in which step of the Palo Alto Networks Five-Step Zero Trust Methodology would an organization's critical data, applications, assets, and services (DAAS) be identified?
Which are the three mandatory components needed to run Cortex XDR? (Choose three.)
Which three categories are identified as best practices in the Best Practice Assessment tool? (Choose three.)
A customer is starting to understand their Zero Trust protect surface using the Palo Alto Networks Zero Trust reference architecture.
What are two steps in this process? (Choose two.)
There are different Master Keys on Panorama and managed firewalls.
What is the result if a Panorama Administrator pushes configuration to managed firewalls?
What are two ways to manually add and remove members of dynamic user groups (DUGs)? (Choose two)
What are the three possible verdicts in WildFire Submissions log entries for a submitted sample? (Choose four.)
Which CLI command will allow you to view latency, jitter and packet loss on a virtual SD-WAN interface?
A)
B)

C)

D)

An administrator wants to justify the expense of a second Panorama appliance for HA of the management layer.
The customer already has multiple M-100s set up as a log collector group. What are two valid reasons for deploying Panorama in High Availability? (Choose two.)
What are two advantages of the DNS Sinkholing feature? (Choose two.)
What are two benefits of the sinkhole Internet Protocol (IP) address that DNS Security sends to the client in place of malicious IP addresses? (Choose two.)
A company has deployed the following
• VM-300 firewalls in AWS
• endpoint protection with the Traps Management Service
• a Panorama M-200 for managing its VM-Series firewalls
• PA-5220s for its internet perimeter,
• Prisma SaaS for SaaS security.
Which two products can send logs to the Cortex Data Lake? (Choose two).
Access to a business site is blocked by URL Filtering inline machine learning (ML) and
considered as a false-positive.
How should the site be made available?
Which two configuration items are required when the NGFW needs to act as a decryption broker for multiple transparent bridge security chains? (Choose two.)
A customer is looking for an analytics tool that uses the logs on the firewall to detect actionable events on the network. They require something to automatically process a series of related threat events that, when combined, indicate a likely compromised host on their network or some other higher level conclusion. They need to pinpoint the area of risk, such as compromised hosts on the network, allows you to assess the risk and take action to prevent exploitation of network resources.
Which feature of PAN-OS can you talk about to address their requirement to optimize their business outcomes?
Which Palo Alto Networks security component should an administrator use to and NGFW policies to remote users?
In PAN-OS 10.0 and later, DNS Security allows policy actions to be applied based on which three domains? (Choose three.)
Which task would be identified in Best Practice Assessment tool?
In an HA pair running Active/Passive mode, over which interface do the dataplanes communicate?
Which two features are key in preventing unknown targeted attacks? (Choose two)
A prospective customer currently uses a firewall that provides only Layer 4
inspection and protections. The customer sees traffic going to an external destination, port 53, but cannot determine what Layer 7 application traffic is going over that port
Which capability of PAN-OS would address the customer's lack of visibility?
Which three mechanisms are valid for enabling user mapping? (Choose three.)
Which Palo Alto Networks pre-sales tool involves approximately 4 hour interview to discuss a customer's current security posture?
Which two products can send logs to the Cortex Data Lake? (Choose two.)
The firewall includes predefined reports, custom reports can be built for specific data and actionable tasks, or predefined and custom reports can be combined to compile information needed to monitor network security.
The firewall provides which three types of reports? (Choose three.)
What is an advantage of having WildFire machine learning (ML) capability Inline on the firewall?
Palo Alto Networks publishes updated Command-and-Control signatures. How frequently should the related signatures schedule be set?
Match the WildFire Inline Machine Learning Model to the correct description for that model.
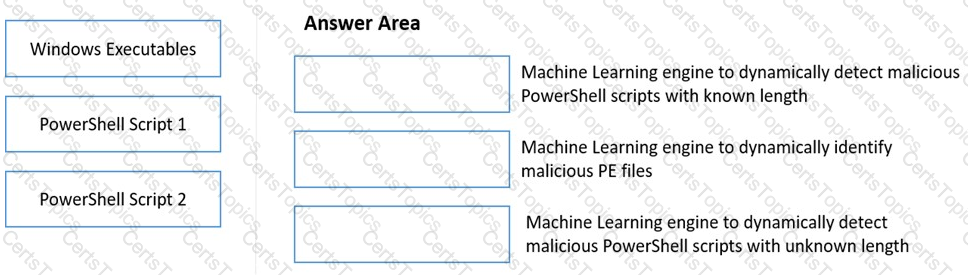
WildFire machine learning (ML) for portable executable (PE) files is enabled in the antivirus profile and added to the appropriate firewall rules in the profile. In the Palo Alto Networks WildFire test av file, an attempt to download the test file is allowed through.
Which command returns a valid result to verify the ML is working from the command line.
Which two features are found in a Palo Alto Networks NGFW but are absent in a legacy firewall product? (Choose two.)
Which two of the following does decryption broker provide on a NGFW? (Choose two.)
Which statement applies to Palo Alto Networks Single Pass Parallel Processing (SP3)?
Which two components must be configured within User-ID on a new firewall that has been implemented? (Choose two.)
A price-sensitive customer wants to prevent attacks on a Windows Virtual Server. The server will max out at 100Mbps but needs to have 45.000 sessions to connect to multiple hosts within a data center
Which VM instance should be used to secure the network by this customer?
Which two tabs in Panorama can be used to identify templates to define a common base configuration? (Choose two.)
Which component is needed for a large-scale deployment of NGFWs with multiple Panorama Management Servers?
Which Security profile on the Next-Generation Firewall (NGFW) includes Signatures to protect against brute force attacks?
A customer worried about unknown attacks is hesitant to enable SSL decryption due to privacy
and regulatory issues. How does the platform address the customer’s concern?
A packet that is already associated with a current session arrives at the firewall.
What is the flow of the packet after the firewall determines that it is matched with an existing session?
Decryption port mirroring is now supported on which platform?
XYZ Corporation has a legacy environment with asymmetric routing. The customer understands that Palo Alto Networks firewalls can support asymmetric routing with redundancy. Which two features must be enabled to meet the customer's requirements? (Choose two.)