You have an Azure subscription that contains an Azure key vault. The role assignments for the key vault are shown in the following exhibit.
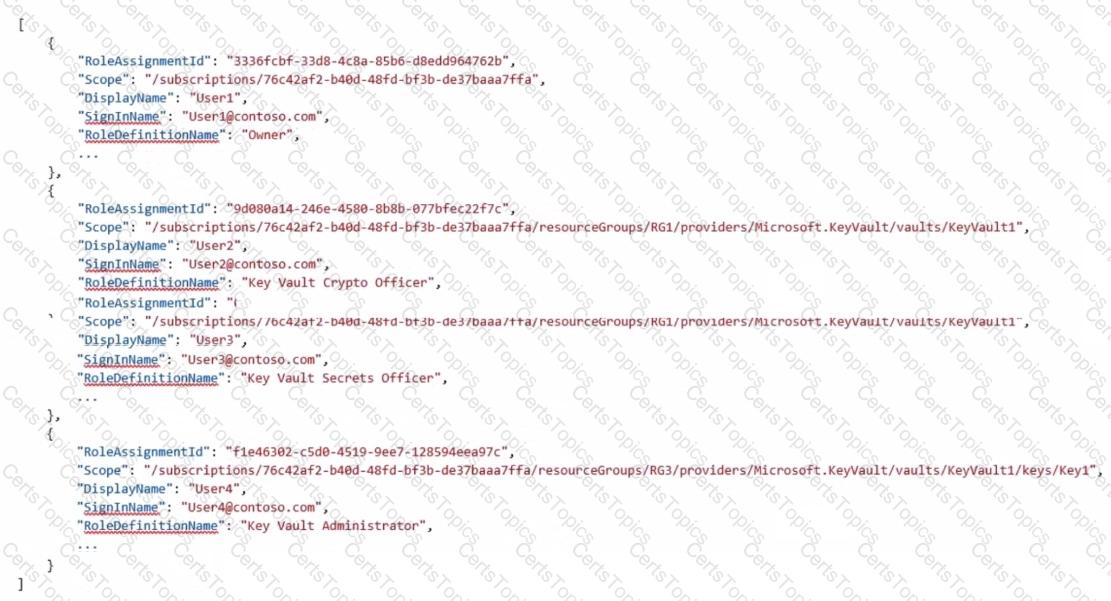
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
You have the Azure key vaults shown in the following table.
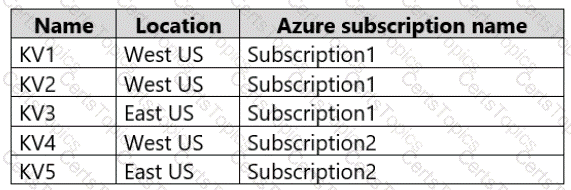
KV1 stores a secret named Secret1 and a key for a managed storage account named Key1.
You back up Secret1 and Key1.
To which key vaults can you restore each backup? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to implement the planned change for VM1 to access storage1.
The solution must meet the technical requirements.
What should you do first?
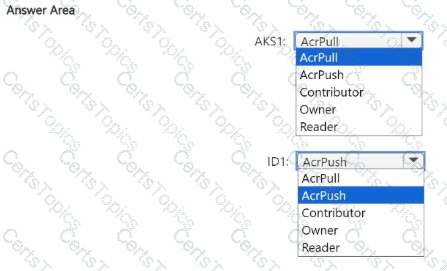
You need to configure the AKS1 and ID1 managed identities to meet the technical requirements. The solution must follow the principle of least privilege.
Which role should you assign to each identity? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.