The Nginx application is deployed on a Linux host. By checking Nginx logs, O&M engineers can obtain the complete URL information submitted by users and determine whether the Linux host is under SQL injection attacks.
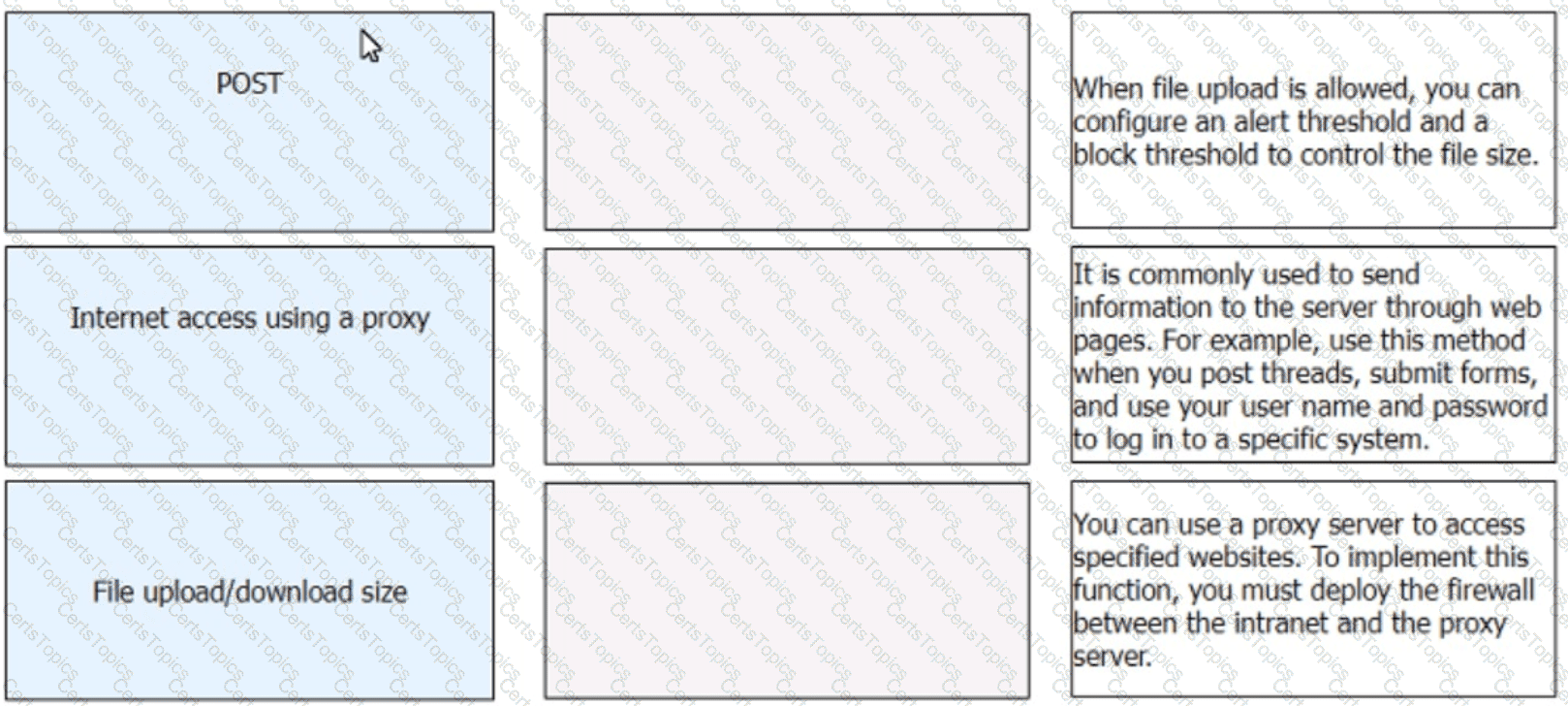
Match the HTTP control items with the corresponding descriptions.
Which of the following statements is false about hot standby networking?(Select All that Apply)
Which of the following statements is true about the outgoing traffic in the firewall virtual system?
: 52 DRAG DROP
Arrange the steps of the bandwidth management process on firewalls in the correct sequence.

Authentication rules configured on iMaster NCE-Campus support multiple matching conditions, such as matching account information, SSID information, and terminal IP address ranges, so that different authentication rules can be executed for different users.
IPsec VPN does not support encapsulation of non-IP unicast packets.
Which of the following actions can be performed when the firewall identifies file anomalies?(Select All that Apply)
When gateways are connected using GRE over IPsec, the IPsec encapsulation mode must be tunnel mode.
Which of the following operations can be performed to harden the Windows operating system?(Select All that Apply)
Which of the following conditions can be matched by PBR?(Select All that Apply)
In quota control policies, which of the following can be set for users?(Select All that Apply)
Before configuring DDoS attack defense, you must configure different thresholds for defense against different types of attacks. Each threshold can be considered an upper limit for normal network traffic. When the rate of traffic exceeds the pre-configured threshold, the firewall considers it to be attack traffic and takes a corresponding action to defend against it.
During deployment of Portal authentication, an authentication-free rule profile needs to be configured to ensure Portal pages can be opened on authentication terminals. To achieve this purpose, the following traffic needs to be permitted in the authentication-free rule profile: DNS resolution traffic of user terminals, traffic from user terminals for accessing Portal pages, and traffic from user terminals to the RADIUS server.
Which of the following statements is false about HTTP behavior?
When an IPsec VPN is established in aggressive mode, AH+ESP can be used to encapsulate packets in NAT traversal scenarios.
Which of the following statements is false about Eth-Trunk?(Select All that Apply)
Predefined URL categories on Huawei firewalls reside in the URL category database delivered with the device and do not need to be manually loaded.