A global variable called “age” will be created in a program and incremented through the use of a function.
Which of the following data types should be defined with the age variable?
Integer
Float
Double
String
Integer is a data type that can store whole numbers, such as 1, 0, or -2. Integer would be the best data type to use for creating a variable to hold an age value because age is usually expressed as a whole number of years. Float, double, and string are not data types that would be suitable for creating a variable to hold an age value. Float and double are data types that can store decimal or fractional numbers, such as 3.14, 0.5, or -2.75. String is a data type that can store text or characters, such as “Hello”, “A”, or “123”. References: CompTIA IT Fundamentals+ Study Guide: Exam FC0-U61, Second Edition, Chapter 4: Programming Concepts and Data Structures, page 146.
Which of the following actions is the FINAL step in the standard troubleshooting methodology?
Document the solution and cause.
Create a new theory of cause.
Research the problem online.
Implement preventive measures.
The final step in the standard troubleshooting methodology is to document the solution and cause of the problem. This step involves recording the details of the problem, the steps taken to resolve it, the outcome of the solution, and any preventive measures implemented to avoid future occurrences. Documenting the solution and cause can help to create a knowledge base for future reference, improve communication among IT professionals, and facilitate continuous improvement12. References := CompTIA IT Fundamentals (ITF+) Study Guide, 2nd Edition, Chapter 7: Explain the Troubleshooting Methodology3; Troubleshooting Methodology | IT Support and Help Desk | CompTIA4
A systems administrator is setting up a new server using RAID technology. If one hard drive in the array fails,
the data is stored on another drive, preventing data loss. Which of the following business continuity concepts
does this explain?
File backup
Data restoration
Fault tolerance
Restoring access
Fault tolerance is the ability of a system to continue functioning even when one or more components fail. RAID (Redundant Array of Independent Disks) is a technology that uses multiple hard drives to store data in a way that improves performance and reliability. If one hard drive in the RAID array fails, the data can be recovered from another drive without losing any information. This is an example of fault tolerance.
References: CompTIA IT Fundamentals+ Study Guide: Exam FC0-U61, Second Edition, Chapter 6: Infrastructure Concepts, page 240.
An attacker is using subversive tactics to gain the trust of a target in order to obtain entry to a location or access to confidential information. Which of the following best describes this scenario?
Phishing attack
Social engineering
On-path attack
Eavesdropping
The scenario where an attacker is using subversive tactics to gain the trust of a target in order to obtain entry to a location or access to confidential information is best described as social engineering. Social engineering is a type of attack that exploits human psychology and behavior to manipulate people into performing actions or revealing information that benefits the attacker. Social engineering can take various forms, such as phishing, vishing, baiting, quid pro quo, pretexting, or tailgating. Phishing attack is a type of social engineering attack that involves sending fraudulent emails or messages that appear to come from legitimate sources to trick recipients into clicking on malicious links or attachments, or providing personal or financial information. On-path attack is a type of network attack that involves intercepting or modifying data packets that are transmitted between two parties on a network. Eavesdropping is a type of network attack that involves listening to or capturing data packets that are transmitted between two parties on a network. References: The Official CompTIA IT Fundamentals (ITF+) Student Guide (Exam FC0-U61), Chapter 7: Security Concepts1
QUESTIO NO: 166
A technician travels to a data center to review specifications on a new project. Which of the following is the technician most likely to see pertaining to types of operating systems?
