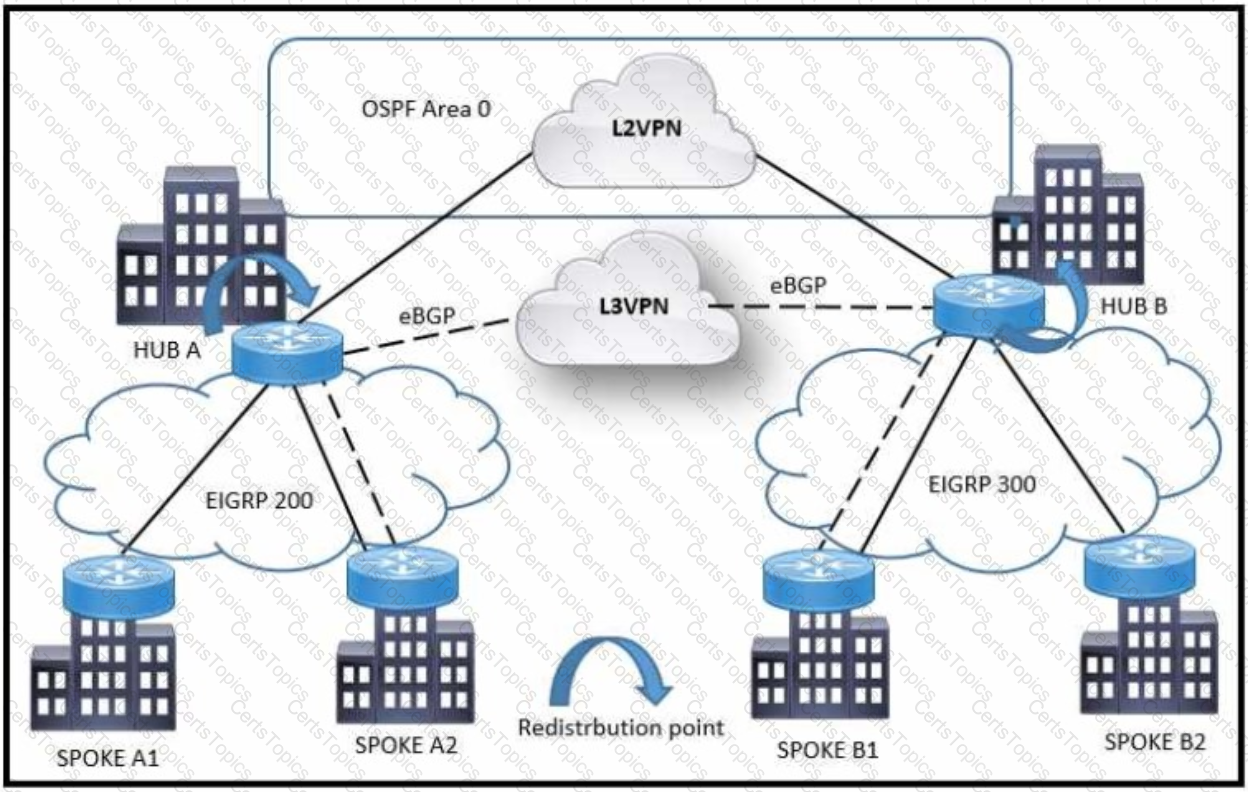
Refer to the exhibit A customer network design team is planning a migration from a legacy TDM-based L2VPN to an MPLS-based L3VPN Migration is planned in a phased approach:
•OSPF backbone Link between HUB A and HUB B sites to be migrated to eBGP
•Spoke A2 and Spoke B1 will be migrated to the L3VPN
Which solution design can be considered to avoid routing loops during backbone link migration?
Which two statements describe the hierarchical LAN design model? (Choose two)
The administrator of a small branch office wants to implement the Layer 2 network without running STP The office has some redundant paths Which mechanism can the administrator use to allow redundancy without creating Layer 2 loops?
A business customer deploys workloads in the public cloud. Now the customer network faces governance issues with the flow of IT traffic and must ensure the security of data and intellectual property. Which action helps to identify the issue for further resolution?