Review the exhibit.
What is the purpose of the configuration page shown Ii the exhibit?
Your customer has deployed the Netskope client to secure their Web traffic. Recently, they have enabled Cloud Firewall (CFW) to secure all outbound traffic for their endpoints. Through a recent acquisition, they must secure all outbound traffic at several remote offices where they have access to the local security stack (routers and firewalls). They cannot install the Netskope client.
You notice that your Netskope client icon has a red dot and see "Disabled due to error" when hovering the mouse over the icon. What are two reasons for this message? (Choose two.)
What is the purpose of the file hash list in Netskope?
Your company needs to keep quarantined files that have been triggered by a DLP policy. In this scenario, which statement Is true?
Your customer implements Netskope Secure Web Gateway to secure all Web traffic. While they have created policies to block certain categories, there are many new sites available dally that are not yet categorized. The customer's users need quick access and cannot wait to put in a request to gain access requiring a policy change or have the site's category changed.
To solve this problem, which Netskope feature would provide quick, safe access to these types of sites?
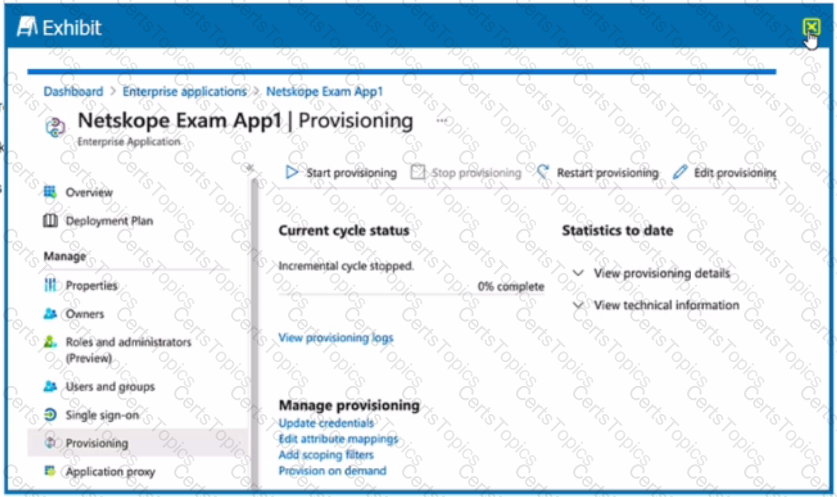
Review the exhibit.
Referring to the exhibit, which three statements are correct? (Choose three.)
You discover the ongoing use of the native Dropbox client in your organization. Although Dropbox is not a corporate-approved application, you do not want to prevent the use of Dropbox. You do, however, want to ensure visibility into its usage.
You want the ability to perform automated remediation of misconfigurations on GitHub, Microsoft 365, Salesforce, ServiceNow, and Zoom.
After deploying the Netskope client to a number of devices, users report that the Client status indicates "Admin Disabled". User and gateway information is displayed correctly in the client configuration dialog
Why are clients installing in an "Admin Disabled" state in this scenario?
Review the exhibit.
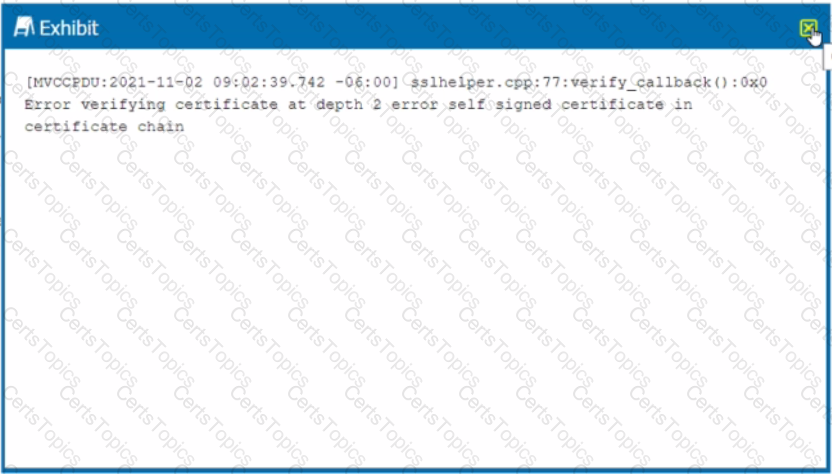
While diagnosing an NPA connectivity issue, you notice an error message in the Netskope client logs.
