Which of the following attacks are associated with an ICMP protocol?
Ping of death
Smurf attack
ICMP flooding
All of the following
ICMP (Internet Control Message Protocol), per RFC 792, handles diagnostics (e.g., ping) and errors in IP networks. It’s exploitable in:
A. Ping of Death:
Method: Sends oversized ICMP Echo Request packets (>65,535 bytes) via fragmentation. Reassembly overflows buffers, crashing older systems (e.g., Windows 95).
Fix: Modern OSes cap packet size (e.g., ping -s 65500).
B. Smurf Attack:
Method: Spoofs ICMP Echo Requests to a network’s broadcast address (e.g., 192.168.255.255). All hosts reply, flooding the victim.
Amplification: 100 hosts = 100x traffic.
C. ICMP Flooding:
Method: Overwhelms a target with ICMP Echo Requests (e.g., ping -f), consuming bandwidth/CPU.
Variant: BlackNurse attack targets firewalls.
Technical Details:
ICMP Type 8 (Echo Request), Type 0 (Echo Reply) are key.
Mitigation: Rate-limit ICMP, disable broadcasts (e.g., no ip directed-broadcast).
Security Implications:ICMP attacks are DoS vectors. CNSP likely teaches filtering (e.g., iptables -p icmp -j DROP) balanced with diagnostics need.
Why other options are incorrect:
A, B, C individually:All are ICMP-based; D is comprehensive.
Real-World Context:Smurf attacks peaked in the 1990s; modern routers block them by default.References:CNSP Official Study Guide (Network Attacks); RFC 792 (ICMP).
What ports does an MSSQL server typically use?
1433/TCP, 2433/UDP, and 3433/TCP
1433/TCP, 1434/UDP, and 1434/TCP
1433/TCP, 2433/UDP, and 1434/TCP
1533/TCP, 1434/UDP, and 2434/TCP
Microsoft SQL Server (MSSQL) relies on specific ports for its core services, as defined by Microsoft and registered with IANA:
1433/TCP:The default port for the SQL Server Database Engine. Clients connect here for querying databases (e.g., via ODBC or JDBC). It’s a well-known port, making it a frequent target for attacks if exposed.
1434/UDP:Used by theSQL Server Browser Service, which listens for incoming requests and redirects clients to the correct port/instance (especially for named instances). It’s critical for discovering dynamic ports when 1433 isn’t used.
1434/TCP:Less commonly highlighted but used in some configurations, such as dedicated admin connections (DAC) or when the Browser Service responds over TCP for specific instances. While 1433/TCP is the primary engine port, 1434/TCP can be involved in multi-instance setups.
Technical Details:
Ports can be customized (e.g., via SQL Server Configuration Manager), but these are defaults.
Named instances often use dynamic ports (allocated from the ephemeral range), with the Browser Service (1434/UDP) guiding clients to them.
Firewalls must allow these ports for MSSQL to function externally, posing risks if not secured (e.g., brute-force attacks on 1433/TCP).
Security Implications:CNSP likely covers MSSQL port security, as vulnerabilities like SQL Slammer (2003) exploited 1434/UDP misconfigurations. Hardening includes restricting access, changing defaults, and monitoring traffic.
Why other options are incorrect:
A. 1433/TCP, 2433/UDP, 3433/TCP:2433/UDP and 3433/TCP are not MSSQL standards; they’re likely typos or unrelated ports.
C. 1433/TCP, 2433/UDP, 1434/TCP:2433/UDP is incorrect; 1434/UDP is the Browser Service port.
D. 1533/TCP, 1434/UDP, 2434/TCP:1533/TCP and 2434/TCP aren’t associated with MSSQL; they deviate from documented defaults.
Real-World Context:Tools like netstat -an | find "1433" on Windows confirm MSSQL’s port usage during audits.References:CNSP Official Documentation (Database Security and Ports); Microsoft SQL Server Documentation, IANA Port Registry.
The application is showing a TLS error message as a result of a website administrator failing to timely renew the TLS certificate. But upon deeper analysis, it appears that the problem is brought on by the expiration of the TLS certificate. Which of the following statements is correct?
The communication between the browser and the server is now no longer over TLS.
The communication between the browser and the server is still over TLS.
