EMC Related Exams
D-SF-A-24 Exam







A .R.T.I.E.has an evolving need, which was amplified during the incidents. Their complex and dispersed IT environments have thousands of users, applications, and resources to manage. Dell found that the existing Identity and Access Management was limited in its ability to apply expanding IAM protection to applications beyond the core financial and human resource management application.A .R.T.I.E.also did not have many options for protecting their access especially in the cloud.A .R.T.I.E.were also not comfortable exposing their applications for remote access.
Dell recommended adopting robust IAM techniques like mapping out connections between privileged users and admin accounts, and the use multifactor authentication.
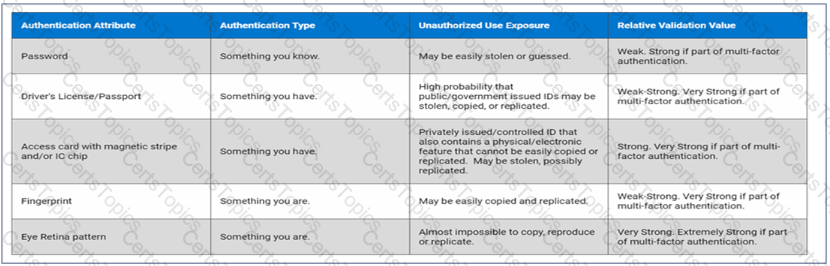
The Dell Services team suggest implementing a system that requires individuals to provide a PIN and biometric information to access their device.
Which type of multifactor authentication should be suggested?
A Zero Trust security strategy is defined by which of the primary approaches?
Dell Services team cannot eliminate all risks, but they can continually evaluate the resilience and preparedness ofA .R.T.I.E.by using the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF).
Match the core NIST CSF component functions with the description that the Dell Services team would have recommended toA .R.T.I.E.