A. Mobile device OS
B. Workstation OS
C. Embedded OS
D. Hypervisor OS
Answer: D
A hypervisor OS is the most likely type of operating system that a technician would see pertaining to a data center. A hypervisor OS is an operating system that runs on a host machine and allows multiple guest operating systems to run on virtual machines. A hypervisor OS enables efficient utilization of hardware resources, scalability, and isolation of different workloads in a data center. Examples of hypervisor OS include VMware ESXi, Microsoft Hyper-V, and Citrix XenServer. A mobile device OS is an operating system that runs on a smartphone, tablet, or other portable device. A mobile device OS provides features such as touch screen, wireless connectivity, camera, GPS, and app store. Examples of mobile device OS include Android, iOS, and Windows Phone. A workstation OS is an operating system that runs on a desktop or laptop computer. A workstation OS provides features such as graphical user interface, file management, multitasking, and networking. Examples of workstation OS include Windows 10, macOS, and Linux. An embedded OS is an operating system that runs on a special-purpose device or system that performs a specific function. An embedded OS provides features such as real-time performance, low power consumption, and minimal user interface. Examples of embedded OS include Windows Embedded, Linux Embedded, and QNX. References: The Official CompTIA IT Fundamentals (ITF+) Student Guide (Exam FC0-U61), Chapter 4: Operating System Fundamentals1
QUESTIO NO: 167
The process of determining the source of an issue during troubleshooting is called:
A. researching.
B. sourcing.
C. diagnosing.
D. triaging.
Answer: C
The process of determining the source of an issue during troubleshooting is called diagnosing. Diagnosing is the third step in the troubleshooting process, after gathering information and determining if anything has changed. Diagnosing involves analyzing the symptoms and possible causes of the problem, testing hypotheses, and identifying the root cause of the problem. Researching is the process of finding relevant information or resources to help solve a problem during troubleshooting. Researching can be done before or after diagnosing, depending on the availability and reliability of the information or resources. Sourcing is not a term used in troubleshooting, but it may refer to the process of finding or obtaining materials or components for a product or service. Triaging is not a term used in troubleshooting, but it may refer to the process of prioritizing problems or tasks based on their urgency or importance. References: The Official CompTIA IT Fundamentals (ITF+) Student Guide (Exam FC0-U61), Chapter 2: IT Concepts and Terminology1
QUESTIO NO: 168
A corporate network just implemented a 60-day password-warning banner. Which of the following is most likely going to happen in 60 days?
A. Password reset
B. Password expiration
C. Password reuse
D. Password Implementation
Answer: B
The most likely thing that will happen in 60 days after implementing a 60-day password-warning banner is password expiration. A password-warning banner is a message that appears on the screen when a user logs in to a system or network, informing them of how many days are left before their password expires. A password expiration policy is a security measure that requires users to change their passwords periodically, usually every 30 to 90 days. This policy helps to prevent unauthorized access or compromise of passwords by hackers or malicious insiders. Password reset is the process of changing or creating a new password for a user account when the user forgets their password or wants to change it for security reasons. Password reset can be done by the user themselves or by an administrator, depending on the system or network settings. Password reset does not necessarily happen in 60 days after implementing a 60-day password-warning banner, unless the user forgets their password or chooses to change it before it expires. Password reuse is the practice of using the same password for multiple user accounts or systems. Password reuse is not recommended as it increases the risk of compromise if one of the accounts or systems is breached by hackers or malicious insiders. Password reuse does not necessarily happen in 60 days after implementing a 60-day password-warning banner, unless the user chooses to use their old password for their new password after it expires. Password implementation is not a term used in security, but it may refer to the process of creating or enforcing password policies for user accounts or systems. Password implementation does not necessarily happen in 60 days after implementing a 60-day password-warning banner, unless there are changes in the password policies that require users to comply with them. References: The Official CompTIA IT Fundamentals (ITF+) Student Guide (Exam FC0-U61), Chapter 7: Security Concepts1
QUESTIO NO: 169
Given this example:
FEB8077911AB12TB
Which of the following is being represented?
A. MAC address
B. String
C. Hexadecimal
D. Unicode
Answer: C
The example FEB8077911AB12TB is being represented as hexadecimal. Hexadecimal is a number system that uses 16 symbols to represent values from 0 to 15. The symbols are 0-9 for values from 0 to 9, and A-F for values from 10 to 15. Hexadecimal is often used to represent binary data in a more compact and readable form, such as MAC addresses, color codes, or memory addresses. A MAC address is a unique identifier for a network interface card (NIC) that consists of 12 hexadecimal digits separated by colons or dashes. A string is a sequence of characters that can be used to store text or other data types. A string can contain hexadecimal digits, but it can also contain other symbols or characters. Unicode is a standard for encoding characters from different languages and scripts into binary data. Unicode can use hexadecimal digits to represent characters, but it also requires other symbols or codes to indicate the encoding scheme. References: The Official CompTIA IT Fundamentals (ITF+) Student Guide (Exam FC0-U61), Chapter 2: IT Concepts and Terminology1
QUESTIO NO: 170
Given the following lines:
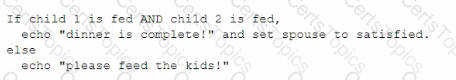
This is an example of:
