Below is the pseudo-code for the bingo program:

The bingo program contains a data flow anomaly. Which data flow anomaly can be found in this program?
Which of the following elicitation techniques is BEST usedwhen questioning a large number of stakeholders specifically to obtain information for non-functional acceptance criteria?
SELECT ONE OPTION
Which option below describes the BEST approach for testing a Medium risk mission- or safety-critical system?
SELECT ONE OPTION
Consider the following specification:
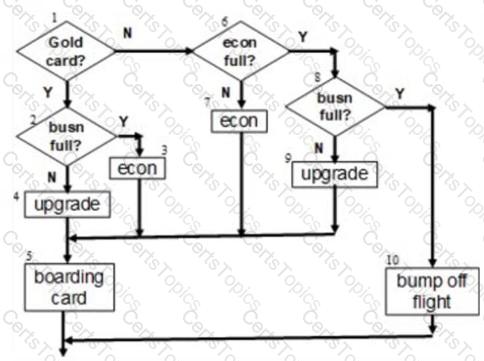
If you are flying with an economy ticket, there is a possibility that you may get upgraded to business class, especially if you hold a gold card in the airline’s frequent flier program. If you don’t hold a gold card, there is a possibility that you will get ‘bumped’ off the flight if it is full when you check in late.
This is shown in the control flow graph below. Note that each box (i.e., statement, decision) has been numbered.
Three tests have been run:
Test 1: Gold card holder who gets upgraded to business class
Test 2: Non-gold card holder who stays in economy
Test 3: A person who is bumped from the flight
What is the level of decision coverage achieved by these three tests?