Referring to the exhibit, what does this error represent?
Review the exhibit.
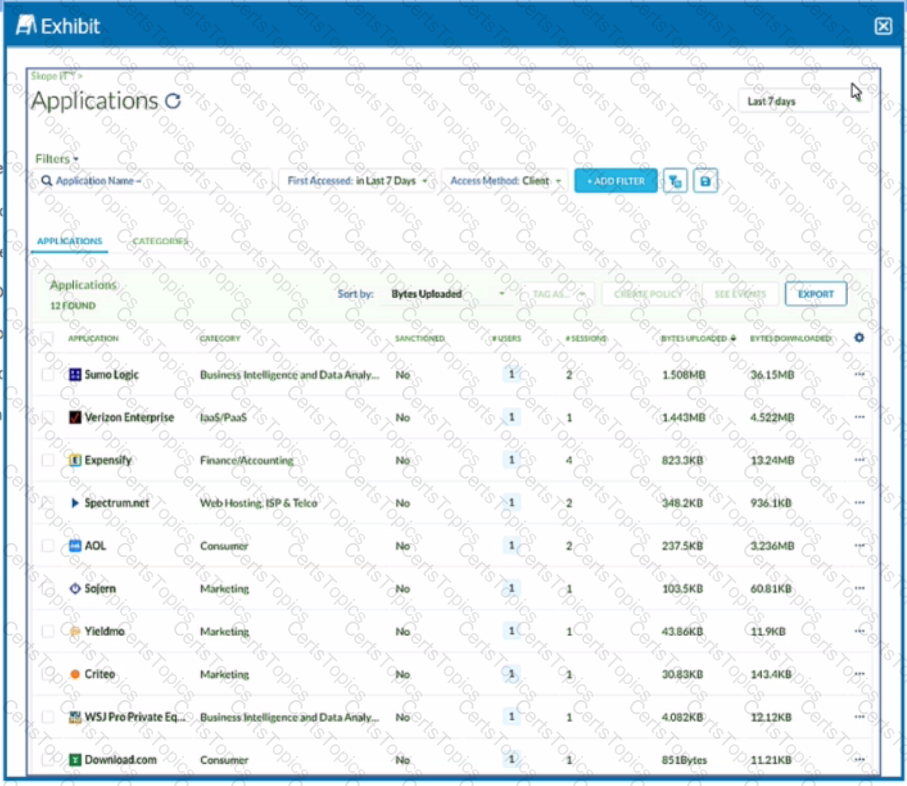
You want to discover new cloud applications in use within an organization.
Referring to the exhibit, which three methods would accomplish this task? (Choose three.)
You are testing policies using the DLP predefined identifier "Card Numbers (Major Networks; all)." No DLP policy hits are observed.
A customer wants to deploy the Netskope client on all their employee laptops to protect all Web traffic when users are working from home. However, users are required to work from their local offices at least one day per week. Management requests that users returning to the office be able to transparently leverage the local security stack without any user intervention.
Which two statements are correct in this scenario? (Choose two.)
You want to reduce false positives by only triggering policies when contents of your customer database are uploaded to Dropbox. Your maximum database size is 2 MB. In this scenario, what are two ways to accomplish this task? (Choose two.)
You created the Netskope application in your IdP for user provisioning and validated that the API Integration settings are correct and functional. However, you are not able to push the user groups from the IdP into your Netskope tenant.
A customer wants to use Netskope to prevent PCI data from leaving the corporate sanctioned OneDrive instance. In this scenario. which two solutions would assist in preventing data exfiltration? (Choose two.)
Your customer has some managed Windows-based endpoints where they cannot add any clients or agents. For their users to have secure access to their SaaS application, you suggest that the customer use Netskope's Explicit Proxy.