A. a flowchart.
B. looping.
C. an assembly.
D. pseudocode.
Answer: D
The example given is an example of pseudocode. Pseudocode is a way of writing the logic of a program or an algorithm in a simplified and informal language that resembles natural language or code, but does not follow the syntax or rules of a specific programming language. Pseudocode is often used to plan, design, or explain a program or an algorithm before writing the actual code. A flowchart is a way of representing the logic of a program or an algorithm using symbols and arrows that show the sequence of steps and decisions. A flowchart is often used to visualize, analyze, or document a program or an algorithm. Looping is a way of repeating a set of statements or actions in a program or an algorithm until a certain condition is met. Looping is often used to perform iterative tasks, such as counting, searching, or sorting. An assembly is a way of writing the instructions of a program or an algorithm in a low-level language that corresponds to the machine code of a specific processor. An assembly is often used to create programs that run fast and efficiently, but it is difficult to read and write. References: The Official CompTIA IT Fundamentals (ITF+) Student Guide (Exam FC0-U61), Chapter 8: Software Development Concepts1
QUESTIO NO: 171
A systems administrator is setting up an output device that supports both USB and network capability. Which of the following devices is the administrator most likely installing?
A. Scanner
B. Camera
C. SSD
D. Printer
Answer: D
The device that the administrator is most likely installing is a printer. A printer is an output device that supports both USB and network capability, meaning that it can be connected to a computer or a network using either a USB cable or a wireless or wired network connection. A printer can produce hard copies of documents, images, or other data on paper or other media. A scanner is an input device that supports both USB and network capability, meaning that it can be connected to a computer or a network using either a USB cable or a wireless or wired network connection. A scanner can capture images or text from paper or other media and convert them into digital data. A camera is an input device that supports both USB and network capability, meaning that it can be connected to a computer or a network using either a USB cable or a wireless or wired network connection. A camera can capture images or videos and store them as digital data. An SSD stands for Solid State Drive, which is a type of storage device that supports both USB and network capability, meaning that it can be connected to a computer or a network using either a USB cable or a wireless or wired network connection. An SSD uses flash memory chips to store data persistently even when the power is turned off. References: The Official CompTIA IT Fundamentals (ITF+) Student Guide (Exam FC0-U61), Chapter 1: IT Fundamentals1
QUESTIO NO: 172
Given the following information:
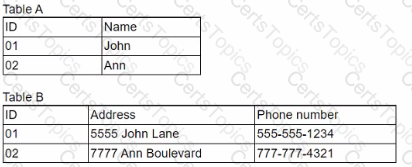
Which of the following is descriptive of both tables?
A. The database uses a flat file structure.
B. The database uses SQL.
C. The data most likely exists within a relational database.
D. The data is corrupted and is being shown as two sets.
Answer: C
The description that best fits both tables is that the data most likely exists within a relational database. A relational database is a type of database that organizes data into tables, which consist of rows and columns. Each table represents an entity, such as customers, orders, products, etc., and each row represents an instance of that entity, such as customer 01, order 02, product 03, etc. Each column represents an attribute of that entity, such as name, address, phone number, etc. Tables can be related to each other by using common columns, such as ID, which can act as primary keys or foreign keys. A primary key is a column that uniquely identifies each row in a table, such as ID in Table A and Table B. A foreign key is a column that references the primary key of another table, such as ID in Table B referencing ID in Table A. A relational database uses SQL (Structured Query Language) to create, manipulate, and query data in tables. The database does not use a flat file structure, which is another type of database that stores data in plain text files with fixed fields and records. A flat file structure does not support relationships between tables or SQL queries. The data is not corrupted and shown as two sets, but rather separated into two tables for normalization purposes. Normalization is the process of organizing data in tables to reduce redundancy and improve efficiency and integrity. References: The Official CompTIA IT Fundamentals (ITF+) Student Guide (Exam FC0-U61), Chapter 6: Database Fundamentals1
QUESTIO NO: 173
Which of the following actions is most likely associated with database use?