TLS (Transport Layer Security)secures communication (e.g., HTTPS) using certificates, per RFC 8446. A certificate includes:
Validity Period:Start and end dates (e.g., "Not After: March 8, 2025").
Purpose:Authenticates the server and encrypts the session.
Scenario:An expired TLS certificate (e.g., past "Not After" date). Modern browsers (e.g., Chrome, Firefox) validate certificates during the handshake:
ClientHello:Browser initiates TLS.
ServerHello:Server sends its certificate.
Validation:Browser checks expiration, CA trust, etc.
If expired, browsers reject the handshake, displaying errors (e.g., "NET::ERR_CERT_DATE_INVALID"). No session key is negotiated, andcommunication doesn’t proceed over TLS. Users may bypass warnings (e.g., "Advanced > Proceed"), but this is unencrypted or uses a fallback (not standard TLS), breaking security guarantees.
Security Implications:Expired certificates expose sites to MITM attacks, as trust is lost. CNSP likely emphasizes certificate management (e.g., automation with Let’s Encrypt) to avoid this.
Why other options are incorrect:
B. The communication is still over TLS:False; an expired certificate halts the TLS handshake in compliant browsers. Legacy systems might negotiate insecurely, but this isn’t "TLS" per standards.
Real-World Context:The 2019 Equifax breach partially stemmed from expired certificates missing vulnerabilities.References:CNSP Official Study Guide (TLS/SSL Security); RFC 8446 (TLS 1.3).
Which of the following services do not encrypt its traffic by default?
DNS
SSH
FTPS
All of these
Encryption ensures confidentiality and integrity of network traffic. Analyzing defaults:
A. DNS (Domain Name System):
Default: Unencrypted (UDP/TCP 53), per RFC 1035. Queries/responses (e.g., “google.com → 142.250.190.14”) are plaintext.
Modern Options: DNS over HTTPS (DoH, TCP 443) or DNS over TLS (DoT, TCP 853) encrypt, but aren’t default in most systems (e.g., pre-2020 Windows).
B. SSH (Secure Shell):
Default: Encrypted (TCP 22), per RFC 4251. Uses asymmetric (e.g., RSA) and symmetric (e.g., AES) crypto for all sessions.
C. FTPS (FTP Secure):
Default: Encrypted (TCP 21 control, dynamic data ports). Extends FTP with SSL/TLS (e.g., RFC 4217), securing file transfers.
Technical Details:
DNS: Plaintext exposes queries to eavesdropping (e.g., ISP snooping) or spoofing (e.g., cache poisoning).
SSH/FTPS: Encryption is baked into their standards; disabling it requires explicit misconfiguration.
Security Implications:Unencrypted DNS risks privacy and integrity (e.g., Kaminsky attack). CNSP likely pushes DoH/DoT adoption.
Why other options are incorrect:
B, C:Encrypt by default.
D:False, as only DNS lacks default encryption.
Real-World Context:The 2013 Snowden leaks exposed DNS monitoring; DoH uptake (e.g., Cloudflare 1.1.1.1) counters this.References:CNSP Official Study Guide (Protocol Security); RFC 1035 (DNS), RFC 4251 (SSH).
Which Kerberos ticket is required to generate a Silver Ticket?
Session Ticket
Ticket-Granting Ticket
Service Account Ticket
There is no specific ticket required for generating a Silver Ticket
ASilver Ticketis a forged KerberosService Ticket (TGS - Ticket Granting Service)in ActiveDirectory, granting access to a specific service (e.g., MSSQL, CIFS) without KDC interaction. Unlike a Golden Ticket (TGT forgery), it requires:
Service Account’s NTLM Hash:The target service’s account (e.g., MSSQLSvc) hash, not a ticket.
Forgery: Tools like Mimikatz craft the TGS (e.g., kerberos::golden /service:
Kerberos Flow (RFC 4120):
TGT (Ticket-Granting Ticket): Obtained via AS (Authentication Service) with user creds.
TGS: Requested from TGS (Ticket Granting Service) using TGT for service access.
Silver Ticket Process:
No TGT needed; the attacker mimics the TGS step using the service account’s stolen hash (e.g., from a compromised host).
C. Service Account Ticket:Misnomer—it’s the hash of the service account (e.g., MSSQLSvc) that enables forgery, not a pre-existing ticket. CNSP’s phrasing likely tests this nuance.
