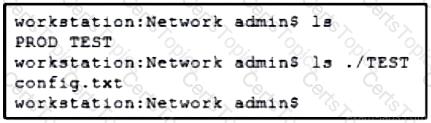
Refer to the exhibit. A network engineer must copy the “config.txt” file from directory TEST to directory PROD. The copied file must also be renamed into “current.txt”. Which command must be used to accomplish these tasks?
How does edge computing analyze sensitive data in the context of privacy control?
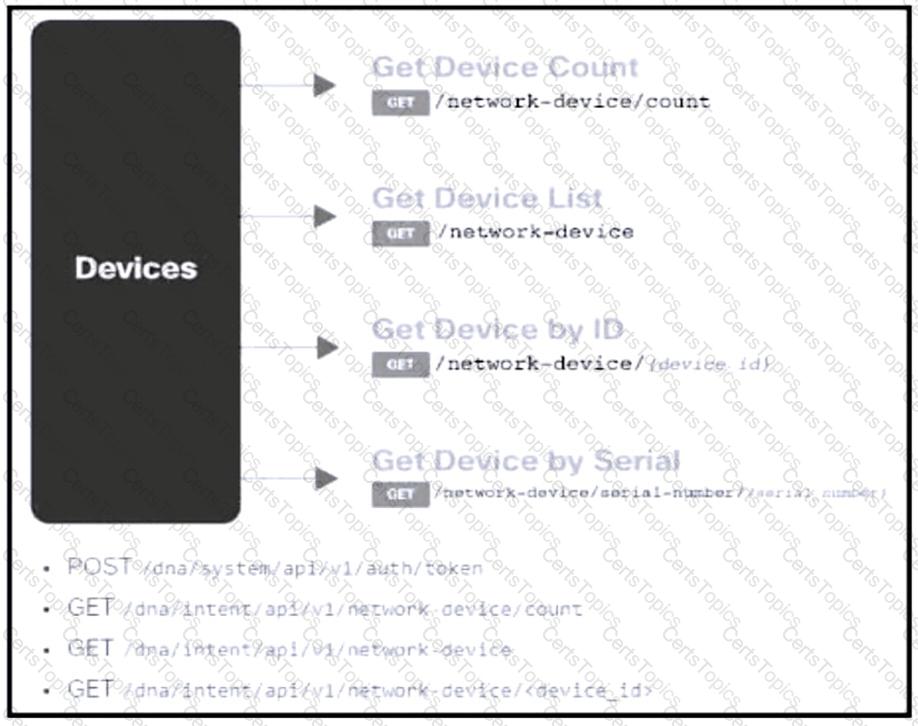
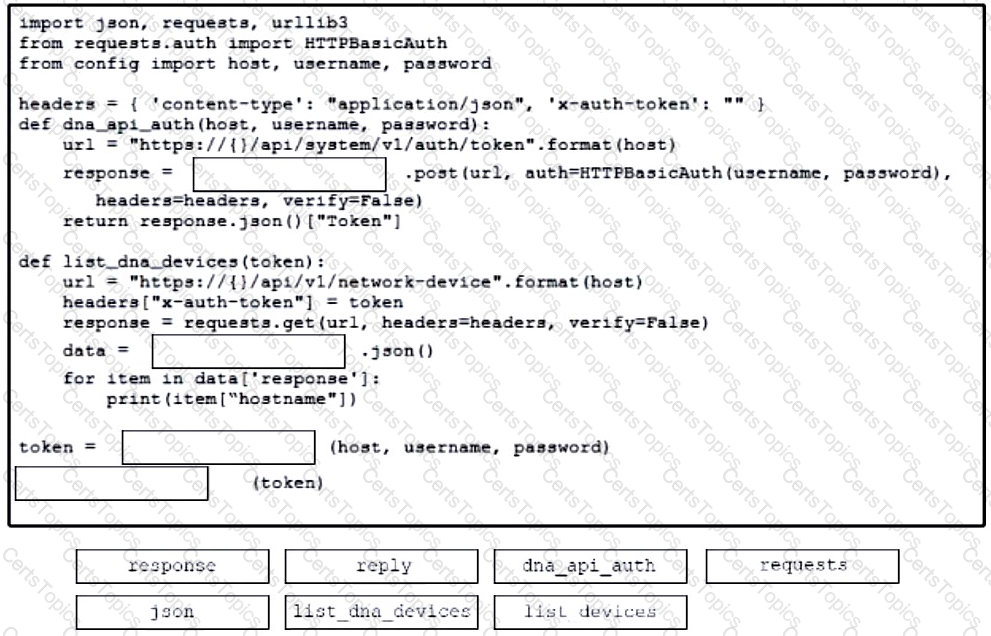
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a request that generates a security token and gets a list of network devices. Not all options are used.