A. Creating diagrams
B. Querying
C. File sharing
D. Printing
Answer: B
The action that is most likely associated with database use is querying. Querying is the process of retrieving data from a database based on certain criteria or conditions. Querying allows users to access specific information from large amounts of data stored in tables. Querying can be done using SQL (Structured Query Language), which is a standard language for interacting with relational databases. SQL queries can perform various operations, such as selecting, inserting, updating, deleting, or joining data from tables. Creating diagrams is not an action that is associated with database use, but rather with software development or design. Creating diagrams can help visualize the structure, logic, or flow of a program or an algorithm. Examples of diagrams include flowcharts, UML diagrams, ER diagrams, etc. File sharing is not an action that is associated with database use, but rather with network use. File sharing is the process of allowing users to access or transfer files over a network. File sharing can be done using various protocols, such as FTP, SMB, NFS, etc. Printing is not an action that is associated with database use, but rather with output device use. Printing is the process of producing hard copies of documents, images, or other data on paper or other media using a printer. References: The Official CompTIA IT Fundamentals (ITF+) Student Guide (Exam FC0-U61), Chapter 6: Database Fundamentals1
QUESTIO NO: 174
A programming construct that is most beneficial tor organizing a program's data and behavior is:
A. an object.
B. a licensing agreement.
C. a query.
D. a constant.
Answer: A
The programming construct that is most beneficial for organizing a program’s data and behavior is an object. An object is a programming construct that encapsulates data and behavior into a single unit. An object can have attributes, which are variables that store data related to the object, and methods, which are functions that perform actions related to the object. An object can be created from a class, which is a blueprint or template that defines the attributes and methods of the object. An object can also inherit attributes and methods from another class, which is called a superclass or a parent class. An object can also override or modify attributes and methods inherited from another class, which is called a subclass or a child class. An object can also interact with other objects by sending or receiving messages. Object-oriented programming (OOP) is a paradigm that uses objects as the main building blocks of a program. OOP allows programmers to create modular, reusable, and maintainable code that models real-world entities and scenarios. A licensing agreement is not a programming construct, but rather a legal document that defines the terms and conditions for using a software product or service. A licensing agreement can specify the rights and responsibilities of the software vendor and the user, such as the scope of use, the duration of use, the payment terms, the warranty terms, etc. A query is not a programming construct, but rather a statement that retrieves data from a database based on certain criteria or conditions. A query can be written using SQL (Structured Query Language), which is a standard language for interacting with relational databases. A constant is not a programming construct that organizes data and behavior, but rather a variable that stores a single value of any data type that does not change during the execution of a program. A constant can be used to store values that are fixed or known in advance, such as PI = 3.14 or TAX_RATE = 0.15. References: The Official CompTIA IT Fundamentals (ITF+) Student Guide (Exam FC0-U61), Chapter 8: Software Development Concepts1
QUESTIO NO: 175
A help desk technician loads a browser-based ticketing system, but when navigating to the queue, the technician realizes that another employee's queue is being accessed. Which of the following explains the issue?