Security Implications:Silver Tickets are stealthier than Golden Tickets (service-specific, shorter-lived). CNSP likely stresses hash protection (e.g., LAPS) and Kerberos monitoring.
Why other options are incorrect:
A. Session Ticket:Not a Kerberos term; confuses session keys.
B. TGT:Used for Golden Tickets, not Silver.
D:Incorrect; the service account’s hash (implied by “ticket”) is essential.
Real-World Context:Silver Tickets exploited in APT29 attacks (2020 SolarWinds) for lateral movement.References:CNSP Official Documentation (Kerberos Attacks); RFC 4120 (Kerberos).
What RID is given to an Administrator account on a Microsoft Windows machine?
0
500
501
100
In Windows, security principals (users, groups) are identified by aSecurity Identifier (SID), formatted as S-1-<authority>-
RID 500:Assigned to the built-inAdministratoraccount on every Windows machine (e.g., S-1-5-21-
Created during OS install, with full system privileges.
Disabled by default in newer Windows versions (e.g., 10/11) unless explicitly enabled.
RID 501:Guest account (e.g., S-1-5-21-
Technical Details:
Stored in SAM (C:\Windows\System32\config\SAM).
Enumeration: Tools like wmic useraccount or net user reveal RIDs.
Domain Context: Domain Admins use RID 512, but the question specifies a local machine.
Security Implications:RID 500 is a prime target for brute-forcing or pass-the-hash attacks (e.g., Mimikatz). CNSP likely advises renaming/disabling it (e.g., via GPO).
Why other options are incorrect:
A. 0:Reserved (e.g., Null SID, S-1-0-0), not a user RID.
C. 501:Guest, not Administrator.
D. 100:Invalid; local user RIDs start at 1000 (e.g., custom accounts).
Real-World Context:Post-compromise, attackers query RID 500 (e.g., net user Administrator) for privilege escalation.References:CNSP Official Study Guide (Windows Security); Microsoft SID Documentation.
On a Microsoft Windows operating system, what does the following command do?
net localgroup Sales Sales_domain /add
Display the list of the users of a local group Sales
Add a domain group to the local group Sales
Add a new user to the local group Sales
Add a local group Sales to the domain group
The net localgroup command manages local group memberships on Windows systems, with syntax dictating its action.
Why B is correct:net localgroup Sales Sales_domain /add adds the domain group Sales_domain to the local group Sales, granting its members local group privileges. CNSP covers this for privilege escalation testing.
Why other options are incorrect:
A:Displaying users requires net localgroup Sales without /add.
C:Adding a user requires a username, not a group name like Sales_domain.
D:The reverse (local to domain) uses net group, not net localgroup.
References:CNSP "Windows Group Management" (Section on net Commands) explains net localgroup for adding domain groups.
Which one of the following services is not a UDP-based protocol?
SNMP
NTP
IKE
SSH
Protocols are defined by their transport layer usage (TCP or UDP), impacting their security and performance characteristics.
Why D is correct:SSH (Secure Shell) uses TCP (port 22) for reliable, connection-oriented communication, unlike the UDP-based options. CNSP contrasts TCP and UDP protocol security.
Why other options are incorrect:
A:SNMP uses UDP (ports 161, 162) for lightweight network management.
B:NTP uses UDP (port 123) for time synchronization.
C:IKE (IPsec key exchange) uses UDP (ports 500, 4500).
References:CNSP "Network Protocols" (Section on Transport Layer) identifies SSH as TCP-based, others as UDP.
Which is the correct command to change the MAC address for an Ethernet adapter in a Unix-based system?
ifconfig eth0 hw ether AA:BB:CC:DD:EE:FF
ifconfig eth0 hdw ether AA:BB:CC:DD:EE:FF
ifconfig eth0 hdwr ether AA:BB:CC:DD:EE:FF
ifconfig eth0 hwr ether AA:BB:CC:DD:EE:FF
In Unix-based systems (e.g., Linux), the ifconfig command is historically used to configure network interfaces, including changing the Media Access Control (MAC) address of an Ethernet adapter. The correct syntax to set a new MAC address for an interface like eth0 is ifconfig eth0 hw ether AA:BB:CC:DD:EE:FF, where hw specifies the hardware address type (ether for Ethernet), followed by the new MAC address in colon-separated hexadecimal format.
