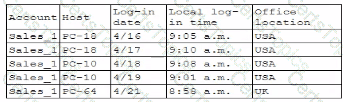
Which of the following is the security engineer most likely doing?
A company that relies on an COL system must keep it operating until a new solution is available Which of the following is the most secure way to meet this goal?
Audit findings indicate several user endpoints are not utilizing full disk encryption During me remediation process, a compliance analyst reviews the testing details for the endpoints and notes the endpoint device configuration does not support full disk encryption Which of the following is the most likely reason me device must be replaced'
An organization has noticed an increase in phishing campaigns utilizingtyposquatting. A security analyst needs to enrich the data for commonly used domains against the domains used inphishing campaigns. The analyst uses a log forwarder to forward network logs to the SIEM. Which of the following would allow the security analyst to perform this analysis?