A. The previous user's session Is cached.
B. The proxy settings were misconfigured.
C. The application is not compatible with the browser.
D. The browser was opened in private mode.
Answer: A
The issue that explains why the technician is accessing another employee’s queue is that the previous user’s session is cached. Caching is the process of storing data temporarily in a memory or disk for faster access or reuse. Caching can improve the performance and efficiency of a browser-based application, but it can also cause security or privacy issues if the data is not cleared or updated properly. The previous user’s session may have been cached by the browser or the application, and the technician may have accessed the same URL or credentials without logging out or clearing the cache. The proxy settings were not misconfigured, as this would not affect the access to another employee’s queue, but rather the access to the internet or the application server. The proxy settings are the configuration options that determine how a browser connects to a proxy server, which is an intermediary server that acts as a gateway between the browser and the internet or the application server. The proxy server can provide security, anonymity, or caching functions for the browser. The application is not incompatible with the browser, as this would not affect the access to another employee’s queue, but rather the functionality or appearance of the application. The application compatibility is the degree to which an application works correctly and efficiently with a specific browser or operating system. The browser was not opened in private mode, as this would not affect the access to another employee’s queue, but rather prevent the caching of data. The private mode is a feature that allows a browser to browse the internet without storing any browsing history, cookies, cache, or other data on the device. References: The Official CompTIA IT Fundamentals (ITF+) Student Guide (Exam FC0-U61), Chapter 5: Infrastructure Concepts1
QUESTIO NO: 176
Employees must use a badge to enter and exit the building. Each time the badge is used, a log entry is created and stored to record who has entered and exited the building. Which of the following best describes what the log entries provide?
A. Automation
B. Accounting
C. Authorization
D. Authentication
Answer: B
The log entries that are created and stored when employees use their badges to enter and exit the building provide accounting. Accounting is a security function that records and tracks user activities and events on a system or network. Accounting can provide evidence of user actions, such as authentication, authorization, access, modification, or deletion of data or resources. Accounting can also provide information for billing, auditing, or reporting purposes. Accounting can be implemented using log files, audit trails, or monitoring tools. Automation is not a security function, but rather a process of using technology to perform tasks or operations without human intervention. Automation can improve productivity, efficiency, accuracy, or reliability of a system or network. Automation can be implemented using scripts, programs, or tools. Authorization is not a security function that records and tracks user activities and events, but rather a security function that grants or denies user access to data or resources based on their identity and permissions. Authorization can ensure that users only access what they are allowed to access on a system or network. Authorization can be implemented using access control lists (ACLs), role-based access control (RBAC), or mandatory access control (MAC). Authentication is not a security function that records and tracks user activities and events, but rather a security function that verifies user identity based on credentials, such as passwords, tokens, biometrics, etc. Authentication can ensure that users are who they claim to be on a system or network. Authentication can be implemented using single-factor authentication (SFA), multi-factor authentication (MFA), or single sign-on (SSO). References: The Official CompTIA IT Fundamentals (ITF+) Student Guide (Exam FC0-U61), Chapter 7: Security Concepts1
QUESTIO NO: 177
A technician has received multiple reports about a media player, which is located in a waiting room, turning on and off at various times of the day. The technician replaces the power adapter and turns the player back on. Which of the following should the technician do next?
A. Verify there is full system functionality.
B. Document the findings/lessons learned.
C. implement the solution.
D. Research the knowledge base.
Answer: A
The next step that the technician should do after replacing the power adapter and turning on the media player is verifying there is full system functionality. Verifying there is full system functionality is the fourth step in the troubleshooting process, after diagnosing and resolving the problem. Verifying there is full system functionality involves testing and confirming that the problem has been fixed and that no new problems have been introduced by the solution. Documenting the findings/lessons learned is not the next step after replacing the power adapter and turning on the media player, but rather the last step in the troubleshooting process, after verifying there is full system functionality. Documenting the findings/lessons learned involves creating a record of the problem and its solution for future reference or training purposes. Implementing the solution is not the next step after replacing the power adapter and turning on the media player, but rather part of resolving the problem in the third step of troubleshooting process. Implementing solution involves applying the chosen solution to fix problem. Researching knowledge base is not next step after replacing power adapter and turning on media player, but rather an optional step that can be done before diagnosing problem in troubleshooting process. Researching knowledge base involves finding relevant information resources to help solve problem. References: The Official CompTIA IT Fundamentals (ITF+) Student Guide (Exam FC0-U61), Chapter 2: IT Concepts and Terminology
Copyright © 2021-2025 CertsTopics. All Rights Reserved