Why A is correct:The hw ether argument is the standard and correct syntax recognized by ifconfig to modify the MAC address. This command temporarily changes the MAC address until the system reboots or the interface is reset, assuming the user has sufficient privileges (e.g., root). CNSP documentation on network configuration and spoofing techniques validates this syntax for testing network security controls.
Why other options are incorrect:
B:hdw is not a valid argument; it’s a typographical error and unrecognized by ifconfig.
C:hdwr is similarly invalid; no such shorthand exists in the command structure.
D:hwr is incorrect; the full keyword hw followed by ether is required for proper parsing.
References:CNSP "Network Interface Configuration" (Section on MAC Address Manipulation) confirms ifconfig eth0 hw ether as the standard command, noting its use in penetration testing for spoofing scenarios.
Which of the following is not a DDoS attack?
SYN Flood
NTP Amplification
UDP Flood
Brute Force
DDoS (Distributed Denial of Service) attacks aim to overwhelm a target’s resources with excessive traffic, disrupting availability, whereas other attack types target different goals.
Why D is correct:Brute force attacks focus on guessing credentials (e.g., passwords) to gain unauthorized access, not on denying service. CNSP classifies it as an authentication attack, not a DDoS method.
Why other options are incorrect:
A:SYN Flood exhausts TCP connection resources, a classic DDoS attack.
B:NTP Amplification leverages amplified responses to flood targets, a DDoS technique.
C:UDP Flood overwhelms a system with UDP packets, another DDoS method.
References:CNSP "DDoS Attack Types" (Section on Attack Classification) excludes brute force from DDoS categories, listing SYN, NTP, and UDP floods as examples.
In a Linux-based architecture, what does the /mnt directory contain?
Temporary-mounted filesystems
System configuration files and initialization scripts
Loadable driver modules needed to boot the system
System files which represent the current state of the kernel
The LinuxFilesystem Hierarchy Standard (FHS), per FHS 3.0, defines directory purposes:
/mnt:Designated fortemporarily mounted filesystems, typically by system administrators.
Use: Mount points for removable media (e.g., USB drives: mount /dev/sdb1 /mnt/usb) or network shares (e.g., NFS).
Nature: Transient, user-managed, not persistent across reboots (unlike /etc/fstab mounts).
Contrast:
/media:Auto-mounts removable devices (e.g., by desktop environments like GNOME).
/mnt vs. /media:/mnt is manual, /media is system-driven.
Technical Details:
Empty by default; subdirectories (e.g., /mnt/usb) are created as needed.
Permissions: Typically root-owned (0755), requiring sudo for mounts.
Security Implications:Misconfigured /mnt mounts (e.g., world-writable) risk unauthorized access. CNSP likely covers mount security (e.g., nosuid option).
Why other options are incorrect:
B. System config/init scripts:Found in /etc (e.g., /etc/passwd, /etc/init.d).
C. Driver modules:Located in /lib/modules/
D. Kernel state:Resides in /proc (e.g., /proc/cpuinfo).
Real-World Context:Admins mount ISOs at /mnt during server provisioning (e.g., mount -o loop image.iso /mnt).References:CNSP Official Study Guide (Linux Filesystems); FHS 3.0 Documentation.
Which one of the following is a phishing email?
Only A
Only B
Both A and B
None of the above
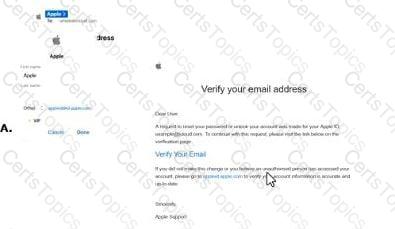
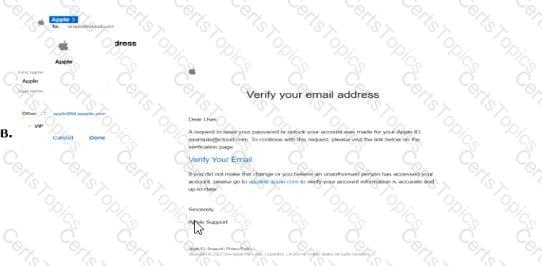
The screenshot shows an email labeled "B" with the subject "Verify your email address" purportedly from Apple. To determine if this is a phishing email, we need to analyze its content and characteristics against common phishing indicators as outlined in CNSP documentation. Since option A is not provided in the screenshot, we will evaluate email B and infer the context for A.
