In ZTP networking, which of the following addresses can be delivered by a DHCP server? (Select All that Apply)
The figure shows an incomplete VXLAN packet format.
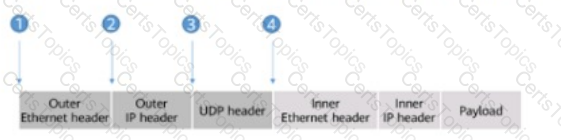
Which of the following positions should the VXLAN header be inserted into so that the packet format is complete?
Which of the following statements are true about IP address planning for a DC? (Select All that Apply)
In the spine-leaf DCN architecture, the border leaf node and service leaf node can be deployed on the same device.
To allow access to a VXLAN network, you need to configure service access points on devices. There are two access modes: Layer ? sub-interface and binding. (Enter the acronym in uppercase letters.)
Which of the following can be used as the conditions for microsegmentation to divide EPGs? (Select All that Apply)
Which of the following technologies are Layer 4 load balancing technologies? (Select All that Apply)
Assume that a VXLAN tunnel is monitored on a Huawei CE series switch and that the tunnel status is Down or the tunnel fails to be dynamically established. In this scenario, which of the following statements are true about how to check the cause of the fault? (Select All that Apply)
Which of the following statements are false about heartbeat link faults in an M-LAG? (Select All that Apply)
Which of the following statements is false about VXLAN tunnel establishment?
In network overlay, both endpoints of a VXLAN tunnel are physical switches.
Which of the following technologies are open-source virtualization technologies? (Select All that Apply)
How many rollback levels does Huawei's iMaster NCE-Fabric support?
Which of the following can be deployed to enhance DC reliability? (Select All that Apply)
Both M-LAG and stacking technologies can overcome the disadvantages of traditional DCNs. However, M-LAG is a better choice to ensure 24/7 service continuity.
A hypervisor virtualizes the following physical resources: memory, and input/output (I/O) resources. (Enter the acronym in uppercase letters.)
In EVPN, Type 5 routes are used only by hosts on a VXLAN network to access external networks.
A VXLAN tunnel is identified by a pair of VTEP IP addresses. During VXLAN tunnel establishment, the local and remote VTEPs attempt to obtain each other's IP addresses. If the VTEP IP addresses are reachable to each other at Layer 3, a VXLAN tunnel can be established.