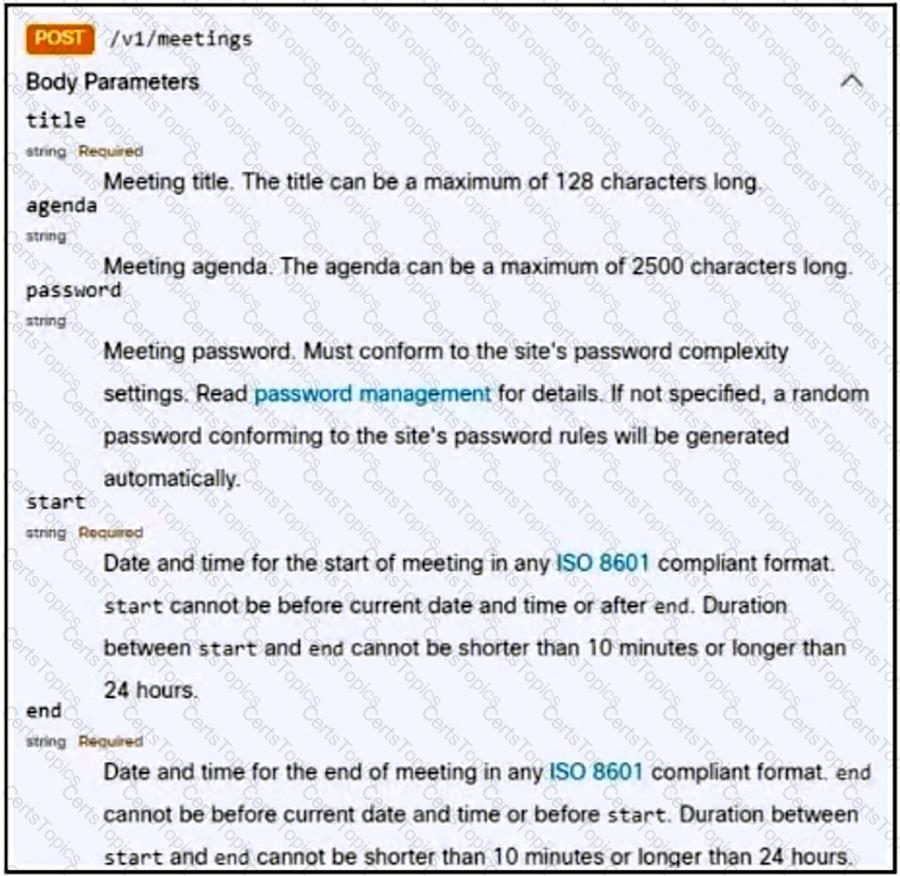
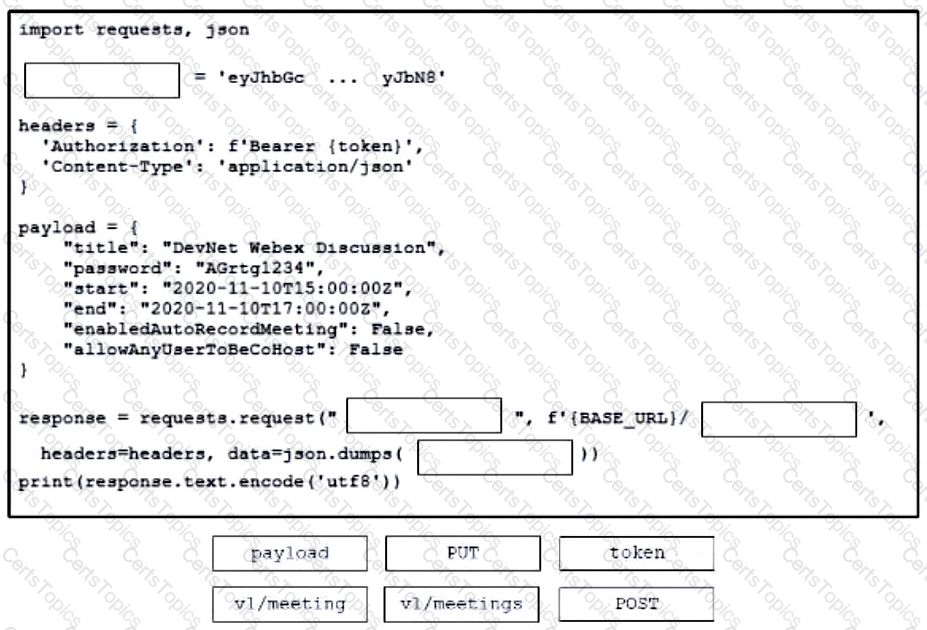
Refer to the exhibit. A bespoke meeting booking system must be integrated with Cisco Webex so that meetings are created automatically. Drag and drop the code from the bottom onto the box where the code is missing to create a sample meeting. Not all options are used.