Analysis of Email B:
Sender and Branding:The email claims to be from "Apple Support" and includes an Apple logo, which is a common tactic to establish trust. However, phishing emails often impersonate legitimate brands like Apple to deceive users.
Subject and Content:The subject "Verify your email address" and the body requesting the user to verify their email by clicking a link ("Verify Your Email") are typical of phishing attempts. Legitimate companies like Apple may send verification emails, but the tone and context here raise suspicion.
Link Presence:The email contains a clickable link ("Verify Your Email") that is purportedly for email verification. The screenshot does not show the URL, but phishing emails often include malicious links that lead to fake login pages to steal credentials. CNSP emphasizes that unsolicited requests to click links for verification are a red flag.
Urgency and Vague Instructions:The email includes a statement, "If you did not make this change or believe an unauthorized person has accessed your account, click here to cancel and secure your account." This creates a sense of urgency, a common phishing tactic to prompt immediate action without critical thinking.
Generic Greeting:The email starts with "Dear User," a generic greeting often used in phishing emails. Legitimate companies like Apple typically personalize emails with the user’s name.
Suspicious Elements:The email mentions "your Apple ID (example@icloud.com)," which is a placeholder rather than a specific email address, further indicating a mass phishing campaign rather than a targeted, legitimate communication.
Phishing Indicators (per CNSP):CNSP documentation on phishing identification lists several red flags:
Unsolicited requests for verification or account updates.
Generic greetings (e.g., "Dear User" instead of a personalized name).
Presence of links that may lead to malicious sites (not verifiable in the screenshot but implied).
Urgency or threats (e.g., "click here to cancel and secure your account").
Impersonation of trusted brands (e.g., Apple).Email B exhibits multiple indicators: the generic greeting, unsolicited verification request, urgent call to action, and impersonation of Apple.
Option A Context:Since the screenshot only shows email B, and the correct answer is "Only B," we can infer that email A (not shown) does not exhibit phishing characteristics. For example, A might be a legitimate email from Apple with proper personalization, no suspicious links, or a different context (e.g., a purchase confirmation rather than a verification request).
Evaluation of Options:
1. Only A:Incorrect, as email A is not shown, and the correct answer indicates B asthe phishing email.
2. Only B:Correct. Email B shows clear phishing characteristics, such as impersonation, a generic greeting, an unsolicited verification link, and urgency, aligning with CNSP’s phishing criteria.
3. Both A and B:Incorrect, as A is implied to be non-phishing based on the correct answer.
4. None of the above:Incorrect, as B is a phishing email.
Conclusion:Email B is a phishing email due to its impersonation of Apple, generic greeting, unsolicited verification request with a link, and use of urgency to prompt action. Since A is not shown but implied to be non-phishing, the correct answer is "Only B."
References:CNSP "Social Engineering Attacks" (Section on Phishing Identification) lists key phishing indicators such as impersonation, generic greetings, unsolicited links, and urgency, all of which are present in email B. The section also contrasts phishing emails with legitimate communications, emphasizing personalization and context as differentiators.
Where are the password hashes stored in the Linux file system?
/etc/passwd
/etc/password
/etc/shadow
/usr/bin/shadow
In Linux, password hashes are stored in a secure file to protect user authentication data. The evolution of Linux security practices moved password storage from plaintext or weakly protected files to a more secure location.
Why C is correct:The /etc/shadow file is the standard location for storing password hashes in modern Linux systems. This file is readable only by the root user, enhancing security by restricting access. It contains encrypted password hashes (typically using algorithms like SHA-512), along with user details such as password expiration policies. CNSP documentation on Linux security emphasizes /etc/shadow as the authoritative source for password hashes, replacing older methods.
Why other options are incorrect:
A. /etc/passwd:Historically, /etc/passwd stored passwords in plaintext or weakly hashed forms (e.g., using DES), but modern systems use it only for user account information (e.g., UID, GID, home directory) and reference /etc/shadow for hashes.
B. /etc/password:This is not a valid file in the Linux file system; it appears to be a typographical error or misunderstanding, with no recognized role in password storage.