Which two configurations are supported for this use case? (Choose two.)
A city uses many types of forms, including permit applications. These forms contain personal and financial information of citizens. Remote employees download these forms and work directly with the citizens to complete them. The city wants to be able to identify and monitor the specific forms and block the employees from downloading completed forms.
Which feature would you use to accomplish this task?
Your customer is using a virtual desktop infrastructure (VDI) for their support engineers. Multiple users will be logging into the same device, and they want to detect activities for each user.
You are an administrator writing Netskope Real-time Protection policies and must determine proper policy ordering.
Which two statements are true in this scenario? (Choose two.)
You are integrating Netskope tenant administration with an external identity provider. You need to implement role-based access control. Which two statements are true about this scenario? (Choose two.)
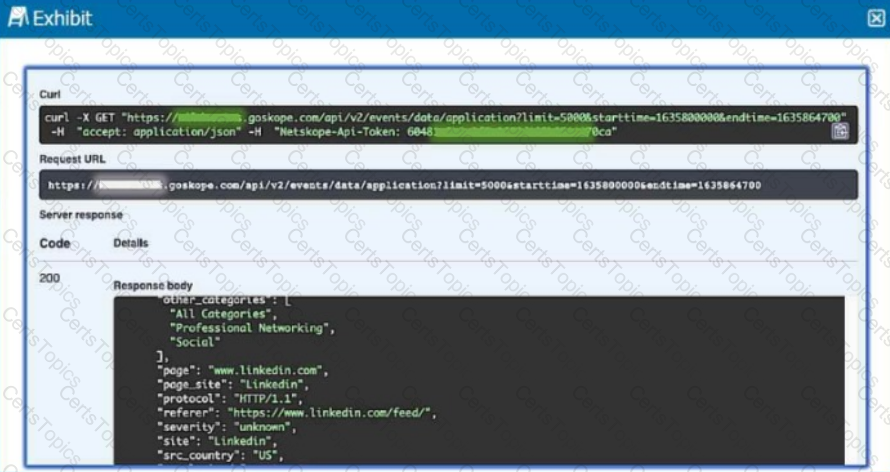
Review the exhibit.
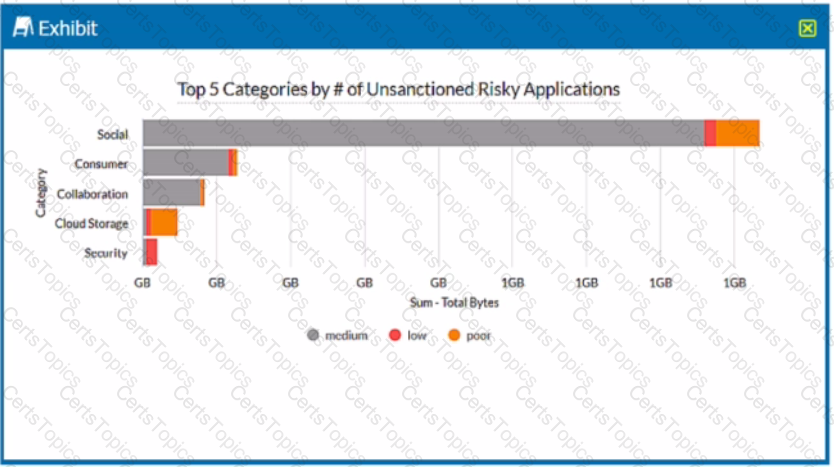
A security analyst needs to create a report to view the top five categories of unsanctioned applications accessed in the last 90 days. Referring to the exhibit, what are two data collections in Advanced Analytics that would be used to create this report? (Choose two.)
Your company wants to deploy Netskope using a tunnel because you have a mixture of device operating systems. You also do not want to enable encryption because you want to maximize bandwidth.
What are three methods to deploy a Netskope client? (Choose three.)
You are troubleshooting private application access from a user's computer. The user is complaining that they cannot access the corporate file share; however, the private tunnel seems to be established. You open the npadebuglog.log file in a text editor and cannot find any reference to the private application.
To which three event types does Netskope's REST API v2 provide access? (Choose three.)