An engineer configured a bridge domain with the hardware-proxy option for Layer 2 unknown unicast traffic. Which statement is true about this configuration?
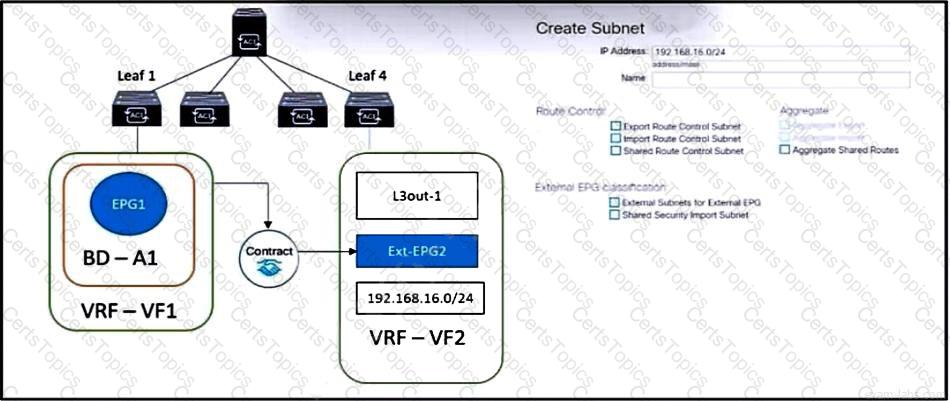
Refer to the exhibit. The external subnet and internal EPG1 must communicate with each other, and the L3Out traffic must leak into the VRF named "VF1". Which configuration set accomplishes these goals?
An engineer must configure VMM domain integration on a Cisco UCS B-Series server that is connected to a Cisco ACI fabric. Drag and drop the products used to create VMM domain from the bottom into the sequence in which they should be implemented at the top. Products are used more than once.
An engineer created a monitoring policy called Test in a Cisco ACI fabric and had to change the severity level of the monitored object Call home source. Which set of actions prevent the event from appearing in event reports?