D. /usr/bin/shadow:/usr/bin contains executable binaries, not configuration or data files like password hashes. /etc/shadow is the correct path.
References:CNSP "Linux Authentication Mechanisms" (Section on Password Storage) details the transition to /etc/shadow for enhanced security and contrasts it with /etc/passwd.
How many usable TCP/UDP ports are there?
65536
65535
63535
65335
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) port numbers are defined by a 16-bit field in their packet headers, as specified in RFC 793 (TCP) and RFC 768 (UDP). A 16-bit integer ranges from 0 to 65,535, yielding a total of 65,536 possible ports (2^16). However,port 0is universally reserved across both protocols and is not considered "usable" for standard network communication. According to the Internet Assigned Numbers Authority (IANA), port 0 is designated for special purposes, such as indicating an invalid or dynamic port assignment in some systems (e.g., when a client requests an ephemeral port). In practice, operating systems and applications avoid binding to port 0 for listening services, and it’s often used in error conditions or as a placeholder in protocol implementations (e.g., socket programming).
Thus, theusable port rangespans from 1 to 65,535, totaling 65,535 ports. These ports are categorized by IANA into:
Well-Known Ports (0–1023):Reserved for system services (e.g., HTTP on 80/TCP). Note that 0 is still reserved within this range.
Registered Ports (1024–49151):Assigned to user applications.
Dynamic/Ephemeral Ports (49152–65535):Used temporarily by clients.
From a security perspective, understanding the usable port count is critical for firewall configuration, port scanning (e.g., with Nmap), and detecting anomalies (e.g., services binding to unexpected ports). Misconfiguring a system to use port 0 could lead to protocol errors or expose vulnerabilities, though it’s rare. The CNSP curriculum likely emphasizes this distinction to ensure practitioners can accurately scope network security assessments.
Why other options are incorrect:
A. 65536:This reflects the total number of possible ports (0–65535), but it includes the reserved port 0, which isn’t usable for typical TCP/UDP communication. In security contexts, including port 0 in a count could lead to misconfigured rules or scanning errors.
C. 63535:This is an arbitrary number with no basis in the 16-bit port structure. It might stem from a typo or misunderstanding (e.g., subtracting 2000 from 65535 incorrectly), but it’s invalid.
D. 65335:Similarly, this lacks grounding in protocol standards. It could be a miscalculation (e.g., subtracting 200 from 65535), but it doesn’t align with TCP/UDP specifications.
Real-World Context:In penetration testing, tools like Nmap scan ports 1–65535 by default, excluding 0 unless explicitly specified (e.g., -p0-65535), reinforcing that 65,535 is the practical usable count.References:CNSP Official Study Guide (Network Protocols and Ports); RFC 793 (TCP), RFC 768 (UDP), IANA Service Name and Transport Protocol Port Number Registry.
What ports can be queried to perform a DNS zone transfer?
53/TCP
53/UDP
Both 1 and 2
None of the above
A DNS zone transfer involves replicating the DNS zone data (e.g., all records for a domain) from a primary to a secondary DNS server, requiring a reliable transport mechanism.
Why A is correct:DNS zone transfers use TCP port 53 because TCP ensures reliable,ordered delivery of data, which is critical for transferring large zone files. CNSP notes that TCP is the standard protocol for zone transfers (e.g., AXFR requests), as specified in RFC 5936.
Why other options are incorrect:
B. 53/UDP:UDP port 53 is used for standard DNS queries and responses due to its speed and lower overhead, but it is not suitable for zone transfers, which require reliability over speed.
C. Both 1 and 2:This is incorrect because zone transfers are exclusively TCP-based, not UDP-based.
D. None of the above:Incorrect, as 53/TCP is the correct port for DNS zone transfers.
References:CNSP "DNS Security Practices" (Section on Zone Transfers) specifies TCP port 53 as the protocol for secure and reliable zone transfer operations.
Which one of the following is not an online attack?
Brute force attack
Rainbow table attack
Password spraying attack
Phishing attack
Online attacks require real-time interaction with a target system (e.g., a login interface), whereas offline attacks occur without direct system interaction, typically after obtaining data like password hashes. A rainbow table attack is an offline method that uses precomputed tables of hash values to reverse-engineer passwords from stolen hash databases, distinguishing it from the other options, which are online.
Why B is correct:Rainbow table attacks are performed offline after an attacker has already acquired a hash (e.g., from a compromised database). The attacker matches the hash against precomputed tables to find the plaintext password, requiring no interaction with the target system during the attack. CNSP classifies this as an offline password recovery technique.
Why other options are incorrect:
A:Brute force attacks involve repeatedly submitting password guesses to a live system (e.g., via SSH or a web login), making it an online attack.
C:Password spraying attacks test a few common passwords across many accounts on a live system, also an online attack aimed at avoiding lockouts.
D:Phishing attacks trick users into submitting credentials through fake interfaces (e.g., emails or websites), requiring real-time interaction and thus classified as online.
References:CNSP "Password Attack Methodologies" (Section on Online vs. Offline Attacks) defines rainbow table attacks as offline and contrasts them with online methods like brute force and phishing.
The Management Information Base (MIB) is a collection of object groups that is managed by which service?
SMTP
SNMP
NTP
TACACS
TheManagement Information Base (MIB)is a structured database defining manageable objects (e.g., CPU usage, interface status) in a network device. It’s part of theSNMP (Simple Network Management Protocol)framework, per RFC 1157, used for monitoring and managing network devices (e.g., routers, switches).
SNMP Mechanics:
MIB Structure:Hierarchical, with Object Identifiers (OIDs) like 1.3.6.1.2.1.1.1.0 (sysDescr).
Versions:SNMPv1, v2c (community strings), v3 (encrypted).
Ports:UDP 161 (agent), 162 (traps).
Operation:Agents expose MIB data; managers (e.g., Nagios) query it via GET/SET commands.
MIB files (e.g., IF-MIB, HOST-RESOURCES-MIB) are vendor-specific or standardized, parsed by SNMP tools (e.g., snmpwalk). CNSP likely covers SNMP for network monitoring and securing it against enumeration (e.g., weak community strings like "public").
Why other options are incorrect:
A. SMTP (Simple Mail Transfer Protocol):Email delivery (TCP 25), unrelated to MIB or device management.
C. NTP (Network Time Protocol):Time synchronization (UDP 123), not MIB-related.
D. TACACS (Terminal Access Controller Access-Control System):Authentication/authorization (TCP 49), not MIB management.
Real-World Context:SNMP misconfiguration led to the 2018 Cisco switch exploits via exposed MIB data.References:CNSP Official Study Guide (Network Monitoring Protocols); RFC 1157 (SNMP).
Which SMB (Server Message Block) network protocol versions are vulnerable to the EternalBlue (MS17-010) Windows exploit?
SMBv1 only
SMBv2 only
SMBv3 only
Both SMBv1 and SMBv2
EternalBlue(MS17-010) is an exploit targeting a buffer overflow in Microsoft’s SMB (Server Message Block) implementation, leaked by the Shadow Brokers in 2017. SMB enables file/printer sharing:
SMBv1 (1980s):Legacy, used in Windows NT/XP.
SMBv2 (2006, Vista):Enhanced performance/security.
SMBv3 (2012, Windows 8):Adds encryption, multichannel.
Vulnerability:
EternalBlue exploits a flaw inSMBv1’s SRVNET driver (srv.sys), allowing remote code execution via crafted packets. Microsoft patched it in March 2017 (MS17-010).
Affected OS: Windows XP to Server 2016 (pre-patch), if SMBv1 enabled.
Proof: WannaCry/NotPetya used it, targeting port 445/TCP.
Version Scope:
SMBv1 Only:The bug resides in SMBv1’s packet handling (e.g., TRANS2 requests). SMBv2/v3 rewrote this code, immune to the specific overflow.
Microsoft: Post-patch, SMBv1 is disabled by default (Windows 10 1709+).
Security Implications:CNSP likely stresses disabling SMBv1 (e.g., via Group Policy) and patching, as EternalBlue remains a threat in legacy environments.
Why other options are incorrect:
B, C:SMBv2/v3 aren’t vulnerable; the flaw is SMBv1-specific.
D:SMBv2 isn’t affected, only SMBv1.
Real-World Context:WannaCry’s 2017 rampage hit unpatched SMBv1 systems (e.g., NHS), costing billions.References:CNSP Official Documentation (Windows Exploits); Microsoft MS17-010 Bulletin.
Copyright © 2021-2025 CertsTopics. All Rights Reserved

